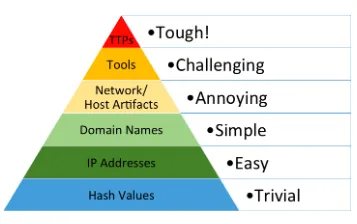
The ingested objects majorly consist of Indicators of Compromise (IOCs) such as IP, Domain, Hash, Vulnerabilities etc. But as explained by David Bianco in the Pyramid of Pain, not all Indicators of Compromise(IOCs) are created equal. The pyramid defines the pain it will cause the adversaries when you are able to deny those indicators to them. Just by blocking Hash Values, IP Addresses, Domain Names etc., we are not disarming or thwarting the APT Group but just momentarily delaying them. The APT group will switch the IP the next day and again target your organisation to gain initial foothold within the network.
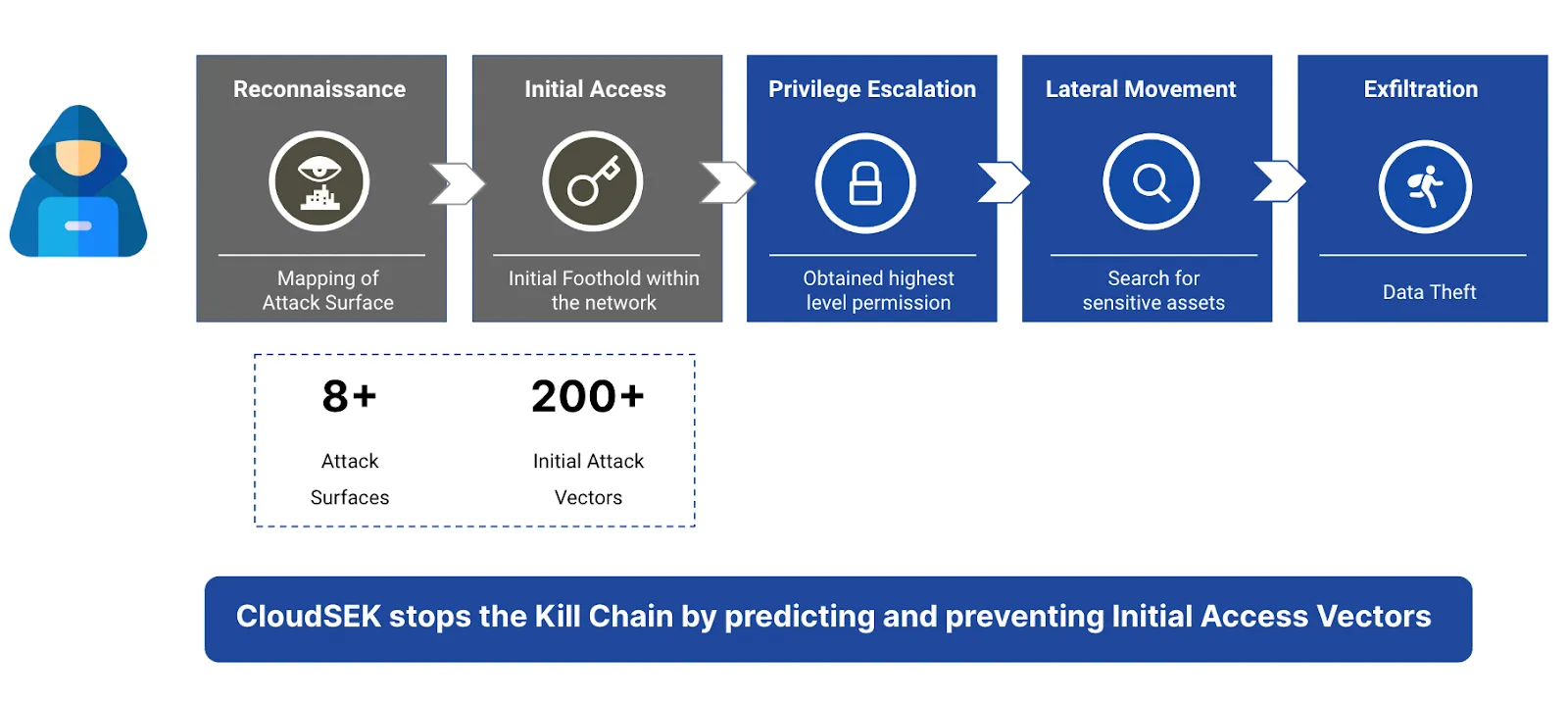
CloudSEK Platform covers 8+ Attack surfaces and monitors 200+ Initial Attack Vectors. Indicators of Attack (IOA) focus on detecting the intent of what an attacker is trying to accomplish, regardless of the malware or exploit used in an attack. Just like AV signatures, an IOC-based detection approach cannot detect the increasing threats from malware-free intrusions and zero-day exploits.
An adversary must take a number of steps in order to be successful, which are represented by an IOA. We can demonstrate this point by dissecting the spear phish, the most prevalent and still-effective tactic of determined foes.
The recipient of the phishing email must be convinced to click on a link or open a document that will infect the computer. Once in the system, the attacker will silently run another process, remain hidden in memory or on the disk, and persist through system reboots. The following action is to communicate with a command and control facility and let their handlers know that they are waiting for further instructions. IOAs are concerned with how these steps are carried out, the adversary's motivation, and the results they are attempting to achieve.
The threat actor can only be permanently neutralized by the analyst by successfully thwarting and combating the Tools, Techniques and Procedure and by mapping the Initial Attack Vector. Finally, at the apex of the Pyramid of Pain are the TTPs and IOAs. When you detect and respond at this level, you are operating directly on adversary behaviors, and not the indicators they used.
CloudSEK Platform can share this intelligence with the TIP platform ultimately empowering the analyst to predict the threats rather than prevent and patch later.
Lorem ipsum dolor sit amet consectetur adipiscing elit dolor semper at ac tempus enim laoreet massa non.
Lorem ipsum dolor sit amet consectetur adipiscing elit dolor semper at ac tempus enim laoreet massa non.

