🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Credential theft has become one of the most reliable ways for attackers to breach modern organizations because identity now sits at the center of access. From cloud platforms and SaaS tools to internal applications and VPNs, valid credentials unlock systems without triggering traditional security defenses. When attackers log in as legitimate users, security controls often trust the activity by design, making credential theft especially difficult to detect.
According to the Verizon 2023 Data Breach Investigations Report, nearly 50% of breaches involved stolen credentials, while only a small percentage stemmed from vulnerability exploitation. Similarly, IBM’s 2023 Cost of a Data Breach Report identifies compromised credentials as the most common initial attack vector, responsible for 19% of all breaches, and often resulting in longer breach lifecycles and higher costs, underscoring how critical identity protection has become.
Learn how credential theft occurs, the techniques attackers use, the real-world impact on organizations, and the practical steps needed to detect and prevent credential-based attacks.
Credential theft is a cyberattack technique where attackers steal authentication data used to verify identity and grant access to systems, applications, or services. This data includes usernames and passwords, session cookies, API keys, access tokens, and authentication secrets. Once obtained, stolen credentials allow attackers to log in as legitimate users without exploiting software vulnerabilities or triggering traditional intrusion defenses.
Credentials represent identity, not infrastructure. When credentials are compromised, security controls that rely on trusted identity are bypassed by design. This makes credential theft highly effective at scale, because valid logins blend into normal user activity across cloud, SaaS, and enterprise environments.
Credential theft is not the same as general account compromise. Account compromise is the outcome, while credential theft is the method. An account can be compromised through other means, but credential theft specifically refers to the unauthorized acquisition and reuse of valid login material to gain trusted access.
Credential theft follows a repeatable sequence that attackers apply across industries and environments. The steps below explain the process in clear, practical terms.
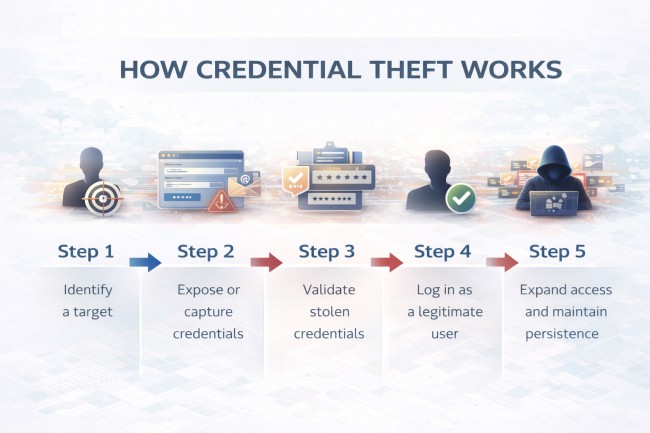
Attackers select users, organizations, or services that rely on password-based or weakly protected authentication. Public details such as email formats, login portals, and exposed services help narrow targets.
Credentials are obtained through phishing pages, malware, leaked databases, or insecure connections. The focus is on collecting valid login data rather than exploiting systems.
Stolen usernames and passwords are tested against real services to confirm they work. This validation is often automated to test large credential sets quickly and quietly.
Once validated, attackers log in using the stolen credentials. Because authentication succeeds normally, security controls often treat this activity as trusted user behavior.
Attackers move laterally, access additional systems, or generate new sessions and tokens to retain access. At this stage, credential theft often becomes the entry point for data theft, ransomware, or broader compromise.
Credential theft appears in several forms, but in practice, it is defined by the techniques attackers use to capture credentials or abuse them after they are stolen. These techniques target both systems and people, and attackers often chain multiple methods to increase success.

In a phishing attack, Attackers send emails, messages, or notifications that appear legitimate, such as security alerts or document requests. These messages lead users to fake login pages that closely resemble real services. When credentials are entered, they are sent directly to the attacker and reused immediately. This technique works because it exploits routine user actions and trust in familiar brands.
Malware installed on a device steals credentials by recording what users type or intercepting login data during normal activity. Through keylogging, malicious software silently records keystrokes when users enter usernames and passwords into legitimate websites, VPNs, or enterprise applications. Some malware captures login form data before it is encrypted, allowing credentials to be stolen even when no suspicious websites are involved.
In addition to capturing credentials during login, malware extracts credentials already stored on the system. This includes browser password databases, saved application credentials, cached authentication tokens, and configuration files containing secrets. Malware often runs quietly in the background for extended periods, exposing multiple accounts from a single infected device without noticeable signs of compromise.
Attackers take usernames and passwords from past data breaches and automatically test them across different services. Because many users reuse credentials, this technique allows attackers to gain access without directly interacting with victims.
Password spraying attempts a small number of commonly used passwords across many accounts to avoid lockout controls. Brute-force attacks target a single account with many password attempts. Both rely on weak password policies and insufficient monitoring.
Attackers intercept communication between users and services, often on unsecured or compromised networks. During this interception, login credentials, session cookies, or tokens are captured in transit, enabling access without alerting the user.
Instead of stealing passwords, attackers hijack active sessions by capturing authentication cookies or tokens from browsers or memory. These stolen sessions allow access even after passwords are changed and can bypass some multi-factor authentication protections.
Multi-factor authentication is bypassed through push notification fatigue, MFA relay attacks, or insecure fallback options. Attackers exploit implementation gaps rather than breaking the authentication mechanism itself.
Attackers manipulate individuals through phone calls, messages, or impersonation. Victims are pressured into revealing credentials, approving login requests, or resetting access. This technique succeeds because it exploits trust, authority, and urgency rather than technology.
In real attacks, these techniques are rarely used alone. Credentials may be captured through phishing, validated automatically, and then abused through session theft or MFA bypass, making identity compromise difficult to detect.
These real-life incidents demonstrate how credential theft facilitates large-scale compromise without exploiting software vulnerabilities.
Attackers first stole credentials from a third-party HVAC vendor connected to Target’s network. Using those valid credentials, they accessed internal systems and later compromised point-of-sale environments. The breach exposed payment data of over 40 million customers, demonstrating how credential theft bypasses perimeter defenses through trusted access.
A single employee reused a password that had been exposed in an unrelated breach. Attackers used that stolen credential to access Dropbox’s internal systems, leading to the exposure of more than 68 million user credentials. The incident showed how credential reuse amplifies risk years after initial theft.
Attackers obtained credentials from a developer through malware and used them to access a private GitHub repository. The repository contained cloud access keys, which allowed attackers to reach internal databases at Uber. This chain began with credential theft and escalated into full data access.
The ransomware attack on Colonial Pipeline was traced back to a compromised VPN account protected only by a password. The stolen credentials allowed attackers to log in remotely, triggering a shutdown of fuel distribution across parts of the United States. No software exploit was required.
Large-scale phishing and MFA fatigue campaigns targeted enterprise users, stealing credentials and session tokens. Attackers used these credentials to access email accounts across multiple organizations using Exchange Online, resulting in data theft and business email compromise without compromising Microsoft's infrastructure.
Credential theft causes widespread damage because attackers gain access using trusted identities. The consequences below explain the most common outcomes in simple terms.
These consequences show that credential theft is rarely a minor incident. The damage scales with the level of access compromised and often leads to full organizational exposure.
Credential theft is difficult to detect because attackers log in using valid credentials. Detection depends on identifying activity that deviates from a user’s normal behavior over time, rather than relying on a single alert.
Logins occur at abnormal times, from unfamiliar locations, or from devices not previously associated with the user. These deviations stand out when compared to historical login patterns.
An account logs in from geographically distant locations within a short period. This pattern indicates credential reuse from different locations.
Repeated authentication attempts across many accounts or services suggest credential stuffing or password spraying activity.
Accounts access systems, data, or administrative functions outside their typical role. This behavior often follows successful credential compromise.
Sessions persist unusually long, appear from multiple devices at the same time, or remain active after password changes. These signs point to session or token theft.
Usernames and passwords appear in breach dumps, underground forums, or public paste sites. Early identification reduces the time attackers can reuse credentials.
Email addresses, MFA settings, or recovery options are altered without user request. These changes are commonly used to maintain attacker access.
Effective detection relies on correlating multiple indicators across login behavior, session activity, and access patterns to identify misuse early and limit impact.
Preventing credential theft requires reducing how credentials are exposed and limiting what attackers can do if credentials are stolen. Effective prevention combines strong identity controls, user awareness, and organizational discipline.
Credential theft prevention is not a single control. Organizations reduce risk by combining authentication strength, continuous monitoring, user awareness, and fast response, making stolen credentials far less effective for attackers.
Credential theft targets identity rather than systems, allowing attackers to gain trusted access without exploiting technical vulnerabilities. By using valid credentials, attackers bypass security controls by design, which is why credential theft remains one of the most effective entry points in modern cyberattacks.
Credential theft is not unavoidable. Organizations can reduce risk by treating identity as a core security boundary and combining strong authentication, continuous monitoring, user awareness, and rapid response. When detection, prevention, and response work together, stolen credentials lose their value, and credential-based attacks become far less effective.
