🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Cyber attacks do not always generate visible disruption. Attackers execute a backdoor attack by embedding hidden access inside systems, enabling persistent, unauthorized control without detection. This method increases in frequency as organisations expand digital infrastructure, integrate third-party software, and enable remote access environments.
The scale of this threat became evident during the ASUS ShadowHammer incident. Kaspersky confirmed that over 1 million devices received a compromised software update through ASUS’s official update mechanism. The attack demonstrated how concealed access propagates through trusted distribution channels and remains undetected for extended periods.
Understanding what backdoor attacks are, how they operate, why they create operational risk, and how to prevent them reduces exposure to persistent and covert system compromise.
A backdoor attack is a cyberattack in which an attacker creates or uses a hidden access point to enter a system without normal authentication. This hidden access bypasses security controls, allowing attackers to enter systems without detection.
In cybersecurity, a backdoor means a concealed method of access that exists outside approved entry methods. Concealed access avoids login checks, security monitoring, and user awareness.
Backdoor attacks focus on long-term access rather than immediate damage. This Persistent access allows attackers to return repeatedly, control systems, steal data, or prepare future attacks without needing to break in again.
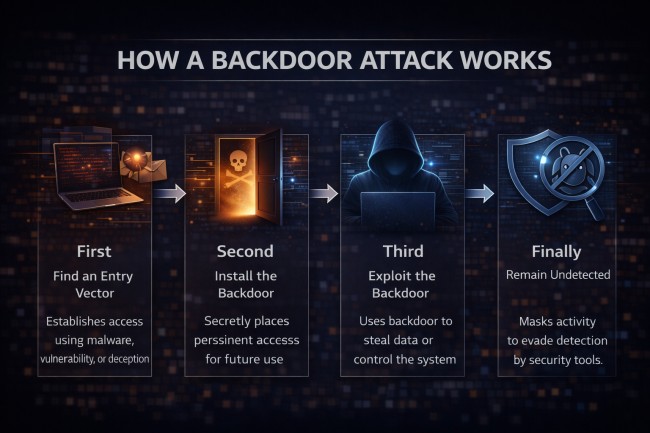
A backdoor attack works by secretly placing hidden access inside a system and using it repeatedly over time. The process starts when an attacker gains initial entry through malware, software flaws, stolen credentials, or compromised updates.
After gaining entry, the attacker creates or installs a backdoor. This backdoor may be a hidden user account, a malicious service, a modified program, or a concealed command interface that avoids normal security checks.
Once installed, the backdoor remains hidden and persistent. The attacker can reconnect at any time without logging in normally, allowing ongoing access for data theft, system control, or preparation for future attacks.
A backdoor attack has clear characteristics that explain why it is difficult to detect and dangerous over time.
A backdoor establishes covert access that is not visible to system administrators. This access operates silently in the background and does not appear in standard user activity logs.
Backdoors circumvent standard authentication mechanisms. Attackers gain entry without valid credentials, multi-factor authentication, or formal access approvals.
A backdoor is designed to survive reboots, updates, and password resets. This persistence enables attackers to maintain long-term access without redeploying malware.
Backdoors enable attackers to reconnect from external networks at any time. This remote access allows repeated system control without physical presence or user interaction.
Backdoors are engineered to avoid detection by security tools. They may hide processes, obfuscate traffic, or mimic legitimate system behavior to remain undetected.
Backdoors provide continuous system-level control. This prolonged access supports data exfiltration, system manipulation, lateral movement, and preparation for advanced attacks.
These are common entry points that expose systems long enough for attackers to install persistent backdoors.
Backdoor access is often introduced through malware delivered via malicious downloads or harmful email attachments. Once executed, the malware installs hidden access mechanisms that attackers later use to regain entry.
Backdoors can be embedded within trusted third-party software. When organizations deploy compromised updates or applications, the malicious code is installed silently, enabling unauthorized access without immediate suspicion.
Unpatched or misconfigured software vulnerabilities provide initial entry points. After exploitation, attackers deploy backdoors to retain access even after the original flaw is remediated.
Exposed or insecure web applications and APIs can allow attackers to upload web shells or hidden scripts. These components function as persistent backdoors within the server environment.
Exposed remote access services, such as RDP or SSH, increase the risk of intrusion. Once attackers gain access—often through weak authentication—they install backdoors to ensure continued control.
Compromised credentials enable attackers to log in legitimately. After gaining access, they establish backdoors to maintain persistence without depending on stolen credentials.
Excessive permissions, default settings, open ports, or insider misuse can create unintended access paths. These weaknesses allow attackers to deploy backdoors with minimal resistance.
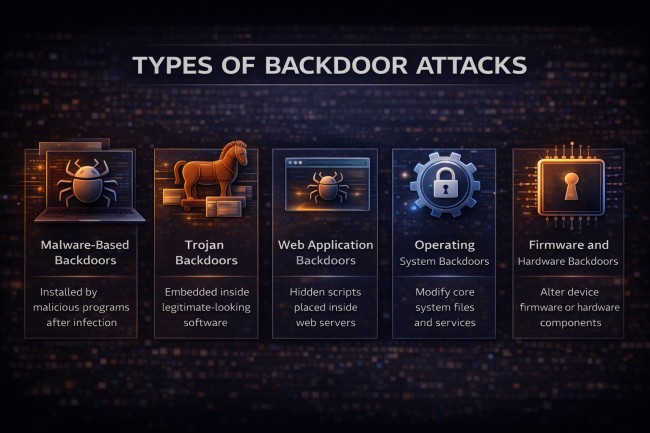
Backdoor attacks are classified by where the hidden access is placed and how long it can persist inside a system. Here are the main types of backdoor attacks:
Malware-based backdoors are deployed after a successful infection. The malicious program establishes a covert communication channel that enables attackers to issue commands, exfiltrate data, or control the system remotely. These backdoors often include persistence mechanisms that survive system reboots.
Trojan backdoors are embedded within software that appears legitimate. Once installed, the application secretly creates hidden access paths, allowing attackers to connect without triggering standard security alerts.
Web application backdoors are implanted within websites or web servers. Attackers upload web shells or concealed scripts that enable remote command execution through HTTP or browser-based access. These backdoors remain active as long as the malicious files persist on the server
Operating system backdoors alter core system components such as services, system files, or privileged user accounts. This deep-level modification provides sustained and often privileged access that can survive patches and routine updates.
Firmware and hardware backdoors operate below the operating system layer. By modifying device firmware or hardware components, attackers establish access that persists even after system reinstallation. These backdoors are among the most difficult to detect and remediate.
Backdoor attacks are often confused with other cyber threats; however, backdoor attacks differ from other cyber threats because their primary goal is persistent hidden access, not immediate execution or damage.
This distinction becomes clear when comparing purpose, persistence, and control.
A malware infection focuses on running malicious code to steal data, disrupt systems, or spread further. A backdoor attack focuses on creating a secret access path that remains usable over time. Malware can exist without persistence, while a backdoor is designed for repeated re-entry.
A remote access trojan provides continuous live control over a system once installed. A backdoor provides a concealed way to enter the system whenever needed. RATs act as active tools, while backdoors function as silent entry points.
A rootkit hides malicious activity by concealing files, processes, or system changes. A backdoor ensures access by bypassing authentication. Rootkits focus on stealth, while backdoors focus on guaranteed entry. Both are often used together but serve different roles.
These Real-world backdoor attacks show how hidden access can remain active for long periods and cause widespread damage.
In 2017, attackers linked to a state-sponsored group compromised the software update system of CCleaner. By inserting a backdoor into a legitimate update, the attackers reached more than 2.2 million users worldwide. Large technology companies were selectively targeted, allowing attackers to maintain silent access inside corporate networks for months before discovery.
In 2020, a highly sophisticated backdoor attack was uncovered in the SolarWinds Orion platform. Attackers, attributed to a nation-state group, modified software updates to include a hidden backdoor. Government agencies and major enterprises were affected, leading to long-term espionage risks and large-scale security overhauls.
In 2014, attackers compromised Sony Pictures Entertainment by planting backdoors inside internal systems. The attackers used this access to steal confidential data, delete files, and disrupt operations. The incident caused extended downtime, reputational damage, and major financial losses.
In 2021, attackers exploited vulnerabilities in Microsoft Exchange servers and installed web shell backdoors. Organizations across the world, including businesses and government entities, were affected. The backdoors enabled repeated access, ongoing data theft, and follow-on attacks long after the initial exploitation.
Backdoor attacks are dangerous because they create persistent, unauthorized access to systems. Persistent access enables repeated entry, increasing the risk of data theft, manipulation, and operational disruption over time.
It evade detection by bypassing authentication controls and blending into legitimate processes. Sustained access supports lateral movement and privilege escalation, expanding compromise across networks and complicating full remediation.
Backdoor attacks are detected by carefully looking for hidden access that stays active even when systems appear normal. Because backdoors are designed to stay unnoticed, detection focuses on long-term changes, repeated behavior, and patterns that do not match normal system use.
Backdoor attacks are found by watching for what should not exist, what keeps returning, and what quietly avoids attention, rather than by looking for obvious damage.
Backdoor attacks are prevented by stopping hidden access from being created and by making sure no secret access remains inside systems. Prevention works best when security steps are followed continuously, not just once. Here are the best tactics:
Secure software installation means downloading and installing programs only from trusted and official sources. Attackers often hide backdoors inside fake or modified software. When software is verified before installation, hidden access is blocked before it can enter the system.
Patching keeps systems safe by fixing known security weaknesses. Attackers search for outdated systems because they are easier to break into. When updates are applied on time, attackers lose common ways to enter and install backdoors.
Strong authentication protects who can enter systems. Using more than just a password, such as a code or device confirmation, makes it much harder for attackers to log in. Limited access reduces the chance of attackers creating hidden entry points.
Least-privilege access means users and programs get only the access they need. If an account is compromised, limited permissions prevent attackers from installing or keeping backdoors in the system.
Continuous monitoring watches systems all the time, not just during checks. When unusual activity appears, such as unexpected file changes or hidden connections, teams can act quickly before a backdoor becomes permanent.
This protection ensures that important system files and settings do not change without approval. Backdoors often hide in startup files or services. Monitoring these areas helps catch hidden access early.
Remote access services allow systems to be controlled from a distance. If left open or weakly protected, attackers can use them to install backdoors. Securing or limiting these services reduces that risk.
Security audits involve regularly checking systems for unknown accounts, hidden files, or suspicious programs. Even after an attack is fixed, audits ensure no backdoors were left behind.
User awareness reduces mistakes that attackers exploit. When users recognize phishing emails and unsafe downloads, attackers lose easy ways to gain access and install backdoors.
