🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Modern cloud environments rely heavily on automation, which introduces new security risks at the infrastructure layer. Infrastructure-as-Code (IaC) security addresses those risks by focusing on how cloud resources are defined before deployment.
Reusable IaC templates allow teams to move fast, but mistakes can spread just as quickly across environments. Exposed services, excessive permissions, and weak network controls often originate from insecure infrastructure definitions.
IaC security places validation and enforcement directly into the infrastructure change process. Early checks allow teams to correct risky configurations before deployment, reducing exposure and preventing avoidable cloud security incidents.
IaC security is the practice of securing cloud infrastructure by enforcing security requirements directly within infrastructure-as-code definitions. Cloud resources are evaluated based on their intended configuration before they are created, rather than after deployment.
Infrastructure defined through code represents the blueprint of cloud environments, including access controls, network exposure, and service permissions. IaC security focuses on ensuring that this blueprint does not contain insecure or noncompliant configurations.
The primary purpose of IaC security is prevention rather than detection or response. Security risks are eliminated at the design stage so insecure infrastructure never becomes part of the cloud environment.
IaC security works by evaluating infrastructure definitions early to identify and stop risky configurations before cloud resources are deployed.
IaC security is important for cybersecurity because cloud infrastructure is now created through automation, where small configuration mistakes can quickly become large-scale security exposures.

Cloud environments often become exposed due to misconfigured networks, storage, or services defined in infrastructure code. IaC security reduces this exposure by preventing insecure configurations from being deployed in the first place.
Access permissions defined in infrastructure code frequently exceed what is actually required. Infrastructure-as-Code security helps enforce least-privilege access early, limiting how far an attacker can move if access is gained.
A large number of cloud breaches are caused by basic configuration errors rather than advanced attacks. IaC security addresses this problem by stopping common mistakes before they create real-world impact.
Security practices often vary between teams, environments, and projects. IaC security creates consistency by applying the same security expectations wherever infrastructure code is reused.
Infrastructure code is designed to be reused and scaled across environments. IaC security prevents insecure patterns from spreading by blocking risky configurations before they are replicated.
Traditional cybersecurity controls focus on detecting issues after deployment. IaC security moves protection earlier in the lifecycle, reducing dependence on monitoring and incident response.
Insecure IaC introduces serious cybersecurity risks because infrastructure definitions control access, exposure, and trust relationships across entire cloud environments.
Infrastructure code can unintentionally expose storage, databases, APIs, or internal services to the public internet. Deployed exposure often remains unnoticed until actively exploited.
Access permissions defined in IaC frequently grant broader rights than required. Compromised credentials become far more dangerous when identities are over-permissioned at the infrastructure level.
Service accounts, roles, and machine identities are often created through Infrastructure-as-Code. Weak identity definitions allow attackers to move laterally or persist without triggering application-level controls.
Loose network rules defined in infrastructure code can eliminate isolation between systems. Poor segmentation increases blast radius once an attacker gains initial access.
IaC pipelines can be abused if security controls are weak or missing. Malicious or compromised code changes can rapidly deploy insecure infrastructure across environments.
Manual changes made outside infrastructure code cause environments to diverge from intended security states. Drift reduces visibility and weakens long-term security posture.
IaC commonly relies on shared modules and third-party templates. Untrusted or outdated components can introduce hidden vulnerabilities at scale.
IaC security is built on a set of controls that ensure infrastructure definitions remain secure, consistent, and enforceable across cloud environments.
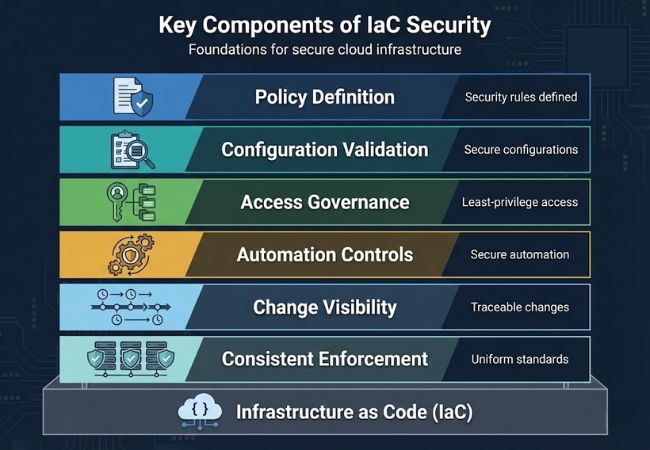
Security requirements are defined as explicit rules that infrastructure configurations must follow. These rules establish what is allowed, restricted, or required across environments.
Infrastructure definitions are checked to ensure services, networks, and identities are configured securely. Validation focuses on preventing risky defaults and insecure design choices.
Permissions and roles defined in infrastructure code are controlled to follow least-privilege principles. Strong governance limits unnecessary access and reduces the impact of credential compromise.
Security enforcement is aligned with automated infrastructure workflows. Controls ensure that automation does not bypass security expectations as environments scale.
Infrastructure changes remain traceable and reviewable over time. Clear visibility helps teams understand what changed, why it changed, and whether it introduced risk.
Security standards are applied uniformly wherever infrastructure code is used. Consistency prevents gaps caused by manual configuration or team-specific practices.
IaC security should be applied at the earliest possible stage of infrastructure creation to prevent insecure configurations from ever reaching cloud environments.
Infrastructure definitions should be reviewed for security risks while they are being written. Early checks reduce rework and prevent insecure patterns from entering shared codebases.
Security validation should occur before infrastructure is provisioned in any environment. Blocking risky configurations at this stage avoids exposing live systems.
Every modification to infrastructure code introduces potential risk. Infrastructure-as-Code security ensures changes are reviewed consistently rather than relying on ad hoc checks.
Infrastructure often expands across regions, accounts, and environments. Applying IaC security during scaling prevents small mistakes from multiplying at scale.
Infrastructure definitions evolve over time as requirements change. Ongoing enforcement ensures security expectations remain aligned with current infrastructure intent.
IaC security differs from other cloud security approaches by focusing on preventing insecure infrastructure at the code level before deployment rather than detecting issues after resources are live.
Infrastructure-as-Code (Iac) security supports cybersecurity programs by embedding preventive controls directly into how cloud infrastructure is designed, approved, and scaled across the organization.
Security teams gain earlier visibility into infrastructure risk without relying on post-deployment monitoring or manual reviews. Enforced standards in infrastructure code help align development teams with organizational security policies automatically.
Audit and compliance efforts also become easier because infrastructure intent is documented, versioned, and traceable. Clear evidence of security enforcement strengthens governance while reducing operational overhead.
Infrastructure-as-Code security has become essential as cloud environments grow more automated and interconnected. Securing infrastructure at the definition stage helps organizations reduce exposure, prevent repeatable mistakes, and maintain stronger control over cloud risk.
As automation continues to scale, treating infrastructure code as a security boundary is no longer optional. Preventive controls applied early create cloud environments that are safer, more consistent, and easier to govern over time.
No. Any team using automated cloud provisioning can introduce security risks through misconfigurations, regardless of size.
No. It complements runtime monitoring and incident response by preventing insecure infrastructure from being created in the first place.
IaC security is a shared responsibility. Development teams define infrastructure, while security teams set and enforce the guardrails.
Yes. Security rules applied to infrastructure definitions provide consistent, auditable evidence of compliance across environments.
No. When implemented correctly, it reduces rework and remediation by catching issues early, which often speeds up delivery overall.
