🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
A security breach rarely ends with the first compromised machine. After gaining initial access, attackers focus on reaching additional systems within the same network.
Enterprise environments depend on shared credentials, administrative privileges, and directory services to operate efficiently. Those same trusted mechanisms can be used to access file servers, databases, and domain controllers without raising immediate suspicion.
Security professionals describe this internal progression as lateral movement. Recognizing how it unfolds and how it can be detected and prevented is critical to reducing the overall impact of an intrusion.
Lateral movement is a post-compromise attack technique in which an intruder uses valid credentials or trusted system access to move from one internal system to another within the same network. It occurs after initial access and enables the attacker to expand control beyond the originally breached device.
Access to a single workstation rarely provides direct control over sensitive infrastructure. Internal authentication systems such as Active Directory, remote administration protocols, and shared service accounts create pathways that can be reused without exploiting additional vulnerabilities.
Expansion across servers, user accounts, and administrative systems increases the attacker’s operational reach. Broader access often leads to domain compromise, data theft, or coordinated ransomware deployment.
Attackers use lateral movement to expand control beyond the initially compromised system.
Lateral movement works by leveraging legitimate internal authentication and communication mechanisms to move between systems.
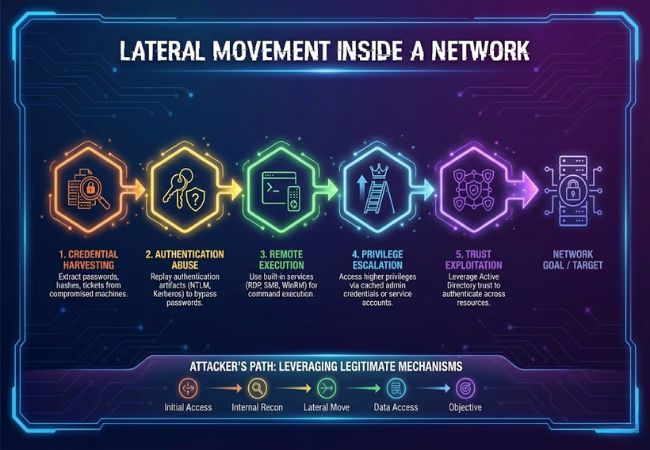
Several well-documented techniques enable attackers to move between internal systems after gaining access.
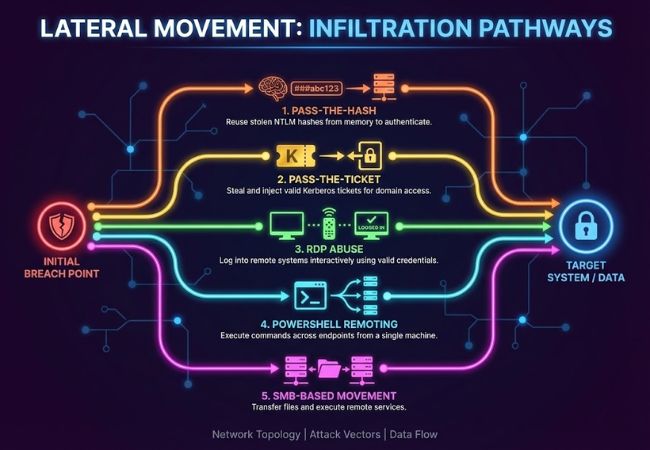
Pass-the-Hash involves reusing stolen NTLM password hashes to authenticate to other machines. The attacker does not need the original password, only the hash stored in memory.
Pass-the-Ticket targets Kerberos authentication by stealing and injecting valid tickets. Injected tickets allow impersonation of users with access to domain resources.
RDP abuse occurs when valid credentials are used to log into remote systems interactively. Administrative accounts make this method especially effective across servers.
PowerShell remoting allows command execution across multiple endpoints from a single machine. Administrative scripting capabilities enable reconnaissance and payload deployment.
Server Message Block is used to transfer files and execute remote services within Windows environments. Combined with valid credentials, it provides reliable system-to-system access.
A common attack begins with a phishing email that compromises a single employee workstation. The attacker gains local access and begins searching the system for cached credentials or active sessions.
Credential dumping tools are then used to extract administrator hashes or Kerberos tickets from memory. Those credentials allow authentication to file servers and other internal machines without triggering external intrusion alerts.
Access eventually reaches a domain controller or backup server, where control over identity infrastructure is established. From that point, ransomware deployment or large-scale data exfiltration can be executed across the environment.
The MITRE ATT&CK framework classifies lateral movement under tactic TA0008. This category documents the techniques adversaries use to move between systems after gaining access.
Each technique, such as Pass-the-Hash or Remote Services, is mapped with detailed descriptions and detection guidance. Security teams use these mappings to understand attacker behavior and measure defensive coverage.
Aligning detection controls with ATT&CK improves visibility into internal attack paths. Structured mapping also supports threat hunting, red teaming, and security maturity assessments.
Detecting lateral movement requires visibility into authentication activity, endpoint behavior, and internal network traffic. Valid credentials are often used, so anomalies matter more than malware signatures.
Endpoint Detection and Response platforms monitor process execution, credential access, and remote connection attempts. Unusual administrative tool usage or abnormal parent-child process chains can indicate pivoting activity.
Log analysis of NTLM and Kerberos events helps identify suspicious ticket usage and repeated lateral login attempts. Unusual logon types, failed attempts followed by success, or account usage outside normal patterns require investigation.
Behavioral baselining of user and service accounts highlights deviations in access patterns. Privilege changes, abnormal ticket requests, or service account misuse often signal internal spread.
Monitoring east-west traffic exposes unexpected connections between systems. Lateral connections between workstations and domain controllers should trigger scrutiny.
Preventing lateral movement requires limiting credential abuse and reducing implicit trust inside the network.
Network segmentation restricts communication between user workstations, application servers, and critical infrastructure. Limiting east-west connectivity reduces how far an attacker can pivot after compromise.
Least privilege ensures users and service accounts only receive permissions required for their roles. Restricting administrative rights lowers the impact of stolen credentials.
Multi-factor authentication adds a verification layer beyond passwords. Even if credentials are compromised, additional authentication requirements reduce unauthorized access.
Privileged Access Management controls, monitors, and rotates administrative credentials. Temporary privilege elevation reduces persistent high-level access across systems.
Active Directory hardening includes monitoring domain controllers, restricting replication permissions, and protecting service accounts. Strengthening identity infrastructure limits domain-wide compromise.
Zero Trust architecture enforces continuous validation of users and devices before granting access. Access decisions are based on identity, device health, and contextual risk rather than network location.
Lateral movement in cloud and hybrid environments primarily targets identity tokens, API access, and cross-platform trust relationships instead of traditional workstation-to-server pivots.
Selecting a lateral movement detection solution requires evaluating how well the platform reduces attacker dwell time and limits internal spread under real-world conditions.
The solution should integrate identity, endpoint, and network data into a unified detection model. Fragmented tools create blind spots that attackers exploit during internal pivoting.
Modern attacks focus on identity rather than malware alone. A strong platform prioritizes credential monitoring, privilege tracking, and authentication abuse detection across environments.
Visibility must extend beyond perimeter controls into east-west communication paths. Systems that only monitor internet-facing threats miss internal propagation.
The platform should continuously assess exposure created by administrative accounts and service permissions. Risk scoring of privileged identities provides early warning of potential escalation paths.
On-premises and cloud telemetry must be analyzed together rather than separately. Unified monitoring reduces the risk created by federated identity and cross-platform trust.
Detection alone is insufficient without a rapid response capability. Solutions should support automated credential invalidation, session termination, and endpoint isolation to prevent further movement.
Modern EDR and XDR platforms disrupt lateral movement by correlating identity activity, endpoint behavior, and network signals into a unified response workflow.
EDR focuses on endpoint-level visibility, while XDR expands detection across identity providers, email systems, cloud workloads, and network layers. Correlating these signals exposes coordinated pivot attempts that would appear harmless in isolation.
Advanced platforms connect authentication events with process execution on endpoints. A suspicious Kerberos ticket request followed by remote command execution can trigger high-confidence alerts.
User and service account behavior is continuously profiled to detect deviations in access patterns. Abnormal administrative logins or sudden lateral connections between systems elevate risk scoring.
Once suspicious pivoting is confirmed, automated playbooks can isolate endpoints, revoke tokens, or disable compromised accounts. Rapid containment prevents additional systems from being accessed.
Built-in MITRE ATT&CK mapping helps analysts investigate lateral movement techniques methodically. Structured telemetry enables faster root cause analysis and impact assessment.
Lateral movement transforms a limited breach into a widespread security incident by allowing attackers to expand control across internal systems. Containing this stage quickly determines whether an intrusion remains isolated or escalates into a domain-wide compromise.
Reducing internal trust, protecting credentials, and monitoring identity behavior are central to limiting attacker movement. Strong detection and rapid response capabilities significantly lower the impact of post-compromise activity.
Not every attack includes lateral movement, but most large-scale breaches do. Attackers use it when broader access is needed beyond the initially compromised system.
Privilege escalation increases access rights on a single system. Lateral movement involves accessing additional systems across the network using existing or elevated credentials.
Activity often relies on valid credentials and legitimate administrative tools. Traditional signature-based detection may not flag behavior that appears operationally normal.
Zero Trust significantly reduces internal trust assumptions and limits credential misuse. Continuous monitoring is still required because no single architecture eliminates risk.
Dwell time varies depending on monitoring maturity and response capability. In environments with limited visibility, attackers may expand access for days or weeks before triggering detection.
