🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
DNS sits at the center of how the internet functions, quietly directing every request to the correct destination. When attackers interfere with this process, the impact spreads beyond a single system, affecting websites, applications, and users at the same time. DNS attack exploits this dependency to disrupt access, redirect traffic, or intercept communication at scale.
The risk of a DNS attack is widespread. According to Verisign’s DNS Threat Report, more than 40% of organizations experienced a DNS-related attack in a single year, often resulting in service downtime or data exposure. That’s why it is essential to understand what a DNS attack is, how it works, the main types involved, why it is dangerous, and how to prevent it.
A DNS attack is a cyberattack that targets the Domain Name System (DNS) to disrupt, redirect, or control how users access online services. These attacks interfere with DNS resolution, the process that translates domain names into IP addresses.
Attackers target DNS because it controls access to the internet. When DNS is compromised, users cannot reach websites, applications, or online services even if those services are operating normally.
DNS attacks are used to block access, redirect users to malicious destinations, or intercept traffic at scale. By manipulating DNS, attackers gain wide control over network communication without directly attacking individual systems.
Before knowing how a DNS attack works, it is essential to understand what DNS is and how it functions.
The Domain Name System (DNS) is a component of the Internet infrastructure. It translates human-readable domain names into numerical IP addresses that computers use to communicate. This translation allows users to access websites and services without memorizing IP addresses.
Here’s how it works: When a user enters a website name, the request is sent to a DNS resolver. The resolver asks a series of DNS servers where the correct IP address is stored. Once the IP address is found, the resolver returns it to the user’s device.
The device then connects to the correct server using that IP address. This entire process happens in seconds and occurs every time a website, app, or online service is accessed.
DNS is open and widely trusted. This trust and constant use across the internet make DNS a critical system and a valuable target for attackers who want to disrupt or control internet access.
A DNS attack exploits the process used to translate website names into their corresponding IP addresses. Here’s how they generally work, step by step:

When a user enters a website address, their computer sends a request to a DNS server to find the matching IP address.
Attackers target this communication path. They can intercept or redirect the request before it reaches the legitimate DNS server.
The attacker sends back a fake DNS response that contains a false IP address, tricking the user’s device into connecting to a malicious site.
The compromised DNS entry leads the user to a counterfeit website that looks like the real one. These fake sites are often used to steal login credentials or deliver malware.
Once successful, the attack can spread through altered DNS records on other servers, affecting many users who rely on the same domain information.
Some attackers implant persistent DNS changes or use malware to keep users directed to malicious servers even after system restarts or DNS cache resets.
DNS attacks are categorized by how attackers misuse the DNS system and what result they aim to achieve. Each type targets a specific weakness in how DNS resolves, stores, or responds to requests.
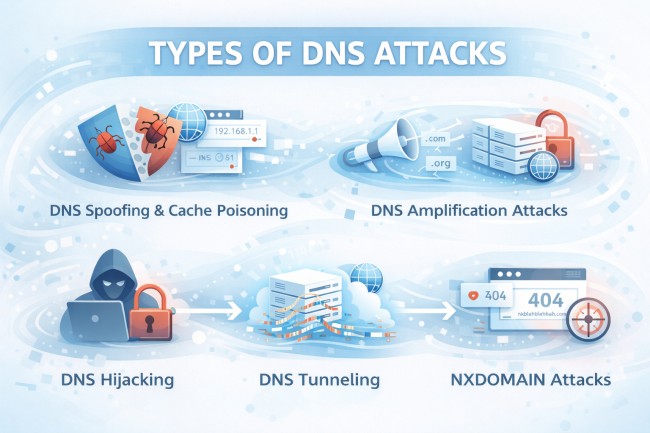
In this attack, the attacker’s goal is redirection. Attackers send fake DNS responses to a DNS resolver. The resolver stores this incorrect information in its cache and later serves it to users. As a result, users are directed to malicious or unintended websites even though they typed the correct domain name.
In this attack, Attackers target public DNS servers and the victim’s network bandwidth. Attackers send very small DNS requests while spoofing the victim’s IP address as the source. DNS servers reply with much larger responses, which are sent to the victim instead. These amplified responses flood the target’s network, overwhelming bandwidth and causing websites or services to become unreachable.
DNS hijacking happens when attackers change DNS settings on routers, devices, or DNS servers. Once changed, all DNS queries are resolved using attacker-controlled servers. This allows attackers to redirect users, inject ads, steal credentials, or block access entirely.
DNS tunneling abuses DNS queries to hide data inside normal-looking traffic. Attackers use DNS requests to communicate with malware or move data out of a network. Because DNS traffic is often allowed through firewalls, tunneling can remain unnoticed for long periods.
NXDOMAIN attacks focus on exhausting DNS resources. Attackers send large volumes of requests for domain names that do not exist. DNS servers spend processing power responding to these failed requests, which slows down or blocks legitimate DNS resolution.
DNS attacks are dangerous because they disrupt access at the foundation of the internet. When DNS is manipulated or overwhelmed, users cannot reach websites or applications even though those services are still running, creating immediate outages.
DNS attacks enable traffic redirection and silent data exposure. By controlling DNS responses, attackers can send users to fake destinations, intercept communication, or steal credentials while domain names appear legitimate.
DNS attacks scale rapidly because DNS serves many users at the same time. A single compromised resolver or DNS provider can affect thousands or millions of users, turning one attack into widespread disruption.
DNS attacks cause direct business and reputational damage. Service downtime leads to lost revenue, broken customer trust, and operational recovery costs. Repeated DNS incidents weaken confidence in online services and infrastructure.
DNS attacks often become entry points for larger attacks. Redirected traffic can deliver malware, support phishing campaigns, or bypass security controls, allowing attackers to expand control across systems and networks.
These incidents show how attacks against DNS infrastructure can disrupt access, redirect traffic, and affect millions of users at once.
In October 2016, attackers used the Mirai botnet to launch a DNS amplification attack against Dyn. By overwhelming Dyn’s DNS servers with massive traffic, the attackers disrupted name resolution for many popular websites. Services such as Twitter, Netflix, GitHub, and Spotify became unreachable for millions of users across North America and Europe. The attack succeeded because many major websites depended on a single DNS provider.
In November 2018, attackers exploited internet routing weaknesses to redirect DNS traffic intended for Google. By manipulating routing paths and DNS resolution, the attackers briefly intercepted user traffic. Although the disruption was short-lived, the incident showed how DNS trust combined with routing errors can expose global traffic to interception.
In April 2019, attackers compromised a domain registrar account and altered DNS records managed through Amazon Route 53. Users attempting to reach legitimate cryptocurrency services were redirected to a fake website that stole credentials. The attack worked because DNS records were changed at the source of trust, causing all users to receive malicious responses.
Between 2019 and 2020, a state-linked group carried out the Sea Turtle campaign by targeting DNS registrars and authoritative DNS servers. Government agencies, telecom providers, and technology companies across multiple countries were affected. By controlling DNS infrastructure, the attackers redirected traffic to their own systems, enabling long-term monitoring and credential collection. The campaign succeeded because DNS changes propagated silently across networks.
In July 2020, a configuration error during mitigation efforts caused a DNS-related outage at Cloudflare. Thousands of websites became unreachable worldwide. While not malicious, the incident highlighted how even small DNS misconfigurations can cause widespread disruption due to the central role DNS plays.
DNS attacks are detected by continuously monitoring DNS activity and identifying behavior that breaks normal resolution patterns. Because DNS runs silently in the background, detection relies on real-time observation rather than visible system errors.
Here are some useful methods to detect DNS attacks:
Security teams watch for sudden spikes in DNS queries, repeated requests, or large volumes of random domain lookups. These patterns often indicate amplification attacks, tunneling activity, or attempts to overload DNS servers.
This technique checks whether DNS responses change without authorization. When trusted domain names suddenly resolve to unfamiliar IP addresses, it signals possible DNS hijacking or cache poisoning.
Traffic analysis measures the balance between DNS requests and responses. Large response floods or uneven traffic volumes reveal amplification-based DNS attacks targeting infrastructure.
DNS logs provide a detailed record of queries, responses, and failures. Reviewing these logs helps identify repeated resolution errors, suspicious domains, or abnormal request behavior over time.
This method compares current DNS activity to established normal behavior. Significant deviations from baseline resolution patterns indicate manipulation or abuse of DNS services.
Threat intelligence data identifies known malicious domains and attack infrastructure. When internal DNS activity matches known threat indicators, detection becomes more accurate and faster.
DNS attacks are confirmed by correlating multiple signals at the same time. When abnormal queries, response changes, and traffic spikes appear together, active DNS abuse is confirmed.
DNS attacks are prevented by protecting DNS integrity, limiting misuse, and keeping DNS services reliable under pressure. Prevention works best when technical controls are combined with consistent oversight.
Here are the best tactics to prevent DNS attacks :
DNS Security Extensions protect DNS responses from being altered. DNSSEC uses digital signatures so resolvers can confirm that DNS data is authentic. This stops attackers from inserting fake DNS records through spoofing or cache poisoning.
Rate limiting controls how many DNS requests a server accepts from one source. Traffic filtering blocks malformed or suspicious queries. These measures reduce the impact of amplification and flood-based DNS attacks.
Distributed DNS spreads services across multiple servers and locations. If one server is attacked or fails, others continue resolving requests. This design prevents single points of failure and keeps services available.
A secure configuration removes common weaknesses. Disabling open recursion, restricting zone transfers, and locking down administrative access prevent attackers from abusing misconfigured DNS servers.
Registrar security protects DNS at its source. Strong authentication, account monitoring, and change approvals prevent attackers from hijacking domains by altering authoritative DNS records.
Ongoing monitoring watches DNS traffic in real time. Alerts highlight sudden spikes, response changes, or suspicious domains, allowing quick action before attacks spread.
Strong access controls protect DNS settings from unauthorized changes. Change management ensures DNS records are modified only through approved processes, reducing the risk of hijacking.
Regular testing checks whether DNS protections still work as expected. Periodic reviews help identify gaps before attackers find them.
DNS attacks target a core layer of the internet that every online service depends on. By manipulating or overwhelming DNS resolution, attackers can block access, redirect users, or intercept traffic without directly attacking applications or servers.
These attacks scale quickly because DNS serves many users at the same time. A single weakness in DNS infrastructure, configuration, or domain ownership can affect entire organizations, platforms, or regions. That’s why it is essential to secure DNS.
Organizations must treat DNS as critical infrastructure. Protecting DNS integrity, securing domain control, and monitoring DNS behavior continuously limits disruption and prevents attackers from abusing.
