🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
A port scan is a method used to understand how a system’s network ports respond when they receive connection attempts. The responses help determine whether each port is open, closed, or filtered by security controls.
Because every port is tied to a specific service, scanning reveals which functions a system is making available to the outside network. These discoveries can range from web services and email servers to remote access tools or unused services accidentally left exposed.
Port scanning remains an essential part of security assessment because it provides visibility into how systems communicate with the world. When performed correctly, it helps identify unnecessary exposure before someone else discovers it.
Port scans are used because they reveal what a system is actually exposing to the outside world, not what administrators assume is exposed.
A port scan works by sending controlled connection attempts to selected ports and analyzing how the system responds. These reactions reveal whether a port is open and listening, closed, or filtered by network security tools.
As the scan progresses, the responses also show whether any devices are quietly filtering traffic along the path. This makes it possible to identify firewalls or intermediary controls without accessing the services behind them.
Port numbers range from 0 to 65,535, and scanning them builds a clear picture of a system’s exposure. Open or unexpected ports may indicate misconfigurations or outdated services that require attention.
Port scanning can be performed in several ways, and each method helps uncover different characteristics of a system’s network behavior.
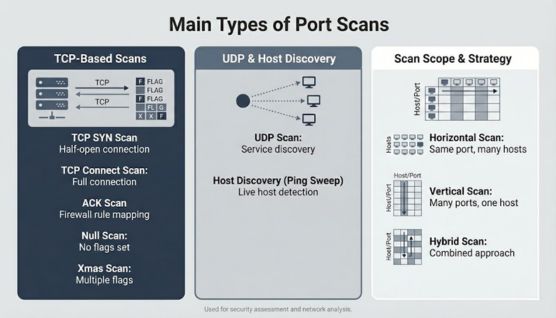
SYN scan sends the initial handshake request to see how the system reacts without completing the connection. This partial exchange blends into regular traffic and makes the scan harder to detect.
A connect scan completes the entire handshake, making it straightforward and highly reliable. However, its activity usually appears in logs, which makes it more visible.
UDP scan sends datagrams to specific ports and waits for error messages or silence to determine the port’s state. This approach is slower and sometimes less predictable because UDP lacks a formal handshake.
ACK scan focuses on how firewalls handle unexpected packets rather than identifying open ports directly. It reveals which ports are being filtered and how those filters behave.
FIN scan sends packets with only the FIN flag, prompting some systems to reveal information unintentionally. Older or misconfigured devices tend to respond inconsistently to such traffic.
Null scan sends packets without any flags, forcing the system to interpret a request that lacks conventional structure. This ambiguity can expose details that basic filtering mechanisms fail to handle correctly.
Xmas scan uses multiple packet flags simultaneously to generate a pattern that stands out on the network. Systems that respond differently to these unusual packets can unintentionally disclose port behavior.
A ping sweep helps identify which hosts on a network are active before running deeper scans. It works by sending echo requests and recording which devices respond.
Horizontal scans test a single port across multiple hosts to reveal widespread weaknesses. Vertical scans explore many ports on one host, while hybrid scans combine both methods for broader mapping.
Port scans give attackers critical information about how a system is configured and where potential weaknesses exist. This insight helps them shape their strategy before attempting any deeper intrusion.
Open ports expose services such as HTTP, SSH, SMB, or RDP, each of which could become an entry point. Attackers look for outdated or unnecessary services because they are easier to exploit.
Some services reveal software versions or banner details when probed, which helps attackers match them with known vulnerabilities. This information often guides the next step in the attack chain.
Scanning across multiple ports and systems reveals how the network is organized and where entry points cluster. This mapping helps attackers decide which systems to target first and how to navigate once inside.
Port scanning itself is not harmful, but its purpose often determines the level of risk it introduces. What begins as a simple probe can quickly become part of a larger attack sequence.
Unauthorized scanning can violate laws because it tests the boundaries of a protected system. Many jurisdictions view it as attempted access regardless of whether exploitation occurs.
Unmonitored scanning reveals which systems are reachable and which services may be vulnerable. This information enables attackers to select the easiest targets with precision.
Authorized scans allow organizations to uncover weaknesses before real attackers find them. These controlled assessments provide valuable insight without introducing unnecessary risk.
Detecting port scans requires a clear understanding of normal traffic patterns and the ability to recognize unusual activity. Sudden spikes in connection attempts across multiple ports are often early signs of reconnaissance.
Firewalls track incoming connection attempts and flag patterns that suggest scanning. Reviewing these logs regularly helps identify probing before it escalates.
Intrusion detection and prevention systems use signatures to spot known scanning behaviors. When detected, these systems can generate alerts or automatically block suspicious sources.
A SIEM aggregates logs from various devices and correlates them to reveal scanning activity that may go unnoticed individually. This broad visibility helps analysts spot patterns across the entire environment.
Behavioral tools focus on how traffic behaves rather than what it contains. This approach makes it effective for detecting stealth scans that mimic normal communication.
Preventing port scans requires limiting what outsiders can learn and reducing how many services are exposed. A well-controlled network surface makes reconnaissance far less effective.
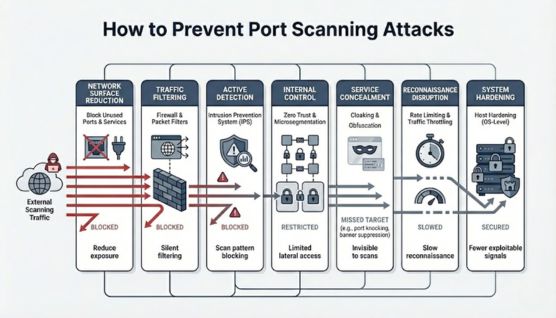
Closing unnecessary ports eliminates easy targets for attackers. This reduces the amount of information a scan can uncover.
Fine-tuned firewall rules help manage unsolicited traffic and reduce visibility into system behavior. Effective filtering ensures that scanners receive as little information as possible.
IPS tools identify scanning patterns and respond by blocking or throttling suspicious traffic. This real-time reaction helps stop reconnaissance early.
Zero Trust limits movement within the network and narrows what each system can reach. Microsegmentation adds another layer of control by isolating sensitive services.
Techniques like port knocking hide services behind intentional triggers. This keeps them invisible until a legitimate user activates them.
Restricting the speed of incoming requests disrupts high-speed scanning attempts. Slower scans are easier to detect and less useful to attackers.
Disabling unnecessary services and applying updates reduces the risk of exploitation. A hardened system offers fewer clues during a scan.
Port scanning tools differ in speed, depth, and the type of insights they provide. Security teams choose tools based on the scope and complexity of their assessment needs.
Nmap remains the most widely used port scanner because it supports a broad range of techniques and provides detailed output. It is a staple in both security audits and network discovery tasks.
Masscan specializes in high-speed scanning that can cover large address spaces quickly. Its performance makes it valuable for wide-area exposure analysis.
These tools combine scanning with vulnerability assessment to provide additional context. Cross-referencing port results with known weaknesses helps prioritize remediation.
Zmap is built for Internet-scale research and uses single-packet probing to maximize efficiency. It excels at identifying trends across vast networks.
Mitigating port scanning risks involves reducing the amount of information attackers can gather and strengthening overall exposure management. A disciplined approach helps organizations stay ahead of reconnaissance attempts.
Consistent monitoring helps detect suspicious patterns before they escalate. Regular log review adds the context needed to identify early reconnaissance.
Frequent audits catch unnecessary open ports and outdated services. Removing these exposures decreases the likelihood of successful scanning.
Segmentation limits how far a scan can reach and contains its impact. Smaller zones provide fewer visible targets from the outside.
Cloud environments and remote access setups often expose ports unintentionally. Regular reviews help ensure these configurations do not expand the attack surface.
CloudSEK incorporates port scanning into its broader effort to map and secure an organization’s external attack surface. Its BeVigil Enterprise platform performs continuous scans across IPv4 and IPv6 to reveal publicly accessible ports and services.
The platform’s Network Scanner builds a complete inventory of external assets, including domains, subdomains, and internet-facing systems. Once mapped, it highlights open ports, misconfigurations, and exposed services that increase the risk of unauthorized access.
CloudSEK also provides clear remediation guidance so security teams know exactly where to focus their efforts. By pairing automated discovery with actionable insight, the platform helps reduce blind spots and reinforce perimeter defenses.
