🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Mobile numbers have become a central layer of digital security, quietly connecting bank accounts, email logins, and investment platforms. When that layer is compromised, the consequences can unfold faster than most people expect.
Incidents involving unauthorized number transfers have increased alongside the rise of online banking and cryptocurrency use. Victims often realize something is wrong only after losing mobile service or receiving unexpected account alerts.
Growing dependence on SMS-based verification has made phone numbers more valuable to cybercriminals than ever before. Recognizing how these attacks unfold is essential to understanding why stronger authentication methods are becoming a necessity.
SIM swapping is a type of identity fraud where a criminal transfers your phone number to a SIM card under their control. Once the transfer is completed, they can receive your calls and text messages instead of you.
This unauthorized number reassignment gives attackers access to SMS-based verification codes used for logging into online accounts. Because many platforms rely on text message authentication, control of a phone number often means control of connected digital services.
Mobile carriers typically process SIM replacement or port-out requests through customer verification procedures. When those verification steps are manipulated through stolen personal information or social engineering, a SIM swapping incident can occur.
SIM swapping attacks work through a series of calculated steps designed to take control of a victim’s phone number.
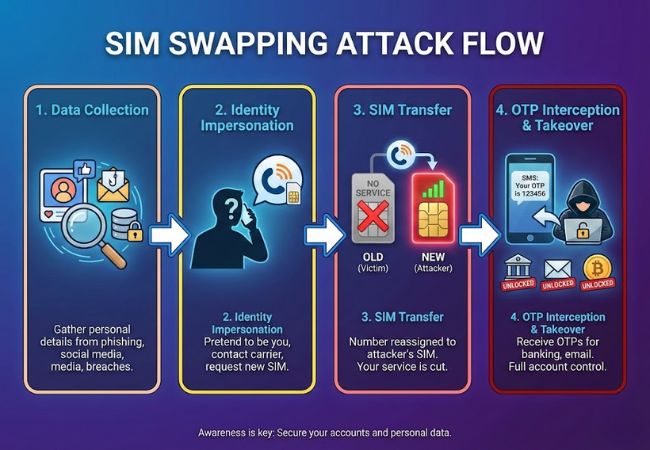
Attackers begin by gathering personal details such as full name, date of birth, address, and phone number. Attackers often obtain this information through phishing emails, social media exposure, or previous data breaches.
Using the collected details, the attacker contacts the mobile carrier while pretending to be the legitimate account holder. They typically claim the phone was lost or damaged and request a SIM replacement.
If the carrier’s verification process is bypassed, the phone number is reassigned to a new SIM card controlled by the attacker. At this point, the victim’s device usually loses network service without warning.
Once the number is under their control, the attacker triggers password reset requests on banking, email, or cryptocurrency accounts. One-time passwords sent via SMS are delivered directly to the attacker, enabling full account takeover.
A compromised phone number can quickly turn into a full-scale digital identity crisis.
Once attackers control a number, they can request password resets across multiple platforms within minutes. This creates a chain reaction where one compromised account leads to another.
Online banking systems often rely on SMS verification for login approvals and transaction confirmations. Intercepting those codes allows attackers to transfer funds or change account settings.
Cryptocurrency exchanges are frequent targets because digital assets can be moved instantly. Unlike traditional banking, crypto transactions are typically irreversible once completed.
Email accounts act as a central hub for password recovery and security notifications. Gaining access to email gives attackers the ability to reset credentials on nearly every connected service.
Cloud storage, social media accounts, and subscription platforms may contain sensitive personal information. This data can be exploited for further identity theft or sold on underground markets.
For business owners and professionals, losing control of a phone number can interrupt client communication and internal systems. Operational delays and reputational damage often follow financial loss.
Anyone who relies heavily on SMS-based verification is exposed to SIM swapping risk, but some groups face significantly higher targeting rates.
Cryptocurrency holders are frequent targets because digital assets can be transferred instantly once access is gained. Attackers often prioritize exchange accounts where large balances may be stored.
Influencers, executives, and public figures share personal details online that can aid impersonation attempts. Public visibility increases the likelihood of being singled out for targeted attacks.
Entrepreneurs often link their phone numbers to payment processors, banking tools, and administrative dashboards. A compromised number can disrupt operations and expose sensitive financial data.
People who travel often may experience temporary service issues that mask early warning signs of a SIM swap. Delayed detection gives attackers more time to access accounts.
Individuals whose personal information has appeared in previous data breaches face higher risk. Exposed details such as birth dates and addresses make carrier impersonation easier.
Reducing SIM swap risk requires strengthening both your mobile carrier security and your online authentication methods.
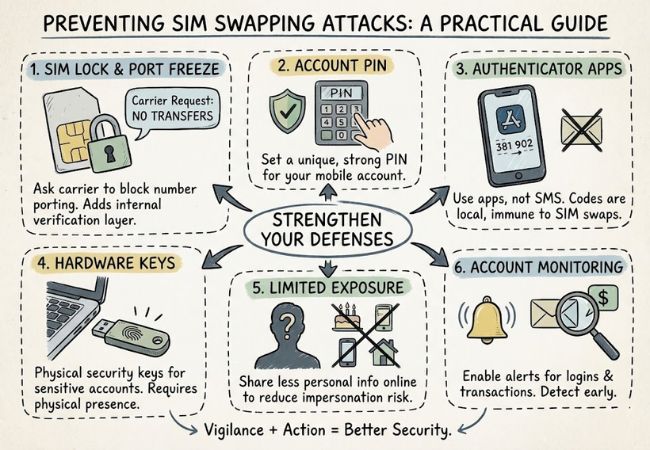
Request a SIM lock or port freeze from your mobile carrier to restrict unauthorized number transfers. This adds an internal flag that prevents changes without additional verification.
Set a strong, unique PIN specifically for your carrier account. This creates an extra barrier if someone attempts to request a SIM replacement.
Switch from SMS-based verification to app-based authentication whenever possible. Authenticator apps generate codes locally, making them immune to SIM reassignment attacks.
Use physical security keys for sensitive accounts such as email, banking, or cryptocurrency platforms. These devices require physical access, which significantly reduces remote takeover risk.
Avoid sharing personal details like birth dates, phone numbers, and addresses publicly online. The less information available, the harder it becomes for attackers to impersonate you.
Enable login alerts and transaction notifications across financial and email accounts. Early detection allows you to act before significant damage occurs.
Responding quickly and strategically can reduce long-term damage after a SIM swapping incident.
Confirm whether the loss of service is due to a SIM transfer rather than a network issue. Testing another device or contacting the carrier from a different phone can clarify the situation.
Request immediate restoration of your original SIM and account ownership. Ask the carrier to document the incident internally for fraud tracking.
Review recent login sessions across your email, financial, and cloud accounts. Look for unfamiliar IP addresses, devices, or password reset attempts.
Take screenshots of suspicious notifications, transaction confirmations, and carrier messages. Keeping a record may support fraud disputes or legal investigations.
Inform close contacts and business associates that your number was compromised. This prevents attackers from using your identity for follow-up scams.
Request escalation to a fraud or security department within your carrier. Higher-tier support teams typically have stronger verification and monitoring tools.
After regaining control, evaluate how the attack succeeded in the first place. Identifying the weak point helps prevent recurrence and strengthens future security posture.
Yes, SIM swapping is illegal because it involves identity fraud and unauthorized access to personal accounts. Transferring someone’s phone number through deception violates both telecommunications and cybercrime laws in many countries.
When attackers use a stolen identity to convince a mobile carrier to reassign a number, they are committing fraud. If they access email, banking, or cryptocurrency accounts afterward, additional charges such as computer intrusion or financial theft may apply.
Law enforcement agencies increasingly treat SIM swapping as a serious cybercrime due to its financial impact. Penalties can include fines, restitution, and imprisonment depending on the severity of the damage and jurisdiction.
SIM swapping attacks have become more frequent as digital services increasingly rely on phone-based authentication.
Reported cases of SIM swap fraud have grown alongside the expansion of online banking and cryptocurrency use. Law enforcement agencies have identified a steady increase in complaints over recent years.
Millions of dollars in losses have been linked to SIM swap-related account takeovers. Cryptocurrency platforms are often disproportionately affected due to irreversible transactions.
Many incidents go unreported because victims may not realize how the breach occurred. This makes official statistics likely lower than the actual number of attacks.
Authorities have uncovered coordinated groups specializing in SIM swap operations. These networks often target multiple victims using structured social engineering tactics.
As more services use SMS-based verification, the number of potential targets continues to expand. Increased digital dependence has widened the attack surface for cybercriminals.
SIM swapping has evolved into a serious cybersecurity threat because mobile numbers now sit at the center of digital identity. When control of that number is lost, access to banking, email, and investment accounts can quickly follow.
Growing reliance on SMS-based verification has unintentionally expanded the attack surface for cybercriminals. As digital services continue to grow, stronger authentication methods are becoming a practical necessity rather than an optional upgrade.
Understanding how SIM swapping attacks work makes it easier to recognize warning signs and reduce exposure. Proactive security decisions today can prevent significant financial and personal damage in the future.
Yes, SIM swapping does not require malware or physical access to your device. The attack targets mobile carrier verification systems rather than the phone itself.
Changing your number may reduce immediate exposure but does not remove the underlying vulnerability. Security depends more on authentication methods than on the number alone.
Accounts connected to payment processors, payroll systems, or administrative tools often attract targeted attempts. Higher financial value increases the incentive for organized fraud groups.
Any platform that allows SMS-based password resets can be accessed after a SIM swap. Control of the phone number enables attackers to reset login credentials quickly.
SMS verification provides basic protection but is considered weaker than app-based or hardware-based authentication. Security professionals increasingly recommend stronger multi-factor methods.
