🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Macro viruses are closely tied to everyday document usage rather than overtly malicious software. Files exchanged for routine communication or productivity can carry hidden threats without appearing unusual or unsafe.
Regular document sharing across email, cloud storage, and internal systems increases silent exposure to embedded risks. Familiarity with common file formats often reduces scrutiny, allowing malicious content to move through normal workflows undetected.
Context around macro viruses begins with recognizing their presence within ordinary document environments. Awareness at this level creates a solid foundation for examining their nature, behavior, and implications in greater detail.
A macro virus is malware embedded within document macros that executes as part of the file rather than as a separate application. The malicious logic operates inside the document environment, allowing harmful actions to occur under the appearance of normal file behavior.
Productivity applications such as Microsoft Office support macros to automate tasks, which creates a legitimate feature surface that can be misused. Attackers typically write macro viruses using Visual Basic for Applications, enabling code to run when macro execution is permitted.
Document-based delivery distinguishes macro viruses from traditional executable malware. Infected files can spread through routine document sharing, allowing the threat to move across systems without relying on standalone programs or obvious installation processes.
Macro virus works by activating embedded instructions after macro functionality is allowed within a document. Embedded code becomes active as part of the application’s normal macro-handling process.
Macro behavior depends on permissions granted to automation features, allowing malicious routines to run with the same level of trust as legitimate macros. Actions performed during this stage align closely with expected document behavior, limiting immediate suspicion.
Activity remains confined to the document session and its associated application context. Minimal disruption during early stages allows harmful operations to continue quietly until later effects become noticeable.
Macro viruses spread through routine document sharing practices that move files between users and systems without raising immediate suspicion.
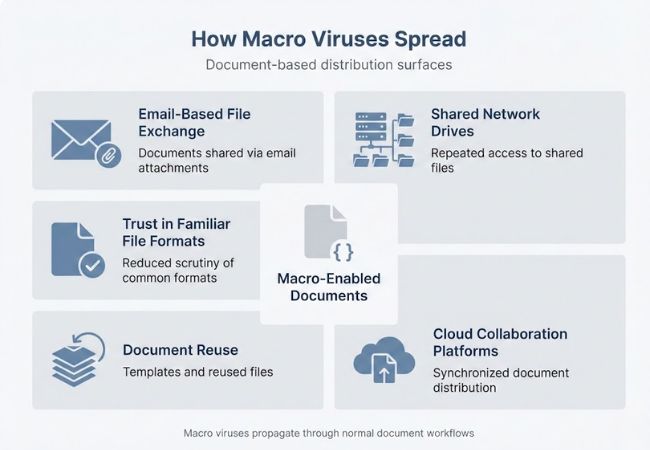
Email continues to serve as a reliable distribution channel due to its central role in professional and personal communication. Documents attached to messages often appear legitimate, allowing malicious macros to travel alongside normal correspondence.
Internal file servers and shared network locations enable documents to circulate across departments or teams. Repeated access and reuse of shared files increase exposure without introducing visible warning signs.
Cloud storage and collaboration tools facilitate rapid document distribution across multiple users and devices. Synchronization features can unintentionally replicate infected files across environments without direct user intent.
Editing, saving, and reusing existing documents extends the lifecycle of infected files. Macro-enabled templates reused over time can silently carry malicious code into new versions and contexts.
Common document types reduce perceived risk during file interaction. Familiarity with widely used formats lowers scrutiny, allowing embedded threats to pass through standard workflows undetected.
Macro viruses introduce a range of risks that affect data security, system stability, and organizational trust.

Sensitive information contained in documents or accessible through applications may be accessed without notice. Personal data, credentials, or internal records can be extracted quietly during normal document use.
Documents and files may be altered in ways that are not immediately visible. Undetected changes can compromise accuracy, reliability, or compliance requirements.
Application settings or security controls can be adjusted to reduce resistance to further misuse. Subtle changes may persist across sessions without triggering alerts.
Macro-based activity can create pathways for additional malicious components. Gradual escalation increases overall impact while delaying detection.
Shared documents increase exposure across teams or departments. A single infected file can introduce risk into multiple workflows.
Confidence in routine document handling may decline following repeated incidents. Productivity suffers as users become cautious or systems require additional controls.
Macro viruses remain relevant because their success depends less on technical sophistication and more on how documents are created, shared, and trusted in everyday environments.
Business and personal workflows continue to rely heavily on documents for communication and operations. Widespread document usage maintains a consistent surface for macro-based abuse.
Familiar file formats often signal safety rather than risk. Trust placed in routine documents lowers scrutiny during file interaction.
Older processes and templates still depend on macro functionality. Compatibility requirements keep macro usage active across many environments.
Psychological tactics remain effective at prompting user action. Urgency, authority, or familiarity can override caution during document handling.
Low-visibility behavior delays recognition during early stages. Subtle activity blends into normal application usage without obvious indicators.
Macro virus detection focuses on identifying unusual document behavior and macro activity that falls outside normal usage patterns.
Unexpected requests to enable macros often signal hidden risks. Documents demanding immediate permission to function properly warrant closer inspection.
Unusual document actions such as automatic edits or unexplained file interactions can indicate malicious activity. Subtle anomalies often appear before visible damage occurs.
Endpoint protection tools may flag suspicious macro behavior during routine scans. Alerts related to script activity or document automation should not be ignored.
Reviewing macro code can reveal unfamiliar or obfuscated instructions. Legitimate macros typically follow predictable logic tied to known tasks.
System and application logs may reflect abnormal macro-related events. Repeated or irregular macro triggers provide useful detection signals.
Macro virus prevention relies on reducing unnecessary macro exposure while reinforcing safeguards around document handling and user behavior.
Default macro settings should block automatic execution unless explicitly required. Limiting macro use reduces exposure without affecting most document workflows.
Selective permission policies help prevent unauthorized macro activity. Allowing macros only from trusted sources lowers accidental activation risk.
Cautious handling of attachments reduces entry points for infected documents. Verification of senders and file context helps prevent risky interactions.
Security tools provide an additional layer of defense against malicious macro activity. Continuous monitoring helps contain threats that bypass initial controls.
Informed users are less likely to enable macros without scrutiny. Awareness programs reinforce cautious behavior during routine document use.
Regular application and system updates strengthen built-in protections. Modern security enhancements reduce reliance on manual intervention.
Reducing macro virus risk requires consistent controls that reinforce prevention measures across users, systems, and document workflows.
Clear policies define when macro usage is permitted and when it is restricted. Consistent enforcement reduces ambiguity and accidental exposure.
User privileges should align with actual operational needs. Limiting macro permissions reduces the impact of unintended activation.
Standardized processes for receiving, storing, and sharing documents lower exposure. Controlled workflows reduce reliance on individual judgment.
Ongoing monitoring helps identify unusual macro-related activity early. Visibility across endpoints strengthens response readiness.
Regular training reinforces secure document practices over time. Familiarity with risks improves decision-making during routine tasks.
Macro viruses demonstrate how everyday document workflows can become security risks without obvious warning signs. Their reliance on trusted file formats allows malicious activity to remain closely aligned with normal user behavior.
Risk reduction depends on consistent controls rather than single protective measures. Clear macro policies, disciplined document handling, and layered security practices work together to limit exposure over time.
Sustained awareness remains essential as long as documents continue to play a central role in digital communication. Treating macro-related threats as an ongoing risk rather than a one-time issue supports stronger, more resilient security environments.
Macro viruses can still affect modern systems if macro functionality is enabled and safeguards are weak. Updated software reduces risk, but user interaction remains a critical factor.
Macro viruses target files that support embedded macros, such as word processing or spreadsheet documents. Formats without macro support are not affected in the same way.
Internet access is not required for initial activity within a document. Network connectivity may be used later if the malicious code attempts external communication.
User action is typically required to allow macro functionality. Without permission, embedded malicious code remains inactive.
Most macros are created for legitimate automation tasks and pose no threat. Risk arises only when macros originate from untrusted or unknown sources.
