🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Key Takeaways:
Zero Trust Security is a cybersecurity framework that requires every access request to be verified, no matter where it comes from. Instead of automatically trusting users or devices inside the network, it assumes nothing is safe until proven otherwise.
This model moves security away from relying on network boundaries and focuses on identity, device health, and real-time context. As attackers increasingly target stolen credentials and compromised endpoints, Zero Trust helps organizations reduce risk and limit unauthorized access more effectively.
Zero Trust model works by continuously authenticating and authorizing users, devices, and applications before granting access. Each request is evaluated based on identity, device health, location, and behavior in real time.
Access decisions are not permanent and are revalidated throughout a session. This approach limits lateral movement and reduces the impact of compromised credentials.
At its core, Zero Trust is guided by a set of ideas that define how access should be granted and controlled in modern security environments.
Access is never assumed to be safe just because a user is inside the network. Identity details, device condition, and context are checked every time before systems or data are made available.
Not everyone needs full access to everything, and this principle keeps it that way. By limiting users to only what their role requires, sensitive systems stay better protected.
Security is designed with the expectation that threats can already exist. Monitoring activity and restricting movement help contain incidents early instead of reacting after damage is done.
Several security controls work together behind the scenes to make Zero Trust effective in real environments.
Identity management confirms who a user is and what they are allowed to access. It handles user identities, roles, and permissions across systems.
Multi-factor authentication adds an extra step to the login process. This helps block unauthorized access even if passwords are stolen.
Devices are checked before access is granted. Security systems look at device health, updates, and endpoint protection status.
Microsegmentation separates systems into smaller zones. This limits how far an attacker can move inside the environment.
Activity is monitored throughout user sessions. This helps detect unusual behavior and respond quickly to threats.
Zero Trust becomes most visible in everyday situations where users, devices, and applications need controlled access.
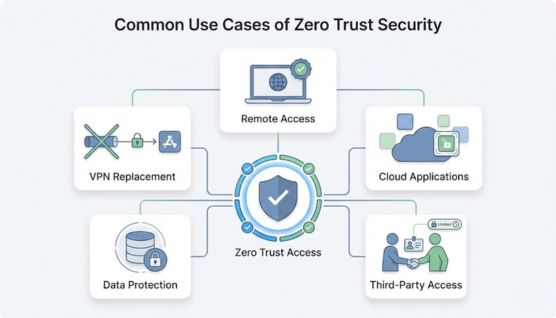
Employees can securely access applications from any location. Access depends on identity and device trust, not network location.
Zero Trust controls access to cloud services and SaaS platforms. Only verified users can reach specific resources.
Vendors and partners receive limited, controlled access. Permissions can be restricted and revoked when no longer needed.
Sensitive data is protected with strict access rules. Only authorized users on trusted devices can access it.
Zero Trust Network Access provides secure access to applications without exposing the internal network. This reduces reliance on traditional VPNs.
Beyond access control, Zero Trust delivers broader advantages that improve how organizations manage risk, scale securely, and support modern work environments.
By treating access as a controlled decision rather than a default state, Zero Trust reduces the overall risk exposure of systems and data. This approach limits the blast radius of security incidents and helps avoid large-scale breaches.
Zero Trust aligns well with regulatory requirements that demand strict access control and auditability. It supports compliance with standards such as data protection and privacy regulations by enforcing clear access boundaries.
Access is granted directly to applications instead of entire networks. This reduces friction for users while still maintaining strong security controls.
Zero Trust adapts easily as organizations grow or change. New users, applications, and cloud services can be secured without redesigning the entire security architecture.
Security teams gain clearer visibility into who can access what. This simplifies policy management and reduces reliance on complex network rules.
Zero Trust enables secure adoption of cloud platforms, SaaS tools, and hybrid environments. It allows organizations to modernize infrastructure without increasing security risk.
In cloud and remote setups, Zero Trust focuses on controlling access to applications and data rather than relying on a fixed network boundary.
Users are authenticated before they can reach cloud services or internal tools. Access decisions depend on who the user is and whether their request meets security policies.
Devices connecting from remote locations are checked for security and compliance. Only trusted and healthy devices are allowed to connect.
Instead of opening the entire network, access is granted directly to specific applications. This keeps cloud workloads and internal systems isolated.
Access is adjusted based on factors like location, behavior, and risk level. Suspicious activity can trigger additional checks or restrictions.
User sessions are monitored while access is active. If risk changes, access can be limited or revoked immediately.
The NIST Zero Trust Framework provides clear guidance for designing and implementing a Zero Trust Architecture. It defines how identities, devices, networks, applications, and data should be secured and connected.
Organizations use this framework to adopt Zero Trust in a consistent and structured way. It helps align security practices with industry standards and compliance requirements.
Implementing Zero Trust is not a single project or product rollout, but a step-by-step shift in how access and security decisions are made.
The first step is getting control over identities across users, devices, and applications. Strong Identity and Access Management (IAM) and Multi-Factor Authentication (MFA) ensure only verified users can request access.
Access should depend not just on who the user is, but also on the device being used. Device posture checks help confirm that endpoints meet security standards before connecting.
Users should only have access to what they actually need. Limiting permissions reduces exposure and lowers the impact of compromised accounts.
Instead of allowing broad network access, resources are isolated using microsegmentation. This prevents attackers from moving freely if they gain entry.
Security does not stop after access is granted. Continuous monitoring tracks behavior during sessions and helps detect unusual or risky activity early.
Zero Trust works best when implemented in phases. Many organizations begin with critical applications or remote access, then expand coverage over time.
CloudSEK supports Zero Trust by improving visibility into external risks that can lead to security breaches. It helps organizations understand what attackers can see and target outside the network.
By identifying exposed assets, leaked credentials, and misconfigured cloud resources, CloudSEK highlights gaps that Zero Trust aims to control. This allows security teams to reduce exposure before unauthorized access occurs.
CloudSEK does not control access directly, but it strengthens Zero Trust by adding risk context. This supports better security decisions and aligns with the Zero Trust approach of assuming threats exist at all times.
