🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
الوجبات السريعة الرئيسية:
إدارة وضع أمان البيانات (DSPM) هي نهج الأمن السيبراني الذي يكتشف ويصنف ويحلل البيانات الحساسة عبر البيئات السحابية والهجينة. فهي توفر رؤية لمكان تخزين المعلومات الهامة ومدى تعرضها للخطر بسبب التكوينات الخاطئة أو بيانات الظل أو الامتيازات المفرطة.
على عكس أدوات الأمان التقليدية التي تركز على البنية التحتية، تركز DSPM الأمان على البيانات نفسها، مما يسهل تقييم المخاطر الحقيقية على مستوى الأصول. وهي تحدد البيانات الحساسة ومسارات الوصول والضوابط المرتبطة بها لمساعدة المؤسسات على تعزيز الامتثال وتحديد نقاط التعرض ذات المغزى.
يربط DSPM أيضًا حساسية البيانات بسياق الهوية وتكوين التخزين ومواءمة السياسة للكشف عن الأشخاص الذين يمكنهم الوصول إلى المعلومات وكيفية انتقالها عبر الخدمات. مع هذا الأساس، فإن الخطوة التالية هي فهم كيفية تنفيذ DSPM لهذه الإجراءات عبر النظم البيئية السحابية المعقدة.
أدى اعتماد السحابة وSaaS إلى توزيع البيانات الحساسة عبر منصات متعددة، مما يجعل من الصعب تتبع مكان وجودها وكيفية حمايتها. تخلق هذه البصمة الموزعة نقاطًا عمياء حيث يمكن للتكوينات الخاطئة والأذونات المفرطة والنسخ المنسية أن تؤدي إلى مخاطر التعرض الصامت.
تواجه عمليات التدقيق اليدوي وأدوات الأمان غير المتصلة صعوبة في متابعة البيانات عبر الحسابات والمناطق والخدمات. ونتيجة لذلك، غالبًا ما تعرف الفرق وجود المخاطر ولكنها تفتقر إلى الوضوح بشأن المخاطر الأكثر أهمية أو مكان نشوئها.
تتغلب DSPM على هذه التحديات من خلال ربط البيانات الحساسة بالهويات والتطبيقات والموارد السحابية التي تتفاعل معها. يصبح هذا السياق أساسًا لفهم كيفية تقييم DSPM لسلوك البيانات والتعرض وظروف الوصول عبر البيئات السحابية.
تعمل DSPM من خلال اكتشاف البيانات الحساسة وتحليل من يمكنه الوصول إليها ومراقبة مخاطر التعرض عبر بيئات السحابة وبيئات SaaS.
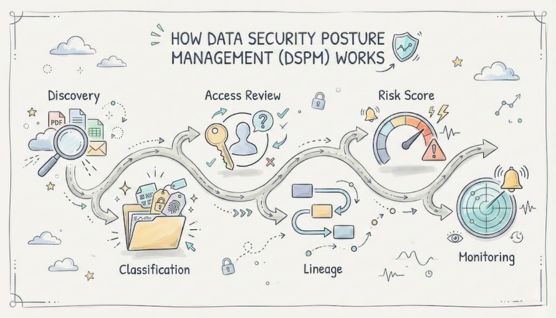
يقوم DSPM بمسح التخزين السحابي وقواعد البيانات وبحيرات البيانات وتطبيقات SaaS لتحديد موقع PII و PHI وبيانات الاعتماد والأصول الحساسة الأخرى. كما يكشف أيضًا عن بيانات الظل والنسخ غير المُدارة التي قد تؤدي إلى مخاطر التعرض المخفية.
يتم تصنيف كل مجموعة بيانات بناءً على الحساسية وتأثير الأعمال والأهمية التنظيمية. تعمل البيانات الوصفية مثل الملكية والغرض ومتطلبات الاحتفاظ على تحسين تحديد الأولويات.
تقوم DSPM بتقييم المستخدمين والأدوار وحسابات الخدمة ومفاتيح API لتحديد من يمكنه الوصول إلى الأصول الحساسة. وهذا يسلط الضوء على الامتيازات المفرطة ومسارات الوصول غير المستخدمة ومخاطر الهوية، مما يعزز ضوابط الامتيازات الأقل.
يتتبع DSPM كيفية انتقال البيانات عبر الخدمات وخطوط الأنابيب والتطبيقات وعمليات الدمج. تكشف النسب عن الانتشار غير المقصود وعمليات النقل غير الآمنة ونقاط التعرض النهائية.
يجمع تصنيف المخاطر بين حساسية البيانات ومستويات الوصول ونقاط ضعف التكوين لتحديد شدة التعرض الحقيقية. تساعد عملية تحديد الأولويات هذه الفرق على معالجة المخاطر الأكثر تأثيرًا أولاً.
تراقب DSPM انحراف التكوين وتغييرات الأذونات وفجوات التشفير وسلوك البيانات غير المعتاد. تحدد التنبيهات حالات التعرض الجديدة بسرعة حتى تتمكن الفرق من التصرف قبل تصاعد المشكلات.
تشكل هذه القدرات معًا القاعدة الوظيفية لـ DSPM وتؤدي إلى المكونات التي تجعل حل DSPM فعالاً.
تتضمن حلول DSPM العديد من المكونات الأساسية التي تعمل معًا لحماية البيانات السحابية طوال دورة حياتها.
يوفر الفهرس الكامل لجميع أصول البيانات عبر الحسابات السحابية والمناطق عرضًا مركزيًا لمواقع التخزين. يساعد هذا في القضاء على النقاط العمياء ويكشف بيانات الظل.
تحدد Lineage كيفية انتقال البيانات بين الأنظمة وخطوط الأنابيب والنسخ الاحتياطية وعمليات الدمج. يساعد فهم هذه التدفقات في تحديد مخاطر الانتشار ومسارات التعرض غير المقصودة.
يقوم DSPM بتقييم إعدادات التشفير واستخدام KMS وجداول تدوير المفاتيح والأصول غير المشفرة. تسلط هذه الأفكار الضوء على ضوابط التشفير الضعيفة التي قد تؤدي إلى انتهاكات الامتثال.
يتم تقييم شدة التعرض باستخدام إطار عمل الدرجات الذي يمزج بين الحساسية وعمق الوصول ونقاط ضعف التكوين. هذا يجعل من السهل تركيز الموارد على نقاط الضعف الأكثر أهمية.
تقدم بعض المنصات إجراءات تلقائية مثل إزالة الوصول العام أو تصحيح الأذونات أو فرض التشفير. تعمل الأتمتة على تقليل وقت الاستجابة وإزالة الحمل التشغيلي اليدوي.
تقيس برامج DSPM القوية الأداء باستخدام مقاييس تشغيلية تعكس تقليل التعرض الحقيقي.
توضح هذه المقاييس تأثير DSPM على تقليل التعرض وتحسين وضع أمان السحابة.
حدد فحص DSPM مخزن كائنات يحتوي على أكثر من 95,000 سجل حساس بأذونات يمكن الوصول إليها بشكل عام. أدت المعالجة الآلية إلى إزالة الوصول العام في غضون دقائق وتقليل نافذة التعرض بشكل كبير، مما يدل على قيمة المراقبة المستمرة وتحديد الأولويات.
تحدد DSPM مخاطر البيانات عالية التأثير مبكرًا، مما يقلل من احتمالية التعرض العرضي أو الوصول غير المصرح به. تعمل هذه الرؤية الاستباقية على تعزيز الوضع الأمني العام.
تقوم DSPM بمواءمة البيانات الحساسة مع متطلبات مثل GDPR و HIPAA و SOC 2. تعمل جهود الأدلة الآلية على تقليل أعباء عمل التدقيق وتبسيط تقارير الامتثال.
تكتسب فرق الأمان رؤية لأصول البيانات والهويات وموارد السحابة التي تتطلب اهتمامًا فوريًا. هذا يقلل من إجهاد التنبيه ويحسن اتخاذ القرار.
يقلل DSPM الوقت المستغرق في عمليات التدقيق اليدوي ورسم خرائط البيانات والارتباط متعدد الأدوات. تتجنب الفرق مطاردة النتائج منخفضة المخاطر وتحافظ على إنتاجية أعلى.
يؤدي ربط البيانات بأدوار المستخدمين وحسابات الخدمة إلى تحسين إدارة الهوية وتقليل زحف الامتيازات. هذا يعزز محاذاة الثقة الصفرية.
يعمل تحديد الأولويات القائم على المخاطر والإصلاحات الآلية على تقصير أوقات الاستجابة. يمكن للمؤسسات حل المشكلات قبل تصعيدها إلى حوادث.
تركز DSPM على تأمين البيانات الحساسة، بينما تتناول CSPM و DLP وإدارة البيانات جوانب مختلفة من أمان السحابة والامتثال.
تقوم DSPM بتعيين البيانات الحساسة ومخاطر الوصول، بينما تقوم CSPM بتحليل التكوينات السحابية وانتهاكات السياسة. يكشفان معًا ما إذا كانت التكوينات الخاطئة تعرض الأصول الحساسة.
تراقب DLP البيانات المتحركة لمنع التسرب، بينما تقوم DSPM بتقييم البيانات في حالة السكون عبر الخدمات السحابية. تعمل DSPM على تحسين دقة DLP من خلال اكتشاف وتصنيف أفضل.
تحدد إدارة البيانات السياسات ومعايير الملكية، بينما تحدد DSPM ظروف التعرض الحقيقية. تحدد الحوكمة التوقعات؛ يُظهر DSPM ما إذا كانت البيئات تلبي تلك التوقعات.
تكشف DSPM عن البيانات غير المُدارة أو المكررة أو المنسية عبر البيئات السحابية. هذا يقلل من مخاطر التعرض المخفية.
تحدد إدارة الوصول الأذونات المفرطة ومسارات الوصول غير المستخدمة والعلاقات الخطرة بين الهوية والبيانات. هذه الأفكار تعزز استراتيجيات أقل الامتيازات.
تقوم DSPM بتعيين البيانات الحساسة لأطر مثل GDPR و HIPAA و SOC 2. تعمل العلامات الآلية وإعداد التقارير على تبسيط عمليات التدقيق.
تحدد ميزة منع التعرض التكوينات الخاطئة مثل الوصول العام أو التشفير الضعيف أو إعدادات المشاركة غير الآمنة. إن معالجة هذه المشكلات مبكرًا تمنع حدوث تسربات عرضية.
يُظهر DSPM البيانات الحساسة التي تم الكشف عنها ومن تفاعل معها. هذا يحسن سرعة ودقة التحقيقات في الحوادث.
تسلط مراقبة دورة حياة التاريخ الضوء على النسخ القديمة والاحتفاظ غير الضروري ونشر البيانات غير الآمن. يمكن للفرق فرض سياسات دورة الحياة والاحتفاظ بشكل فعال.
تقوم حلول DSPM المدمجة في السحابة بفحص الخدمات السحابية وقواعد البيانات لتحديد المعلومات الحساسة وظروف التعرض. وهي توفر رؤية مستمرة من خلال ربط الحساسية بالتكوين وسياق الوصول.
تقوم هذه الأدوات بالكشف عن البيانات الحساسة عبر المستودعات وتعيين فئات الحساسية. التصنيف يبني الأساس لتقييم المخاطر الهادف.
فهي تحدد مسارات الوصول عبر المستخدمين والأدوار وحسابات الخدمة ومفاتيح API. وهذا يساعد المؤسسات على تعزيز سياسات أقل الامتيازات.
تقوم هذه الأدوات بتسجيل التعرض من خلال مزج الحساسية مع عمق الوصول ونقاط ضعف التكوين. يوجه تحديد الأولويات الانتباه إلى القضايا عالية التأثير.
تتخذ هذه الحلول إجراءات تصحيحية مثل ضبط الأذونات أو تصحيح التكوينات الخاطئة. تقلل الأتمتة من الجهد اليدوي وتفرض سياسات متسقة.
فهي تعمل على مواءمة البيانات الحساسة مع اللوائح الرئيسية وتوفر أدلة جاهزة للتدقيق. هذا يقلل من الجهد المطلوب لتقييمات الامتثال.
تحمي DSPM البيانات الحساسة مثل PII و PHI والمعلومات المالية وسجلات الأعمال الداخلية. والغرض منه هو تقليل التعرض الناتج عن التكوينات الخاطئة والوصول المفرط والنسخ غير المُدارة.
لا تحل DSPM محل CSPM أو DLP لأن كل أداة تتناول طبقة مختلفة من الأمان. إنه يعزز كلاهما من خلال إضافة رؤية تتمحور حول البيانات.
تقوم معظم منصات DSPM بإجراء مسح مستمر أو شبه فوري. هذا يضمن اكتشاف التغييرات في تخزين البيانات والأذونات بسرعة.
تستخدم فرق الأمان ومهندسو السحابة وقادة الامتثال ومجموعات الحوكمة رؤى DSPM. يقوم كل فريق بتطبيق هذه الأفكار من وجهات نظر تشغيلية مختلفة.
تدعم DSPM الامتثال من خلال تصنيف البيانات الحساسة وتعيينها لأطر مثل GDPR و HIPAA. كما أنه يبسط عمليات التدقيق من خلال توفير أدلة دقيقة عن النسب والتعرض.
تدعم DSPM عادةً البيئات متعددة السحابات والهجينة وSaaS من خلال عمليات تكامل API. يوفر هذا رؤية واسعة عبر أنظمة البيانات البيئية المتنوعة.
يوفر DSPM رؤية عميقة لكيفية تخزين البيانات الحساسة والوصول إليها وعرضها عبر البيئات السحابية الحديثة. وهذا يسمح للفرق بالتركيز على المخاطر الأكثر أهمية والاستجابة بدقة أكبر.
ومع توسع اعتماد السحابة، تحتاج المؤسسات إلى رؤية تركز على البيانات للحفاظ على وضع أمني قوي. يوفر DSPM الأساس للحد من التعرض والحوكمة المنسقة والمرونة على المدى الطويل.
