🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Security environments change faster than most organizations can track. New software releases, cloud services, integrations, and configuration changes quietly introduce weaknesses over time.
Attackers take advantage of that reality by targeting known flaws that remain unaddressed rather than relying on complex zero-day exploits. Many security incidents begin not with advanced techniques, but with gaps in vulnerability management.
Managing those weaknesses requires more than occasional scans or isolated fixes. A structured vulnerability management approach helps organizations understand exposure, prioritize risk, and maintain control as environments continue to evolve.
Vulnerability management is a cybersecurity practice focused on identifying and managing security weaknesses across systems, applications, and cloud environments. Unaddressed weaknesses increase the likelihood of unauthorized access, data exposure, and system compromise.
Security operations assess identified weaknesses using severity, exploitability, and asset criticality as primary factors. This evaluation helps teams concentrate on vulnerabilities that create genuine attack paths instead of treating all findings equally.
Ongoing tracking of weaknesses and remediation progress reduces attack surface exposure over time. The process supports risk-aware decisions and sustained reduction of cyber risk as environments change.
The vulnerability management process operates as a continuous cycle that turns vulnerability data into prioritized, risk-based remediation actions.
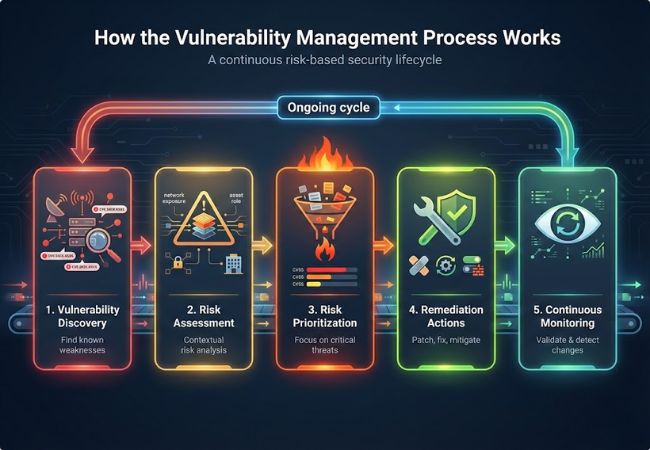
Discovery identifies security weaknesses across systems, applications, endpoints, and cloud environments. Automated scanning and assessments commonly surface issues referenced in the Common Vulnerabilities and Exposures (CVE) catalog.
Assessment evaluates vulnerabilities using technical severity, exposure level, and environmental context. Factors such as network accessibility and system role influence real-world risk.
Prioritization determines which vulnerabilities require immediate attention based on exploitability and asset criticality. Severity metrics often reference the Common Vulnerability Scoring System (CVSS), refined by threat activity and business impact.
Remediation addresses high-risk vulnerabilities through patching, configuration changes, or security control updates. Mitigation measures reduce exposure when permanent fixes cannot be applied immediately.
Monitoring verifies remediation effectiveness and detects new vulnerabilities introduced by system changes. Ongoing validation maintains visibility and prevents previously resolved issues from reappearing.
A vulnerability management program relies on a defined set of components that work together to maintain visibility, prioritize risk, and drive consistent remediation across the environment.
Asset inventory provides a clear view of systems, applications, endpoints, and cloud resources that require protection. Accurate visibility ensures vulnerabilities are mapped to real assets and ownership is clearly defined.
Vulnerability scanning identifies known security weaknesses across the attack surface using automated detection methods. A vulnerability scanner enables repeatable discovery and timely detection as environments change.
Threat intelligence adds context by highlighting active exploitation and emerging attack patterns. This insight helps distinguish theoretical vulnerabilities from those most likely to be targeted.
Risk prioritization aligns vulnerability severity with asset importance and business impact. This component ensures remediation efforts focus on vulnerabilities that create meaningful security risk.
Remediation workflows coordinate fixing activities across security and IT teams. patch management operates within this workflow to address software-related vulnerabilities efficiently.
Reporting visibility translates vulnerability data into actionable insights for security teams and leadership. Clear reporting supports accountability, tracking progress, and informed decision-making.
Cybersecurity vulnerability management is important because unmanaged security weaknesses directly increase the likelihood and impact of cyberattacks.
Vulnerability management focuses on identifying and prioritizing security risks, while patch management is limited to applying fixes for known software issues.
Security vulnerabilities are prioritized by evaluating risk factors that determine whether a weakness represents a real and immediate threat.
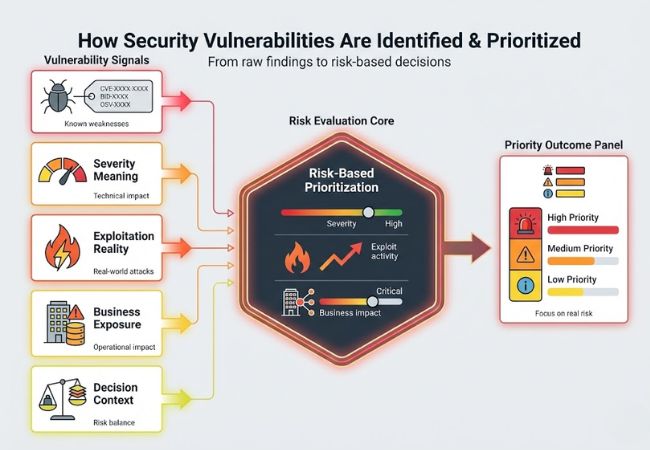
Identification relies on recognizing known weaknesses present in systems and applications. Standardized references such as Common Vulnerabilities and Exposures (CVE) provide consistent identification without repeating detection mechanics.
Severity reflects the potential technical impact of exploitation rather than the likelihood of attack. Baseline scores from the Common Vulnerability Scoring System (CVSS) offer a starting point, not a final decision.
Exploit activity determines whether a vulnerability is theoretical or actively dangerous. Inputs from threat intelligence help distinguish real attack risk from low-priority exposure.
Asset importance influences prioritization by linking technical weaknesses to operational impact. Vulnerabilities affecting critical services or sensitive data receive higher urgency.
Final prioritization reflects a balance of severity, exploit reality, and business exposure. This context-driven approach prevents security teams from chasing volume instead of risk.
Cyber security vulnerability management faces structural and operational challenges that limit visibility, prioritization, and timely remediation across modern environments.
Modern systems generate thousands of vulnerability findings across applications and infrastructure. High volume obscures real risk and slows decision-making.
Severity scores alone fail to reflect real attack likelihood. Limited context causes teams to address less important issues while critical risks persist.
Cloud platforms, hybrid infrastructure, and remote endpoints continuously expand the attack surface. Constant change makes consistent visibility difficult to maintain.
Security and IT teams often lack sufficient staffing and time for remediation. Competing operational priorities delay vulnerability resolution.
Unclear responsibility between security, IT, and development teams slows remediation progress. Accountability gaps allow vulnerabilities to remain unresolved.
Disparate security tools create isolated data and inconsistent insights. Fragmentation increases manual effort and reduces prioritization accuracy.
Many organizations struggle to confirm whether vulnerabilities are fully remediated. Lack of validation leads to recurring exposure and false confidence.
Vulnerability management supports compliance and risk reduction by providing continuous visibility, documented control, and measurable evidence of how security weaknesses are identified and addressed.
Many security regulations require organizations to identify and remediate vulnerabilities on an ongoing basis. Vulnerability management helps align security practices with regulatory expectations without relying on one-time assessments.
Security frameworks emphasize the need to prove that controls are working as intended. Ongoing vulnerability tracking demonstrates that weaknesses are actively managed rather than passively acknowledged.
Documented vulnerability data, remediation actions, and timelines provide clear audit evidence. This reduces the effort required to prepare for internal and external audits.
Vulnerability management translates technical weaknesses into risk-focused insights. Leadership gains a clearer understanding of exposure across systems and business functions.
Security policies often mandate patching timelines, risk thresholds, and remediation ownership. Vulnerability management enforces these policies through consistent measurement and tracking.
Compliance is not static, and risk changes as environments evolve. Continuous vulnerability management ensures controls remain effective over time rather than degrading between audits.
Building an effective vulnerability management program requires aligning security processes with risk priorities, operational capacity, and long-term governance needs.
Effective vulnerability management relies on disciplined execution, risk awareness, and alignment with operational realities rather than reactive or volume-driven activity.
Maintain ongoing visibility across systems, applications, and cloud environments as they change. Continuous coverage prevents blind spots created by infrastructure updates or configuration drift.
Prioritize vulnerabilities based on exploitability and business impact instead of relying on severity scores alone. Risk-based focus ensures remediation effort targets real attack paths.
Link vulnerability findings directly to remediation tasks with clear timelines. Clear action paths prevent issues from remaining unresolved after detection.
Assign responsibility for remediation across security, IT, and development teams. Defined ownership reduces delays and accountability gaps.
Verify that remediation actions fully resolve identified vulnerabilities. Validation prevents recurring exposure and false assumptions of security.
Align vulnerability management with change management and incident response workflows. Integration ensures security actions fit operational processes without disruption.
Vulnerability management is a continuous cybersecurity discipline that helps organizations stay ahead of known security weaknesses as environments evolve. The approach shifts security efforts toward prevention instead of reacting after incidents occur.
Clear visibility into vulnerabilities, structured prioritization, and accountable remediation reduce attack surface exposure over time. Limited security resources deliver greater impact when focused on weaknesses that pose real business risk.
As attackers continue to exploit unaddressed flaws, vulnerability management remains essential for security, compliance, and operational stability. Treating the practice as an ongoing program strengthens long-term resilience across modern environments.
The main goal is to reduce cyber risk by ensuring security vulnerabilities are identified, prioritized, and addressed before they are exploited. It focuses on prevention rather than reacting after incidents occur.
Vulnerability management should operate continuously, not as a one-time activity. Regular scanning, reassessment, and tracking are required to keep pace with changing environments and threats.
Vulnerability scanning is only one part of vulnerability management. Vulnerability management includes assessment, prioritization, remediation, validation, and ongoing monitoring.
No security practice can eliminate all risk. Vulnerability management significantly reduces exposure by addressing known weaknesses, but it must be combined with other cybersecurity controls.
Responsibility is typically shared between security, IT, and development teams. Clear ownership and coordination are essential for timely remediation.
