🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Key Takeaways:
Cloud Infrastructure Entitlement Management (CIEM) is a cloud security discipline focused on governing the permissions that control access to cloud resources. These permissions, known as cloud entitlements, determine what actions identities are allowed to perform across services, accounts, and environments.
In cloud-native setups, automation, shared services, and rapid scaling gradually create complex permission structures that are hard to track and even harder to validate. CIEM brings clarity to this complexity by showing how access is actually structured and where permissions quietly expand beyond what day-to-day operations require.
Clear and continuous control over entitlements allows organizations to reduce security exposure without slowing down cloud usage. Through ongoing visibility and alignment with least-privilege principles, CIEM helps keep access appropriate as cloud environments evolve and change.
Cloud security today depends heavily on controlling permissions, making visibility into entitlements essential for reducing risk in modern cloud environments.
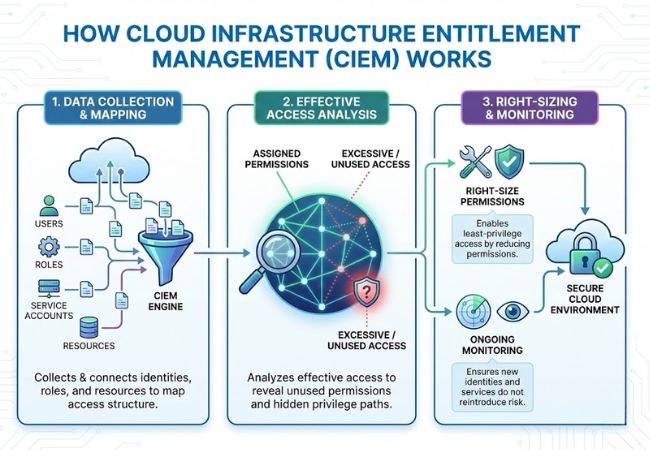
Cloud Infrastructure Entitlement Management works by continuously collecting identity and permission data from cloud environments to build a complete picture of access. This process connects users, roles, service accounts, and resources to show how permissions are structured across the cloud.
Once entitlement data is gathered, CIEM analyzes effective access rather than relying only on assigned roles or policies. This analysis reveals unused permissions, excessive access, and hidden privilege paths that increase security risk over time.
Based on these insights, CIEM enables organizations to right-size permissions and maintain least-privilege access as environments change. Ongoing monitoring ensures that new identities, services, and workloads do not silently reintroduce entitlement risk.
A CIEM solution is composed of multiple tightly connected components that work together to manage, analyze, and control cloud permissions at scale.
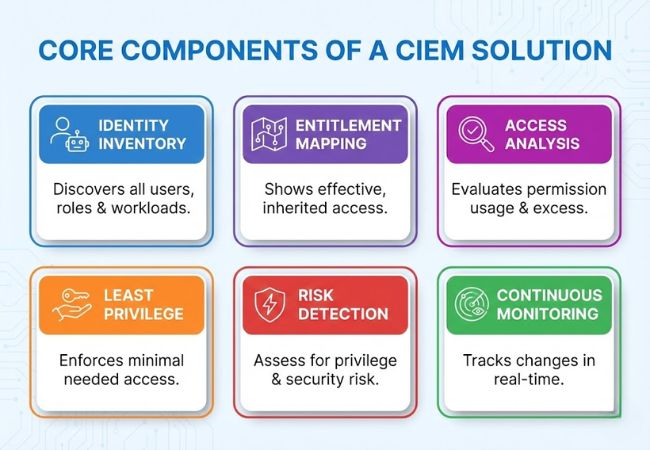
CIEM continuously discovers all identities that can access cloud resources, including users, roles, service accounts, and automated workloads. Full identity coverage is critical because non-human identities often hold broad and persistent permissions.
Permissions are mapped across cloud services, accounts, and resources to show how access is granted and inherited. This mapping reveals effective access rather than relying only on assigned roles or policies.
CIEM evaluates how permissions are actually used within cloud environments. This analysis helps identify unused access, excessive privileges, and permission paths that quietly expand over time.
Entitlements are assessed for security risk, including privilege escalation opportunities and overly permissive access. Highlighting these risks allows security teams to focus remediation efforts where exposure is highest.
CIEM supports right-sizing permissions so identities retain only the access they need. Continuous enforcement helps maintain least-privilege access as environments change and scale.
Cloud environments evolve constantly through automation and deployment cycles. CIEM monitors entitlement changes in real time to prevent new risks from emerging unnoticed.
Both CIEM and IAM play important roles in cloud security, but they address different layers of access control and risk management within cloud environments.
CIEM, CSPM, and PAM all address cloud security risk, but each focuses on a different control layer, which is why they are often used together rather than as replacements.
Cloud Infrastructure Entitlement Management operates differently across major cloud platforms because each provider uses a distinct identity and permission model.
In Amazon Web Services, access is governed through IAM users, roles, policies, and service-linked roles that often accumulate permissions over time. CIEM analyzes these layered policies to determine effective access and identify unused or overly permissive entitlements across accounts and services.
Microsoft Azure relies on role-based access control (RBAC) combined with Azure Active Directory identities and resource scopes. CIEM evaluates role assignments, inherited permissions, and cross-subscription access to reveal where privileges exceed operational requirements.
Within Google Cloud Platform, permissions are defined through roles that bundle granular actions across projects and services. CIEM examines these roles and bindings to uncover excessive access and clarify how permissions propagate across projects.
Organizations operating across multiple cloud providers face fragmented permission models and inconsistent access controls. CIEM normalizes entitlement data across AWS, Azure, and GCP to provide a unified view of permissions, making it easier to manage risk and enforce least-privilege access consistently.
Cloud Infrastructure Entitlement Management is applied across security, operations, and compliance teams to reduce risk created by excessive and unmanaged cloud permissions.
CIEM helps identify and remove unnecessary permissions that expand the cloud attack surface. Reducing excessive access limits the blast radius of compromised identities and credentials.
Least-privilege access is a core requirement of Zero Trust security models. CIEM continuously aligns permissions with actual usage, ensuring access remains minimal and justified over time.
Audits often require proof that access is controlled and reviewed regularly. CIEM provides clear visibility into entitlements, making it easier to demonstrate compliance with security and regulatory standards.
Fast-moving DevOps workflows frequently introduce temporary or automated access that is never removed. CIEM monitors these changes to prevent privilege creep without slowing down deployment cycles.
Organizations operating across AWS, Azure, and GCP face fragmented permission models. CIEM centralizes entitlement visibility to enforce consistent access policies across cloud platforms.
Choosing the right CIEM tool depends on how effectively it can handle identity complexity, permission sprawl, and continuous change across cloud environments.
A CIEM tool should work consistently across AWS, Azure, and GCP without requiring separate workflows. Unified coverage helps security teams manage entitlements centrally instead of juggling provider-specific views.
Strong CIEM platforms account for both human and non-human identities, including service accounts, workloads, and automated processes. This breadth is essential because non-human identities often hold persistent and high-impact permissions.
The ability to analyze effective access rather than assigned roles is critical for real risk visibility. Tools should clearly show how permissions combine and propagate in real usage scenarios.
A capable CIEM solution highlights excessive, unused, and risky permissions with clear prioritization. Actionable risk insights help teams focus remediation efforts where exposure is highest.
Permission right-sizing should be guided by actual usage patterns, not assumptions. Continuous least-privilege enforcement ensures access stays appropriate as environments evolve.
CIEM tools should integrate smoothly with existing IAM, security, and DevOps systems. Seamless integration reduces friction and helps entitlement management become part of everyday cloud operations.
Cloud Infrastructure Entitlement Management is essential for controlling access in modern cloud environments where permissions define security boundaries. Clear entitlement visibility helps organizations understand and govern who can do what across cloud resources.
As cloud environments grow and change rapidly, unmanaged permissions increase security risk. CIEM addresses this by continuously aligning access with least-privilege principles.
Looking forward, identity-centric security will remain a priority for cloud adoption. CIEM enables organizations to reduce risk while maintaining the speed and flexibility required for cloud operations.
Cloud entitlements are the permissions that define what actions an identity can perform on cloud resources. These permissions are granted through roles, policies, and bindings across cloud services and accounts.
CIEM does not replace Identity and Access Management systems. IAM establishes access, while CIEM continuously analyzes and governs how that access is actually used over time.
Over-permissioning increases the attack surface by allowing identities to access more resources than necessary. If an identity is compromised, excessive permissions can lead to broader damage and easier privilege escalation.
CIEM is designed to manage both human and non-human identities, including service accounts, workloads, and automated processes. This is critical because non-human identities often hold persistent and high-impact permissions.
Even single-cloud environments can develop complex and unmanaged permission structures as they scale. CIEM helps maintain visibility and control regardless of whether an organization uses one cloud provider or multiple.
CIEM evaluates actual permission usage and identifies access that is no longer required. This allows organizations to right-size permissions and keep access aligned with least-privilege principles as environments evolve.
