🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
A passive attack is a cybersecurity method where unauthorized actors observe data flows or system activity without altering the target environment. The purpose centers on information acquisition rather than disruption, manipulation, or control.
Observation typically occurs across communication paths where data moves between systems or users. Operational continuity remains intact, allowing monitoring to blend into normal activity without raising immediate suspicion.
Exposure of sensitive information defines the primary risk associated with passive attacks rather than direct system damage. Detection becomes difficult due to the absence of modification, reinforcing the importance of safeguarding data confidentiality at the transmission level.
Passive attacks work by positioning an attacker in a location where data can be observed as it moves between communicating parties. Access is gained to communication paths, transmission channels, or broadcast mediums without interacting with the source or destination.
Data observation focuses on capturing signals, packets, or communication patterns during transmission rather than accessing stored systems. Interception occurs silently, ensuring that the original data reaches its destination without interruption or alteration.
Long-term monitoring enables attackers to build an information profile based on collected data or communication behavior. Absence of interference allows the activity to persist unnoticed, increasing exposure risks as more data is observed over time.
Passive attacks can be grouped into categories based on how information is observed or inferred during transmission. These classifications represent the most commonly recognized observation methods rather than an exhaustive list of all possible variations.
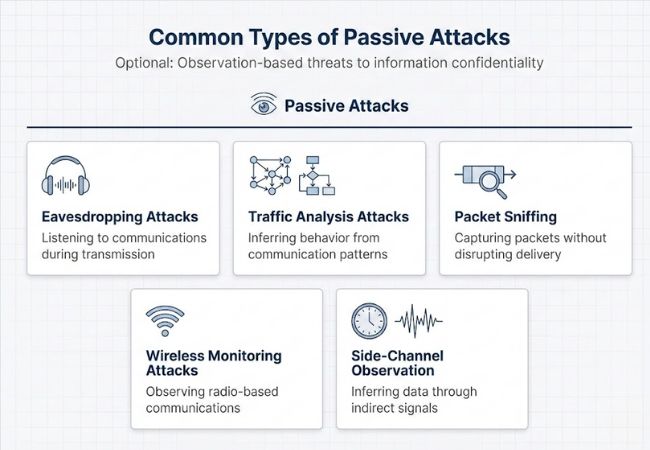
Eavesdropping attacks involve listening to communications as they occur across wired or wireless channels. Information exposure depends on the sensitivity of the intercepted data and the level of protection applied during transmission.
Traffic analysis attacks focus on communication patterns instead of content, such as timing, frequency, and data volume. Operational behavior can often be inferred even when messages remain encrypted.
Packet sniffing captures data packets traveling across a network without interrupting delivery. Readable information may be exposed from unencrypted traffic, while encrypted packets still reveal metadata.
Wireless monitoring targets radio-based communications, including Wi-Fi or other broadcast signals. Open or weakly secured wireless environments increase the visibility of transmitted data.
Side-channel observation relies on indirect information leakage, such as timing variations or signal characteristics. Inference occurs without accessing the actual data content or systems directly.
Passive and active attacks differ primarily in whether the attacker only observes information or actively alters systems, data, or operations.
Passive attacks are difficult to detect because observation occurs without altering system behavior, data, or network operations.
Security controls commonly rely on detecting changes such as unauthorized access, file alterations, or configuration updates. Absence of modification removes these indicators, allowing observation activity to remain unnoticed.
Captured data travels alongside legitimate communications without interruption or delay. Monitoring activity blends into routine traffic patterns, making malicious intent difficult to distinguish.
Intrusion detection systems focus on anomalies rather than silent observation. Passive monitoring provides few measurable signals for automated tools to flag or investigate.
Long-term data collection can occur without triggering alerts or errors. Prolonged exposure increases the volume of information gathered while maintaining operational invisibility.
Encrypted communications often conceal content but not observation activity. Presence of encryption may reduce visibility into intent rather than eliminate passive monitoring entirely.
Minimal resource usage prevents noticeable performance degradation. Lack of system strain removes secondary indicators that could otherwise signal suspicious activity.
Passive attacks commonly appear in everyday digital environments where data is transmitted, broadcast, or shared without direct system interaction.
Unsecured public Wi-Fi networks allow attackers to observe data transmitted between connected devices. Sensitive information can be exposed when traffic lacks adequate protection.
Wireless communications broadcast signals that can be monitored within range. Poorly secured wireless setups increase the visibility of transmitted data.
Internal or external network monitoring points can be misused for unauthorized observation. Data flows may be inspected without affecting system performance or availability.
Communication metadata such as timing, frequency, and volume can be observed without accessing content. Behavioral patterns often emerge from prolonged observation.
Older systems frequently rely on outdated or unencrypted protocols. Data transmitted through such environments becomes easier to observe passively.
Cloud or shared network environments increase exposure surfaces for transmitted data. Observation risks rise when multiple users rely on the same underlying infrastructure.
Passive attacks threaten data security because sensitive information can be exposed continuously without detection or operational disruption. Silent access allows confidentiality risks to grow over time while systems appear unaffected.
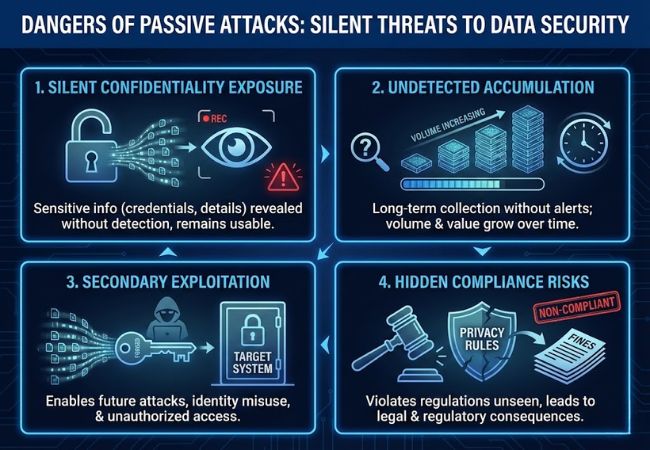
Unauthorized observation directly compromises data confidentiality by revealing communications, credentials, or sensitive operational details. Information gathered passively often remains usable long after interception.
Lack of visible impact enables long-term data collection without triggering alerts. Extended exposure increases both the volume and strategic value of intercepted information.
Observed data can support identity misuse, unauthorized access, or more targeted attacks. Intelligence gathered passively often serves as a foundation for future security incidents.
Hidden data exposure can violate privacy and data protection requirements even without service outages. Regulatory and legal consequences may emerge once the breach is identified.
Reducing the risk of passive attacks requires limiting data visibility during transmission and strengthening confidentiality controls across communication paths.
Encryption protects information in transit by rendering intercepted data unreadable. Strong cryptographic protocols reduce the value of observed communications even when monitoring occurs.
Use of secure communication standards minimizes exposure across networks and applications. Proper protocol configuration ensures data exchanges follow confidentiality-focused practices.
Segmentation limits how far observed data can travel within an environment. Isolating sensitive systems reduces the scope and impact of potential observation.
Continuous monitoring helps identify unusual observation patterns over time. Behavioral analysis supports early awareness even when no direct modification occurs.
Informed users reduce exposure by avoiding unsecured networks and unsafe communication practices. Awareness programs strengthen the human layer of confidentiality protection.
Passive attacks rarely draw attention because systems continue to operate as expected while information is quietly observed. That lack of visibility is what makes them especially relevant in environments where data constantly moves across networks and communication channels.
Reducing exposure depends less on detecting attackers and more on limiting what can be learned through observation. Strong confidentiality controls, disciplined communication practices, and awareness of transmission risks remain essential for protecting data over time.
Passive attacks cannot be completely prevented because any data transmitted across a network can potentially be observed. Strong encryption and secure communication practices significantly reduce the risk and impact.
Passive attacks do not require direct access to systems or applications. Observation typically occurs at communication paths where data is transmitted between parties.
Passive attacks are not less dangerous than active attacks, even though they cause no immediate disruption. Long-term data exposure often enables credential misuse, surveillance, or future targeted attacks.
Encryption does not stop all passive attacks, but it prevents attackers from reading intercepted data. Communication patterns and metadata may still be observable despite encryption.
