🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Key Takeaways:
In cybersecurity, a botnet refers to a network of devices that have been compromised through malware and brought under remote control. Operation depends on both the infected devices and the systems used by an attacker to manage them as a single coordinated network.
Compromised devices within a botnet communicate with external control servers, often known as command-and-control (C2) systems, which deliver instructions to the network. Infected machines are commonly referred to as bots or zombie devices because activity occurs without the owner’s knowledge or consent.
Within the context of cybercrime, botnets enable malicious activity to be distributed across many independent systems, reducing attribution and increasing operational scale. Combined malware infection, attacker-managed control channels, and synchronized network behavior distinguish botnets from isolated security incidents.
Botnets work through a structured sequence that allows attackers to compromise devices, maintain control, and coordinate malicious activity across a network.
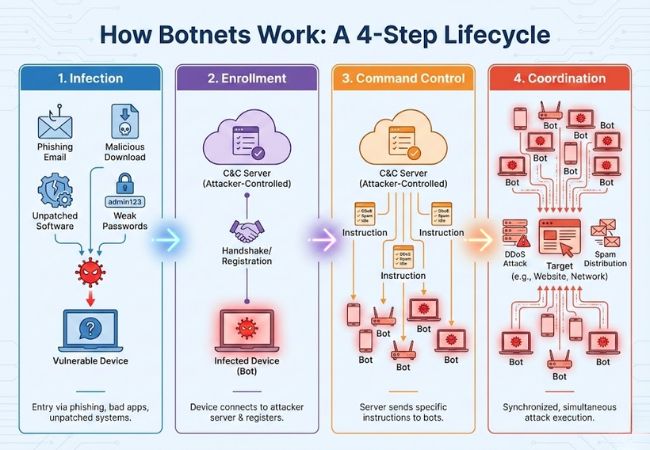
Malware enters systems through phishing emails, malicious downloads, unsafe applications, or exposed services. Weak passwords and unpatched software significantly increase the likelihood of successful compromise, especially across IoT and mobile devices.
Once malware executes, the infected device establishes outbound communication with attacker-controlled servers. Successful communication registers the device into the botnet and prepares it to receive instructions.
Instructions are delivered through command-and-control infrastructure that directs bot behavior. Actions can include sending traffic, distributing spam, or remaining idle until activated.
Synchronized execution allows thousands of compromised devices to act simultaneously. Distributed coordination increases attack effectiveness while reducing the chance of immediate detection.
Botnets are used to automate and scale malicious activities that would be difficult or impossible to perform from a single system.
Botnets are commonly used to carry out distributed denial-of-service attacks by overwhelming servers, websites, or networks with massive volumes of traffic. Coordinated requests from thousands of infected devices can disrupt services, cause outages, and result in financial or operational damage.
Large botnets enable attackers to send spam and phishing emails at scale. Malicious messages often distribute malware, harvest credentials, or promote fraudulent schemes.
Automated bots generate fake clicks, views, and interactions to manipulate advertising platforms. Artificial traffic distorts analytics data and leads to significant revenue losses.
Infected devices may be exploited to mine cryptocurrency or relay traffic without permission. Excessive resource usage degrades performance and increases energy consumption for victims.
Botnets manipulate online platforms by inflating engagement metrics or coordinating fake activity. Abuse commonly targets social media networks, video platforms, search results, and online services without requiring direct access to user accounts.
Botnets are categorized based on how control is structured, which devices are targeted, and how communication is maintained across the network.
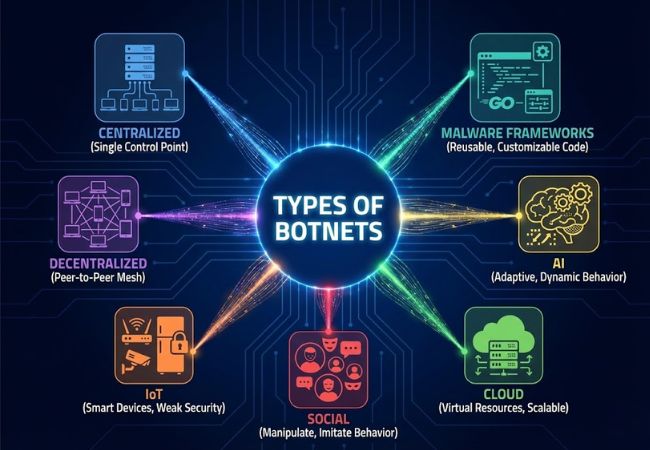
Control relies on one or more central servers that issue commands to infected devices. Simple management makes coordination efficient, but disruption becomes easier once control infrastructure is identified.
Peer-to-peer communication removes reliance on a single control point. Resilience increases because infected devices can continue operating even when parts of the network are taken offline.
Routers, cameras, smart appliances, and similar devices are frequently targeted due to weak default security settings. Limited processing power and infrequent updates make cleanup difficult once infection occurs.
Automated or compromised accounts are coordinated to manipulate discussions, engagement metrics, or public perception. Human behavior imitation often allows these networks to evade detection longer than traditional botnets.
Virtual servers and hosting environments are abused to launch attacks rapidly and at scale. Elastic resources enable attackers to increase power on demand while obscuring infrastructure origins.
Automation techniques are used to adjust behavior, timing, and traffic patterns dynamically. Adaptive control reduces predictability and complicates traditional detection methods.
Reusable botnet codebases enable rapid deployment and customization. Implementations written in languages such as Go are common, while references to “free botnets” usually involve leaked or illicit tools.
Well-known botnets are typically identified through government advisories and coordinated takedown efforts that reveal how large-scale botnet operations function in practice.
Mirai is an IoT-focused botnet family that spreads by exploiting weak or default credentials on internet-connected devices. Security authorities reported Mirai-linked DDoS activity reaching close to 1 terabit per second, highlighting the destructive potential of consumer hardware at scale.
Avalanche operated as a botnet-enabling criminal infrastructure that used fast-flux techniques to support multiple malware operations. International investigations indicated that at least 500,000 computers worldwide were infected and controlled on a daily basis.
The PRC-linked router botnet campaign relied on compromised routers and IoT devices to build a large proxy-based attack platform. National cybersecurity reporting confirmed over 260,000 devices were involved as of mid-2024.
RondoDox represents a newer generation of IoT botnets that target network appliances and vulnerable web applications. Government alerts documented active exploitation activity and ongoing expansion as of January 2026.
A later Mirai-based campaign demonstrated how older botnet families continue to resurface through new exploit chains. National advisories confirmed active targeting of industrial routers and smart-home devices in early 2025.
Retadup functioned as a malware-driven botnet used for cryptomining and unauthorized remote control. Law-enforcement intervention resulted in the remote disinfection of more than 850,000 computers, making it one of the largest cleanup operations on record.
Simda was a self-propagating botnet that compromised systems through malicious redirections and exploit kits. International operations estimated over 770,000 infected computers worldwide, underscoring how quickly botnets can spread when left unchecked.
Botnet infections are often identified by observing abnormal behavior at the device or network level rather than by visible malware alerts.
Unusual slowdowns, frequent crashes, or unexplained background activity can indicate botnet-related compromise. Unexpected system changes, such as disabled security tools or unknown running processes, further increase suspicion.
Persistent outbound connections to unfamiliar servers or sudden traffic spikes may signal command-and-control communication. Repeated requests occurring at regular intervals are another common indicator of botnet activity.
Security scanners, intrusion detection systems, and specialized botnet trackers help identify compromised devices. Network tests and traffic analysis tools are commonly used to confirm infection and assess spread.
Preventing botnet attacks focuses on reducing exposure to compromise and limiting the ability of attackers to maintain control over infected devices.
Regular patching closes vulnerabilities commonly exploited to install botnet malware. Firmware updates are especially important for routers, cameras, and other IoT devices that are frequently targeted.
Unique passwords and multi-factor authentication reduce the risk of unauthorized access. Credential hygiene is critical for devices and services exposed to the internet.
Continuous monitoring helps identify unusual traffic patterns associated with botnet activity. Early detection limits spread and reduces the impact of coordinated attacks.
Security features should be enabled on all endpoints, including firewalls and access restrictions. Removing unused services and limiting remote access further reduces attack surfaces.
Advanced email filtering blocks phishing messages that commonly deliver botnet malware. Reduced exposure to malicious attachments and links lowers initial infection risk.
Network segmentation limits how far botnet malware can spread after compromise. Restricted lateral movement prevents attackers from controlling large numbers of devices at once.
Botnets remain a foundational threat in cybersecurity because large networks of compromised devices allow attackers to operate at scale with minimal exposure. Understanding how botnets form and function is essential for recognizing why they continue to power many modern attacks.
Effective defense against botnets depends on early detection, consistent security practices, and awareness of common infection paths. Strong authentication, timely updates, and network monitoring significantly reduce the likelihood of devices being absorbed into botnet networks.
As connectivity expands across personal, enterprise, and IoT environments, botnet activity is likely to evolve rather than disappear. Ongoing vigilance and coordinated defensive efforts remain critical to limiting their impact over time.
Botnets are illegal in most jurisdictions because they involve unauthorized access, device control, and coordinated cybercrime. Operating, selling, or renting a botnet is commonly prosecuted under computer misuse and cybercrime laws.
Personal devices can become part of a botnet when malware infects systems through phishing, malicious downloads, or weak credentials. Compromise often occurs without visible signs to the device owner.
IoT devices are more vulnerable to botnets due to default passwords, limited security controls, and infrequent updates. Constant internet connectivity further increases exposure to automated attacks.
Individual botnets can be disrupted or dismantled through coordinated efforts, but complete elimination is unlikely. New botnets continue to emerge as attackers adapt techniques and exploit new vulnerabilities.
