🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Data breaches and financial fraud frequently trace back to manipulation rather than technical failure. Deceptive communication often succeeds where direct system intrusion would be difficult.
Stolen credentials, unauthorized transfers, internal data leaks, and account takeovers commonly follow persuasive interaction. Email scams, fake executive requests, support impersonation, and physical access tricks continue to bypass strong technical safeguards.
Digital communication channels have expanded the scale and speed of these attacks across industries. Risk reduction depends on disciplined verification practices and security controls that limit the damage caused by human error.
Social engineering is a category of cyberattack that uses deception to obtain confidential information or unauthorized access. Access is achieved through influence and persuasion rather than through exploitation of software vulnerabilities.
Cybersecurity frameworks recognize social engineering as a human-centric threat model. Attack execution typically occurs through structured interaction designed to appear legitimate.
Risk assessment models treat this attack method separately from traditional hacking techniques. Defensive strategies must therefore address behavioral exposure alongside network and system security.
Social engineering works through a calculated process designed to gain trust before triggering a harmful action.
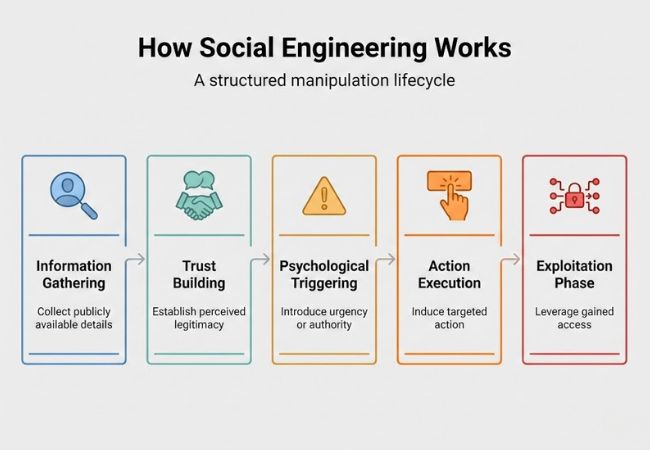
Human behavior follows predictable psychological patterns that attackers deliberately leverage during manipulation.
Social engineering appears in several distinct forms, each using a different delivery method while relying on manipulation.
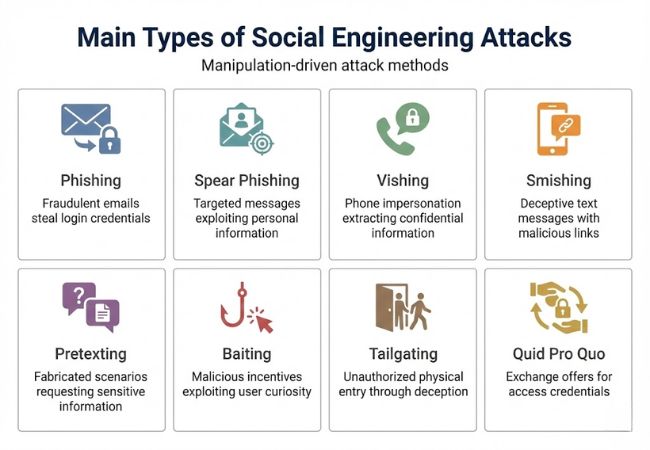
Phishing uses deceptive emails that mimic trusted brands or internal teams to push recipients toward malicious links, fake login pages, or credential capture forms. Attackers often borrow real logos, familiar tones, and urgent language to make the request feel routine inside normal business communication.
New Zealand’s National Cyber Security Centre (NCSC) recorded 355 reports of phishing and credential harvesting in Q3 2025, showing how consistently this tactic appears in incident reporting pipelines. Even with awareness programs in place, phishing remains a primary intrusion vector because it targets everyday email behavior.
Spear phishing targets a specific person or role using personal context such as job title, current projects, vendors, or reporting lines to make the message believable. Instead of broad distribution, attackers focus on precision to increase the probability of credential theft or payment diversion.
Canada’s Canadian Anti-Fraud Centre (CAFC) reported over $43 million in losses linked to spear phishing in 2025, reflecting the financial impact of highly tailored deception. Personalization lowers suspicion and increases compliance because the message aligns with legitimate operational workflows.
Vishing relies on voice calls to impersonate banks, IT support desks, law enforcement, or regulatory bodies while applying urgency and authority. Conversations are structured to extract one-time passwords, remote access approval, or immediate fund transfers.
Japan’s National Police Agency reported that 79.1% of special fraud cases in the first half of 2025 began with phone contact (10,458 cases). High phone-first prevalence demonstrates how real-time pressure and direct conversation remain effective persuasion tools.
Smishing delivers fraudulent prompts through SMS or messaging platforms, typically framed as delivery updates, security alerts, refunds, or account problems. Short links and time-sensitive language exploit fast mobile interactions and reduced on-screen context.
India’s Department of Telecommunications noted that in December 2025 the DLT system blocked more than 7.5 crore SMS and voice calls per day under filtering and consent mechanisms. Blocking at that scale highlights the volume of suspicious messaging traffic linked to text-based deception.
Pretexting builds a fabricated narrative that justifies a sensitive request, such as identity confirmation, compliance verification, or access approval. The strength of the scenario determines whether the target views the interaction as routine rather than suspicious.
Singapore Police reported 1,762 government official impersonation scam cases in the first half of 2025, with losses of about $126.5 million. Authority-driven impersonation demonstrates how a convincing backstory can override skepticism and trigger high-value transfers.
Baiting uses attractive offers such as discounted products, giveaways, free downloads, or exclusive opportunities to trigger curiosity or financial temptation. Engagement begins voluntarily because the victim believes there is something to gain.
Australia’s ACCC Scamwatch recorded more than 6,300 financial loss reports linked to shopping scams in the first half of 2025. Offer-based fraud shows how perceived reward functions as the psychological entry point before financial or data compromise occurs.
Tailgating involves unauthorized individuals following authorized personnel into restricted areas by leveraging politeness, urgency, or familiarity. Physical presence is used to bypass badge checks and access controls that depend on human enforcement.
The UK’s Cyber Security Breaches Survey 2025 found that 2% of businesses experienced unauthorized access to files or networks by people outside the organization. Weak physical verification can enable digital compromise once an attacker gains internal positioning.
Quid pro quo exchanges assistance or perceived benefit for access, credentials, or remote control of a system. Fake technical support interactions are common examples where help becomes the leverage point.
A 2025 U.S. Attorney’s Office case involving a computer support scam resulted in approximately $328,573 returned to the victim. Support-themed fraud illustrates how promised service is converted into financial extraction or unauthorized access.
A classic example involves attackers impersonating IT support to request login credentials. By referencing internal systems and speaking with confidence, the attacker persuades the employee to share passwords or authentication codes.
Historically, Kevin Mitnick demonstrated how psychological manipulation could bypass advanced security controls. Access was gained not through code exploitation, but through convincing employees to disclose confidential information.
Modern incidents include voice impersonation scams in which criminals mimic a company executive and request an urgent wire transfer. Finance teams that fail to verify the request through a secondary channel may authorize payments before realizing the deception.
Social engineering creates business risk by turning normal workplace communication into a pathway for financial and operational damage.
Fraudulent wire transfers, vendor payment redirection, and payroll manipulation can result in immediate monetary damage. Recovery is often difficult once funds are transferred to external accounts.
Compromised credentials may allow attackers to access customer records, internal documents, or intellectual property. Data leaks can disrupt operations and damage long-term business relationships.
Clients and partners may lose confidence after a security incident becomes public. Brand credibility can decline even if technical systems were not directly breached.
Unauthorized access to sensitive information may trigger compliance investigations and legal scrutiny. Fines and reporting requirements can extend the impact well beyond the initial event.
Social engineering has advanced in sophistication as digital infrastructure and communication technologies have expanded.
Automated language tools now produce highly convincing phishing emails at scale. Personalized wording increases credibility and lowers detection rates.
Audio manipulation technology enables criminals to imitate executives or trusted contacts. Urgent financial requests delivered through cloned voices appear authentic.
Video fabrication tools create realistic executive appearances during virtual meetings. Visual confirmation reduces suspicion and accelerates fraudulent approvals.
Public platforms reveal job roles, reporting structures, and ongoing projects. Attackers use this data to craft believable and targeted scenarios.
Email, SMS, phone calls, and messaging apps are combined within coordinated attacks. Reinforced communication across channels builds perceived legitimacy.
Corporate accounts are impersonated or hijacked to request payment transfers. Vendor relationships and invoice processes are frequently exploited.
Third-party vendors and service providers are used as entry points into larger organizations. Indirect access allows attackers to bypass stronger primary defenses.
Phishing is a specific attack technique, while social engineering is the broader category that includes multiple manipulation-based methods.
Personal security against social engineering depends on disciplined verification habits and awareness of manipulation tactics.
Unexpected financial or credential requests should always be confirmed through a separate, trusted communication channel. Direct phone calls to official numbers reduce the risk of responding to fraudulent messages.
Multi-factor authentication adds an extra layer of protection beyond passwords. Compromised credentials alone become insufficient for account access.
Oversharing job roles, travel plans, or internal responsibilities on social media increases exposure. Publicly available details often help attackers craft convincing scenarios.
Urgent messages should trigger caution rather than immediate action. Taking time to evaluate tone, sender details, and context prevents impulsive responses.
Unique, complex passwords reduce the damage of credential reuse. Password managers help maintain secure storage without memorization risks.
Organizational defense against social engineering requires structured policies, technical safeguards, and continuous employee training.
Regular training programs educate employees about manipulation tactics and real-world attack scenarios. Simulated phishing campaigns reinforce learning through practical exposure.
Role-based access limits the amount of information and system privileges available to each employee. Reduced access scope minimizes damage if credentials are compromised.
Advanced email security solutions detect suspicious links, spoofed domains, and malicious attachments. Filtering systems reduce the number of fraudulent messages reaching employees.
Mandatory multi-factor authentication protects critical systems even if passwords are exposed. Additional identity verification steps block unauthorized access attempts.
Clear reporting channels allow employees to escalate suspicious activity immediately. Documented response procedures help contain threats before they spread.
Third-party partners should follow defined security standards and verification protocols. External access points often become indirect entry routes for attackers.
An effective defense strategy should combine behavioral safeguards with technical protection rather than relying on a single control layer.
Employee education must go beyond one-time sessions and include ongoing reinforcement. Regular simulations help measure awareness and identify vulnerable departments.
Multi-factor authentication should protect email systems, financial platforms, and administrative accounts. Access barriers reduce the impact of stolen credentials.
Monitoring tools should detect unusual login patterns, spoofed domains, and suspicious communication behavior. Early detection shortens response time and limits exposure.
Formal procedures must exist for approving financial transfers or sensitive information requests. Secondary confirmation channels prevent fraudulent authorization.
Employees need simple and direct ways to report suspicious activity. Quick escalation helps contain threats before broader compromise occurs.
Vendor access should follow defined security standards and verification practices. External partners often become overlooked entry points for attackers.
Social engineering continues to challenge organizations and individuals because it targets behavior rather than technology. Technical defenses alone cannot eliminate risk when persuasion becomes the primary attack method.
Sustainable protection depends on awareness, verification discipline, and layered security controls that address both human and technical exposure. Strengthening everyday decision-making remains one of the most effective ways to reduce long-term security risk.
