🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Key Takeaways:
Remote Code Execution (RCE) is a type of security vulnerability that allows an attacker to execute malicious code on a remote system, such as a server, application, or endpoint device. This execution occurs without physical access and often without authentication, making RCE one of the most dangerous classes of vulnerabilities.
Once exploited, RCE gives attackers the ability to control how a system behaves. This level of access can allow them to install malware, manipulate data, or use the compromised system as an entry point into a larger network.
Remote Code Execution works by chaining multiple weaknesses in an application until attacker-controlled input is executed by the system. Each stage builds on the previous one, turning a simple input flaw into full code execution.
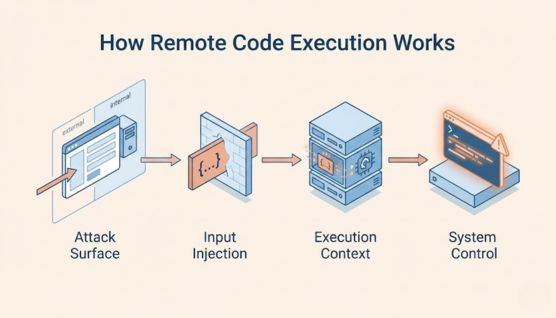
RCE starts with an exposed attack surface such as a web application, API endpoint, application server, or network service. These components accept external input and interact directly with backend logic or system resources.
The attacker sends crafted input containing executable code, commands, or serialized objects. Weak input validation allows this data to pass through the application as trusted content.
The application processes the injected input within its runtime environment, such as a web server or operating system shell. At this point, the malicious payload is executed as code rather than treated as data.
Once execution occurs, the attacker gains control within the permissions of the affected process. This access is often used to escalate privileges, deploy malware, or move laterally across connected systems.
Remote Code Execution vulnerabilities are caused by weaknesses in how software is designed, implemented, or maintained. These flaws allow attacker-controlled input to reach execution paths that were never intended to process code.
Applications that fail to validate, sanitize, or constrain user input are highly susceptible to RCE. Untrusted data can be interpreted as commands, scripts, or executable objects instead of plain input.
Many RCE vulnerabilities stem from known flaws already documented as CVEs. When systems are not patched, attackers can exploit publicly available exploit code to gain remote execution.
Applications that deserialize untrusted data without proper checks may execute embedded malicious objects. This is a common RCE vector in Java, .NET, and PHP-based applications.
Overly permissive services, exposed admin interfaces, or unsafe default configurations increase the risk of RCE. These misconfigurations often give attackers a direct path to code execution.
Remote Code Execution attacks have caused some of the most serious security incidents in recent years. These examples show how a single vulnerability can give attackers remote control over systems.
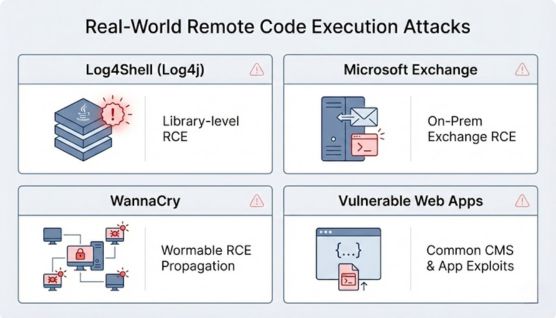
Log4Shell was a Remote Code Execution vulnerability found in the Apache Log4j logging library. Attackers could trigger it by sending a specially crafted message, which caused vulnerable applications to run malicious code.
Because Log4j is used in many Java applications, this flaw affected thousands of systems worldwide. Attackers used it to install malware and ransomware.
Several Microsoft Exchange Server vulnerabilities allowed attackers to execute code remotely on email servers. Once exploited, attackers could install web shells to maintain access.
This made it possible to read emails, steal data, and move deeper into company networks. Many organizations were affected before patches were applied.
The WannaCry attack used a Remote Code Execution flaw in the Windows SMB service. This allowed the ransomware to spread automatically between unpatched computers.
No user action was required, which made the attack spread extremely fast. Entire networks were locked down within hours.
Remote Code Execution vulnerabilities are also common in web applications and content management systems. Attackers exploit these flaws to run commands on web servers or upload malicious files.
These attacks are often used as a starting point for data theft, malware installation, or further system compromise.
Detecting Remote Code Execution attacks requires watching for unusual behavior rather than relying on a single alert. Since RCE allows attackers to run code like a legitimate process, early detection depends on visibility across systems, applications, and networks.
RCE attacks often cause applications to behave abnormally, such as spawning unexpected system processes or executing shell commands. Monitoring application logs and runtime behavior helps identify these warning signs early.
Unexpected commands, scripts, or file changes in system and application logs can indicate remote code execution. Logs showing abnormal request patterns, strange parameters, or repeated failed inputs are especially important.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can detect known RCE exploit patterns. These tools analyze network traffic for malicious payloads and suspicious command execution attempts.
Endpoint Detection and Response (EDR) tools monitor process execution on servers and endpoints. They can flag unauthorized code execution, privilege escalation attempts, or malware dropped through RCE exploits.
Many RCE attacks are followed by actions such as web shell installation, outbound connections to command-and-control servers, or unusual privilege changes. Detecting these follow-up behaviors often reveals an earlier RCE breach.
Preventing Remote Code Execution attacks focuses on reducing the chances that malicious input ever reaches an execution point. A strong prevention strategy combines secure development practices with ongoing system protection.
Many RCE attacks exploit known vulnerabilities with available fixes. Keeping operating systems, applications, frameworks, and libraries up to date closes common entry points attackers rely on.
Developers should validate and sanitize all user input to ensure it is treated as data, not executable code. Following secure coding standards significantly reduces RCE risk at the application level.
Applications should run with the minimum permissions required to function. If an RCE vulnerability is exploited, limited privileges help contain the damage.
Web Application Firewalls (WAFs) can block malicious payloads before they reach the application. They are especially effective at stopping common RCE exploit patterns in web traffic.
Network segmentation prevents attackers from easily moving across systems after exploitation. Continuous monitoring helps detect and contain RCE attempts before they escalate.
CloudSEK helps organizations reduce the risk of Remote Code Execution by providing early visibility into vulnerabilities and emerging threats. Instead of blocking attacks directly, it focuses on identifying risk signals before exploitation occurs.
Through continuous threat intelligence, CloudSEK tracks exploited CVEs, attacker activity, and vulnerability disclosures that commonly lead to RCE attacks. This allows security teams to prioritize patching and remediation efforts based on real-world threat context.
Additionally, CloudSEK monitors an organization’s external attack surface to identify exposed applications, misconfigurations, and weak entry points. By highlighting these risks early, it supports proactive defense and complements tools like WAFs, EDR, and patch management systems.
