🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Hacktivism represents the intersection of technology and activism, where cyber techniques are used to advance political, social, or ideological causes.
As digital platforms become central to governance, commerce, and public discourse, hacktivism has emerged as a visible and disruptive force within the cybersecurity landscape. These activities extend beyond traditional cybercrime, focusing on protest, exposure, and disruption rather than financial gain.
This article explains what hacktivism is, how it works, the motivations and techniques behind it, notable real-world examples, and its legal, ethical, and security implications in modern digital environments.
Hacktivism is the intentional use of unauthorised digital actions to advance political, social, religious, or environmental agendas.
Hacktivism combines hacking techniques with activist objectives and operates without financial incentives. Hacktivists target systems to express dissent, expose injustice, or pressure institutions.
Key traits of hacktivism include:
Hacktivism increases cyber risk by introducing ideologically driven threat actors into digital environments.
Understanding hacktivism requires examining how these activities are carried out, the objectives behind them, the methods used, and the implications for organisations operating in highly visible digital environments.
Hacktivism operates by identifying exposed digital assets and exploiting technical or human weaknesses to disrupt operations or deliver ideological messages. Activity follows a repeatable, structured process rather than spontaneous action.
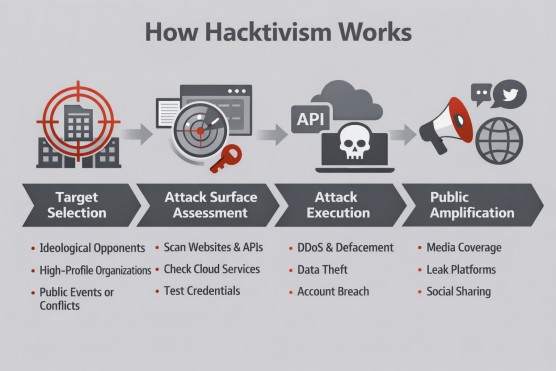
Hacktivist operations typically progress through the following stages:
Hacktivism relies on coordinated digital techniques rather than physical protest. Common attack vectors include web servers, application interfaces, email systems, and unsecured or leaked credentials.
For governments, corporations, and institutions with public-facing infrastructure, hacktivism increases operational and reputational risk, particularly during political events, social movements, or geopolitical tensions.
The goals of hacktivism focus on influencing opinion, pressuring institutions, and challenging authority through unauthorised digital actions. Hacktivist campaigns are ideologically driven and prioritise visibility and impact rather than financial gain.
Hacktivist activity has grown in scale and complexity in recent years. According to ENISA, ideology-driven attacks made up nearly 80 % of all reported incidents from mid-2024 to mid-2025, with distributed denial-of-service (DDoS) attacks, a common hacktivist method, comprising 77 % of those cases.
Disruption targets the availability of websites and online platforms to interrupt operations or reduce public visibility. DDoS attacks against government portals during elections reflect this objective.
Exposure involves leaking internal data, emails, or records to reveal alleged misconduct, corruption, or abuse. Data disclosure is used to damage credibility and force accountability.
Protest relies on visible actions such as website defacement or content manipulation to express dissent and influence narratives without long-term system damage.
Retaliation responds to censorship, legislation, military activity, or corporate decisions by attacking related digital infrastructure.
Awareness-driven attacks aim to generate media attention and expand reach through high-profile cyber incidents and social platforms.
These goals shape target selection, attack timing, and techniques, making hacktivism a visibility-driven and event-responsive cyber threat.
Common types of hacktivism describe the primary ways ideologically motivated actors conduct unauthorized cyber activity to disrupt operations, expose information, or apply public pressure. These approaches prioritise visibility and impact rather than financial gain.
Large volumes of traffic are directed at servers or networks to render websites or applications unavailable.
Example: Disrupting government portals during political protests.
Website content is altered to display political messages, slogans, or protest imagery.
Example: Replacing a corporate homepage with anti-censorship messaging.
Unauthorised access is used to steal and publicly release confidential emails, databases, or internal documents.
Example: Publishing internal communications to expose alleged corruption.
Personal information of individuals associated with an organisation is publicly exposed to intimidate or pressure targets.
Example: Releasing names and addresses of public officials or executives.
Deceptive emails or fake websites are used to steal credentials or deliver malicious payloads.
Example: Sending spoofed emails to gain access to internal systems.
Malicious software such as spyware, ransomware, or keyloggers is used to monitor, disrupt, or damage infrastructure.
Example: Deploying custom malware to exfiltrate sensitive organisational data.
Human trust and behaviour are exploited to bypass security controls without advanced technical intrusion.
Example: Impersonating IT personnel to obtain network access.
Hacktivist campaigns frequently combine multiple techniques to increase disruption, exposure, and psychological pressure on targeted organisations.
Most Recognised hacktivist groups are decentralised collectives or named entities that use cyberattacks to support ideological, political, or social agendas.
These groups operate across borders, often without formal leadership, using anonymity, coordination, and symbolism to amplify their actions.
These hacktivist groups differ in structure, tools, and motivations but share a common strategy: using cyber disruption to challenge power and influence public opinion.
Known examples of hacktivism show how ideologically motivated cyber activity is used to disrupt operations, expose information, or apply political pressure during major global events. These incidents follow a consistent pattern: symbolic targeting, public visibility, and unauthorised digital disruption.
These examples show that hacktivism consistently escalates during political conflict and international crises. From a cybersecurity perspective, hacktivist activity represents a visibility-driven threat that prioritises disruption, data exposure, and reputational impact over financial gain.
Hacktivism is distinct because it merges activism with unauthorised cyber activity, driven by ideology rather than financial gain or physical destruction.
Hacktivism is illegal under national and international cybersecurity laws, regardless of intent.
Legal systems classify hacktivist actions as cybercrimes, even if they serve political or social causes. The method—not the message—determines legal consequences.
Hacktivism remains criminal regardless of purpose, and organisations targeted by hacktivists are legally protected under cybersecurity and privacy law frameworks.
Hacktivism impacts cybersecurity risk by introducing ideologically motivated attackers who target public-facing systems for visibility and disruption. The impact extends beyond technical damage and directly affects operations, reputation, and security strategy.
Hacktivist activity creates several measurable impacts on cybersecurity programs:
Hacktivism forces cybersecurity teams to account for threats driven by ideology rather than profit. Effective defence requires understanding attacker motivation, anticipating event-driven risk, and preparing for sudden spikes in activity.
Preventing hacktivist attacks requires strong technical controls, continuous monitoring, and operational readiness. Because hacktivist activity targets visibility and public impact, organisations must prioritise the protection of public-facing systems and rapid response capabilities.
Preventing hacktivist attacks depends on proactive defence and real-time readiness, especially during periods of political, social, or reputational sensitivity.
The future of hacktivism involves decentralised networks, AI-enhanced tactics, and deeper involvement in geopolitical conflicts.
Hacktivism is evolving beyond basic disruption, adapting to advanced technologies and ideological warfare.
Hacktivism is becoming more strategic, anonymous, and technologically advanced, making it a growing concern in the global cybersecurity landscape.
Hacktivism remains an active and evolving cyber threat shaped by political events, social movements, and global conflict. While understanding its methods and prevention strategies is essential, organisations must move beyond awareness toward risk-based evaluation.
The next step is assessing how hacktivism impacts business operations, public trust, and digital resilience. This includes identifying exposed assets, monitoring periods of heightened ideological activity, and integrating hacktivist scenarios into enterprise threat models.
A focused examination of hacktivism risk enables security teams to anticipate activity, prioritise defences, and align cybersecurity strategy with broader geopolitical and reputational considerations.
