🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Local networks operate on trust, with devices assuming that shared information is accurate and safe. This makes everyday communication fast and efficient, but also creates opportunities for abuse. ARP spoofing exploits this trust by redirecting traffic without detection, allowing attackers on the same network to intercept, monitor, or manipulate communication while systems appear to function normally.
This threat is more common than many realize. According to the SANS Institute, man-in-the-middle (MITM) techniques, particularly ARP spoofing, remain among the most frequently observed attack methods on unsecured local networks. These attacks are especially common on public Wi-Fi environments and flat enterprise LANs where network segmentation, encryption, and authentication controls are weak or absent.
That’s why understanding how ARP spoofing works and how it can be prevented is essential for protecting internal network traffic from silent interception.
ARP spoofing is a network-based attack where an attacker transmits forged Address Resolution Protocol (ARP) messages to map their MAC address to a legitimate IP address on a local network.
It exploits the inherent trust model of ARP, as devices accept ARP replies without authentication. This behavior enables the attacker to associate their hardware address with the IP address of a router, server, or endpoint.
After the mapping is altered, network traffic is rerouted through the attacker’s device. The attacker captures credentials, inspects communications, or modifies transmitted data without alerting users.
In security terms, spoofing represents deliberate impersonation. In ARP spoofing, the attacker impersonates a trusted device by claiming its IP address within the same network segment.
Address Resolution Protocol (ARP) is a network protocol that connects an IP address to a physical MAC address on the same local area network (LAN). This connection allows devices to send data to the correct hardware destination.
This connection is required because devices send data using MAC addresses, not IP addresses. Here's how ARP works:
ARP has no built-in verification. Devices automatically accept any ARP reply and update their ARP tables. This lack of authentication creates the weakness that attackers exploit in ARP spoofing.
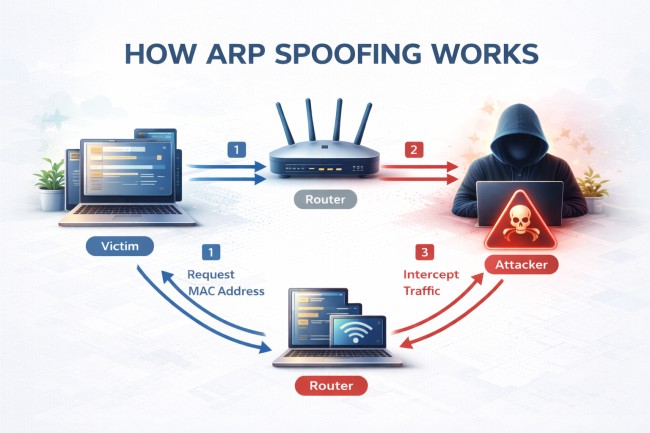
ARP spoofing works by manipulating ARP table entries on a local network to redirect traffic through the attacker’s device instead of the legitimate destination.
First, the attacker gains access to the same local network segment as the target systems. This network access enables direct exchange of ARP messages with connected devices.
Second, the attacker transmits forged ARP replies that falsely associate their MAC address with the IP address of a trusted system, such as the default gateway or router. These unsolicited ARP responses exploit the protocol’s lack of authentication.
Third, victim devices update their ARP caches with the fraudulent IP-to-MAC mapping. This cache modification causes devices to forward traffic to the attacker rather than the intended host.
Fourth, redirected traffic flows through the attacker’s system. The attacker intercepts credentials, inspects sensitive communications, modifies transmitted data, or disrupts connectivity without generating visible alerts.
Finally, the attacker continuously resends forged ARP replies to maintain the malicious mapping. This persistent transmission prevents legitimate ARP updates and sustains control over network traffic.
ARP spoofing has specific characteristics that explain its behavior, limits, and risks on a network. Here are the key characteristics:
ARP spoofing only works on the same local network. The attacker must be connected to the same LAN or Wi-Fi network as the victim devices.
ARP spoofing exploits blind trust. Devices accept ARP replies without verification, which allows attackers to send false address information.
ARP spoofing places the attacker between two communicating devices. All data passes through the attacker before reaching its intended destination.
ARP spoofing usually does not break connections. Communication continues normally, which makes the attack difficult for users to notice.
ARP spoofing changes entries stored in ARP tables. These entries are temporary, which is why attackers must keep sending fake replies.
ARP spoofing only works while the attacker stays active on the network. If the attacker stops sending forged ARP messages, devices eventually correct their ARP tables.
ARP spoofing does not install software or change files. The attack works entirely by redirecting network traffic rather than altering devices themselves.
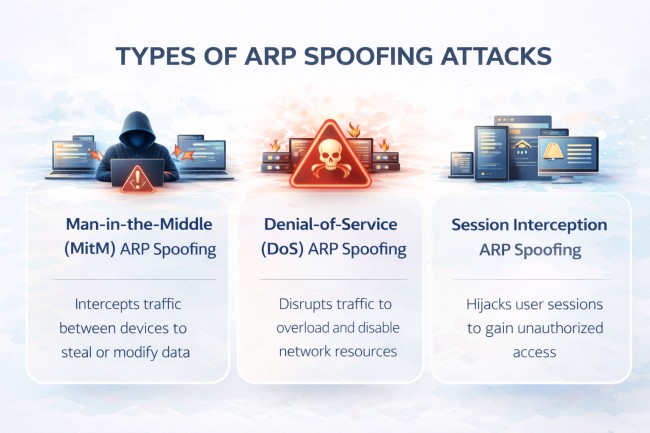
ARP spoofing attacks are commonly grouped by how attackers use the redirected network traffic. Here are the main types of ARP spoofing:
This is the most common type of ARP spoofing. The attacker places their device between two communicating systems, such as a user and a router. All traffic passes through the attacker, allowing them to read, capture, or modify data while communication appears normal.
In this type, the attacker uses ARP spoofing to disrupt network communication. By sending incorrect address information, the attacker prevents devices from reaching the correct destination. This results in lost connectivity, dropped sessions, or complete network interruption.
This type focuses on taking over active network sessions. By intercepting traffic, the attacker captures session identifiers and gains access to accounts or services without logging in directly. This allows unauthorized access using an existing session.
The key difference between ARP spoofing and ARP poisoning lies in action versus result. ARP spoofing is the attacker’s action of sending fake ARP messages. ARP poisoning is the condition created when devices store incorrect address information because of those messages.
In real-world usage, these terms often appear together. Security tools and articles may use “ARP poisoning” to describe the corrupted network state, while “ARP spoofing” describes how the attacker caused it. Both refer to the same attack process but from different viewpoints.
In simple terms, ARP spoofing describes what the attacker does. ARP poisoning describes what happens to the network. Here is the comparison table to better understand:
These real incidents show how ARP spoofing succeeds on trusted local networks and leads to data exposure or service disruption.
In multiple documented cases since 2018, attackers on public Wi-Fi networks used ARP spoofing tools such as Ettercap to impersonate routers. The victims were cafe, airport, and hotel users sharing the same network. Dozens of users on a single hotspot were affected at once. Attackers intercepted login credentials, emails, and browsing sessions, leading to account takeovers and privacy loss.
In 2019, an internal attacker within a corporate office network performed ARP spoofing to impersonate the default gateway. Using freely available network spoofing tools, the attacker redirected traffic from multiple employee devices. The organization experienced credential theft and unauthorized access to internal systems, forcing password resets and network reconfiguration across departments.
In 2020, a student on a university LAN launched an ARP spoofing attack to monitor traffic between student devices and campus servers. Hundreds of users connected to the same subnet were exposed. The attack allowed session interception and data monitoring, resulting in temporary network shutdowns and stricter access controls across the campus.
In 2021, a small business experienced repeated network outages caused by ARP spoofing. An attacker on the same local network sent forged ARP replies to block communication between devices and the router. The business lost internet access for several hours, disrupting operations and customer transactions.
ARP spoofing is detected by monitoring live network behavior and identifying incorrect address mappings that should not exist. Because the attack works silently, detection focuses on real-time changes rather than visible system damage.
Reliable detection comes from combining signals. When ARP table changes, duplicate mappings, and abnormal traffic paths appear together, ARP spoofing is confirmed.
ARP spoofing is prevented by adding checks to ARP traffic, controlling who can join the network, and protecting data even if traffic is intercepted.
Dynamic ARP Inspection is a switch feature that blocks fake ARP messages before they reach devices. The switch checks each ARP reply and verifies whether the IP address and MAC address match a trusted record. When the mapping is wrong, the switch drops the packet. This stops attackers from poisoning ARP tables because their forged ARP replies never get accepted by other devices.
DHCP snooping is a switch feature that watches DHCP traffic and builds a trusted list of which device owns which IP address. The switch records the real IP-to-MAC assignments it sees from the legitimate DHCP server.
This record becomes a reliable reference for other protections, especially Dynamic ARP Inspection. When DHCP snooping is enabled, it becomes harder for attackers to pretend they own someone else’s IP address because the network has a verified source of truth.
Static ARP entries are manual IP-to-MAC mappings set on important devices, such as servers, gateways, and network appliances. Because these entries do not change automatically, forged ARP replies cannot overwrite them. Static ARP works best for critical systems with fixed addresses because it requires maintenance when hardware changes.
Network segmentation divides one large network into smaller, separated zones. Segmentation limits how far an attacker can reach after joining the network. If an attacker performs ARP spoofing inside one segment, they can only affect devices in that segment, not the entire organization. This reduces the blast radius and keeps critical systems away from risky user networks.
Encryption protects the content of network traffic, even if an attacker redirects it. When users rely on HTTPS, secure email protocols, and VPN connections, intercepted traffic becomes unreadable. Encryption reduces credential theft and data exposure because attackers see scrambled data instead of passwords, session tokens, or private information.
Port security controls which devices are allowed to connect to a switch port. It can limit the number of MAC addresses on a port or lock a port to specific approved devices. This blocks many ARP spoofing attempts because the attacker cannot join the network easily in the first place. When an unknown device connects, the port can shut down or restrict traffic automatically.
Continuous monitoring watches ARP activity and traffic patterns in real time. Monitoring systems alert when they see unusual ARP replies, frequent ARP changes, or duplicate IP-to-MAC mappings. Early alerts allow teams to isolate the attacking device quickly, before large amounts of traffic are intercepted.
Disabling unused services reduces unnecessary exposure on the network. While this does not directly change ARP behavior, it reduces the chances that attackers gain a foothold on the local network in the first place. Fewer exposed services and fewer open paths reduce the overall opportunities for misuse.
ARP spoofing exploits a basic weakness in how local networks trust address information. By sending false ARP messages, attackers can quietly place themselves between devices and control how data moves across the network. This makes ARP spoofing especially dangerous in shared or poorly secured environments where trust is assumed.
Organizations can reduce this risk by strengthening network controls and removing blind trust. Verifying address mappings, limiting who can connect to the network, and encrypting traffic together close the gaps that ARP spoofing depends on.
