🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Key Takeaways:
A software firewall is a network security application designed to control inbound and outbound traffic on a specific computer, server, or virtual machine. Firewall software operates within the operating system or application environment to evaluate network connections in real time.
Software-based firewalls focus on device-level protection rather than acting as a network-wide perimeter defense. Computer firewall software enforces security policies by analyzing traffic sources, destinations, ports, protocols, and application behavior.
Granular traffic control makes software firewalls effective for endpoint security, server protection, and cloud-based systems. Modern cybersecurity environments rely on software firewalls to secure individual workloads, remote devices, and distributed infrastructure.
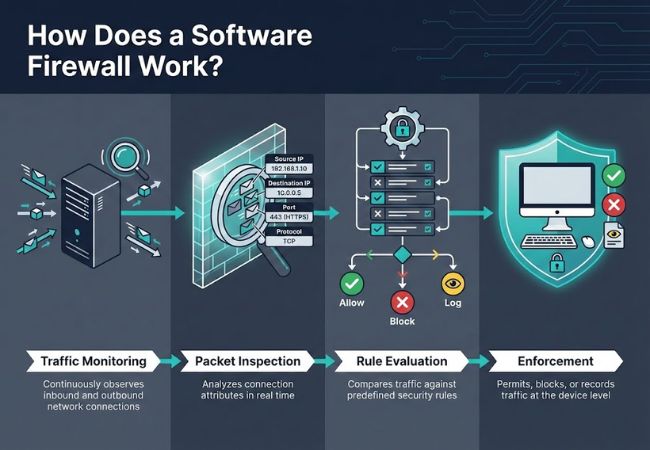
A software firewall works by continuously monitoring network traffic entering and leaving a device. Traffic evaluation relies on predefined security rules that determine whether a connection should be allowed, blocked, or recorded.
Network communication is inspected in real time using attributes such as source address, destination address, port number, and protocol type. Decision-making occurs instantly to prevent unauthorized or suspicious connections from reaching the system.
Rule enforcement at the device level allows software firewalls to respond dynamically to changing network behavior. This process enables precise control over traffic flows across endpoints, servers, and virtual environments.
Software firewall deployment focuses on controlling network traffic at the system level where connections originate or terminate.
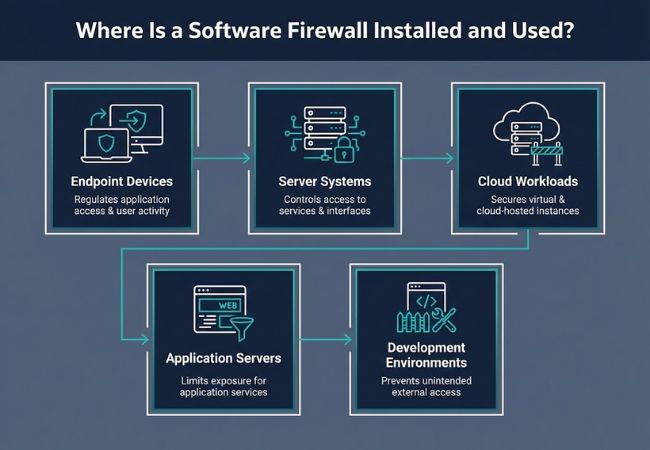
Personal computers and remote work systems commonly use software firewalls for device-level protection. Traffic control at the endpoint helps regulate application access and user-initiated network activity.
Server environments rely on software firewalls to control access to services and management interfaces. Restricting inbound and outbound connections at the server level reduces exposure to unauthorized traffic.
Virtual machines and cloud-hosted systems use software firewalls to secure workloads without physical infrastructure. Centralized rule enforcement across virtual environments supports scalable and distributed security models.
Application-facing systems use software firewalls to control traffic reaching backend services. Connection filtering at this level helps limit exposure to misuse and automated attacks.
Testing and staging systems apply software firewalls to prevent unintended external access. Controlled network boundaries protect unfinished applications and internal tools.
Modern cyber threats increasingly target individual systems, applications, and user activity rather than only network perimeters.
Attackers exploit exposed services, unauthorized connections, and malicious traffic to compromise systems. Software firewalls reduce this risk by enforcing strict traffic controls at the system level.
Network access restrictions help limit who or what can communicate with protected systems. Controlled connectivity reduces unauthorized entry points and misuse.
Proactive traffic filtering helps stop malicious communication before systems are affected. Preventive controls lower the likelihood of data breaches and system compromise.
Consistent security rules help ensure predictable behavior across protected systems. Automated enforcement reduces configuration drift and human error.
Layered defenses improve the ability to detect and contain threats. Software firewalls strengthen overall resilience by acting as a foundational control layer.
Software firewalls provide flexible, system-level security controls, while certain constraints influence performance, management, and overall coverage.
Software firewalls and hardware firewalls differ based on where traffic filtering occurs, how security rules are enforced, and which infrastructure layer is protected.
Software firewalls are installed directly on individual devices, servers, or virtual machines. Hardware firewalls are deployed as physical appliances between internal networks and external connections.
Software firewalls provide endpoint-level protection by controlling traffic specific to a single system. Hardware firewalls deliver network-level protection by filtering traffic across an entire network segment.
Application activity and system behavior are visible to software firewalls during traffic evaluation. Network packets are inspected by hardware firewalls without awareness of individual device processes.
Rule management for software firewalls occurs independently on each protected system. Centralized policy enforcement allows hardware firewalls to apply uniform rules across connected devices.
Software firewalls scale easily across cloud workloads and remote environments without physical limitations. Hardware firewalls require physical installation and capacity planning as networks expand.
Endpoint security and distributed infrastructure commonly rely on software firewalls for granular control. Perimeter security and network segmentation typically depend on hardware firewalls for boundary defense.
Choosing a software firewall over a hardware firewall depends on infrastructure design, security requirements, and operational flexibility.
Personal computers and standalone systems benefit from software firewalls that provide direct control over local network activity. Device-level protection suits environments without centralized network infrastructure.
Distributed workforces rely on software firewalls to secure devices operating outside traditional network boundaries. Consistent protection remains active regardless of user location or network connection.
Virtualized environments favor software firewalls that integrate directly with cloud workloads. Infrastructure without physical network edges requires system-level traffic control.
Cost-sensitive deployments benefit from software firewalls due to lower upfront investment. Flexible licensing models support gradual scaling as security needs evolve.
Application-specific traffic rules are easier to enforce using software firewalls. Detailed policy control supports environments requiring precise access restrictions.
Expanding environments benefit from software firewalls that can be deployed quickly across new systems. Scalability without hardware procurement supports fast-changing operational demands.
Short-term systems use software firewalls to establish immediate security controls without permanent infrastructure. Development and testing scenarios benefit from flexible and removable protection layers.
Cloud-native and application-centric architectures require security controls that operate at the system and workload level rather than only at network boundaries.
Software firewalls secure virtual machines and cloud instances by enforcing traffic rules directly on each workload. Workload-level protection supports dynamic scaling and infrastructure changes.
Application-facing systems rely on software firewalls to control inbound and outbound communication paths. Controlled traffic flow helps reduce exposure to misuse and automated attacks.
Independent firewall rules help separate workloads running within shared cloud environments. Logical isolation limits lateral movement between systems.
Service communication benefits from software firewalls that regulate access to exposed endpoints. Controlled connectivity reduces unauthorized requests and abnormal traffic patterns.
Identity-aware traffic control aligns software firewalls with zero-trust security models. System-level enforcement supports continuous verification across applications and services.
Software firewalls remain a foundational security control for managing network traffic at the system level. Precise traffic regulation helps reduce unauthorized access and limits exposure to modern cyber threats.
Evolving infrastructure models have increased reliance on endpoint, server, and cloud-level protection rather than perimeter-only defenses. Software firewalls address this shift by applying consistent security policies across distributed and dynamic environments.
Effective cybersecurity strategies balance flexibility, control, and visibility across all systems. Software firewalls support that balance by strengthening layered defenses and enabling informed security decisions as environments continue to change.
Yes, a software firewall controls network traffic, while antivirus software detects and removes malicious files. Both tools address different security risks and are commonly used together for layered protection.
Yes, a software firewall can block internet access by restricting specific connections, ports, or applications. Misconfigured rules are a common cause of blocked legitimate traffic.
Yes, free software firewalls are generally safe for basic protection on personal or low-risk systems. Advanced features such as centralized management and deep inspection are usually limited.
Yes, a software firewall reduces hacking risks by blocking unauthorized connections and suspicious traffic patterns. Protection effectiveness depends on correct configuration and rule enforcement.
Yes, most modern operating systems include built-in firewall software enabled by default. Built-in firewalls provide basic protection and can be supplemented with third-party solutions.
Yes, software firewalls can monitor and control network activity on a per-application basis. Application-level filtering helps prevent unauthorized programs from communicating externally.
No, a software firewall alone is not sufficient for full business security. Business environments require additional controls such as monitoring, access management, and layered defenses.
Yes, firewall rules can be customized to allow, block, or log specific types of network traffic. Customization enables alignment with security policies and operational requirements.
