🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
الوجبات السريعة الرئيسية:
يتم استهداف الرعاية الصحية أكثر من أي قطاع آخر لأن المهاجمين يمكنهم تحقيق الدخل من سجلات المرضى واستغلال الأنظمة السريرية القديمة التي تفتقر إلى الضوابط الأمنية الحديثة. إن الجمع بين البنية التحتية القديمة وتوافر الخدمات الحيوية يجعل الرعاية الصحية معرضة بشدة للهجمات التي يحركها الابتزاز.
يجذب التصنيع مجرمي الإنترنت بسبب بيئات OT - IT المترابطة التي تخلق نقاط ضعف مخفية عبر خطوط الإنتاج. يستغل المهاجمون هذه الثغرات لتعطيل العمليات وسلاسل التوريد، مع العلم أن وقت التوقف عن العمل يخلق نفوذًا قويًا لطلبات الفدية.
تواجه الخدمات المالية استهدافًا مستمرًا لأنها تخزن بيانات الهوية عالية القيمة وتعالج المعاملات النقدية الحساسة عبر المنصات الرقمية. يستخدم المجرمون سرقة بيانات الاعتماد والتصيد الاحتيالي والبرامج الضارة لتجاوز الدفاعات واستغلال المشهد المتوسع للخدمات المصرفية عبر الإنترنت وخدمات التكنولوجيا المالية.
يتم استهداف الصناعات بناءً على قيمة البيانات والإلحاح التشغيلي وسهولة استغلال نقاط الضعف.
تظل الرعاية الصحية هدفًا رئيسيًا بسبب بيانات المرضى الحساسة والإلحاح التشغيلي. يستغل المهاجمون الأنظمة الطبية القديمة والشبكات المجزأة.
التهديدات:
نهج التخفيف:
يمكن لأنظمة الرعاية الصحية تقليل المخاطر عن طريق تقسيم الشبكات وتأمين الأنظمة القديمة. يعمل التصحيح المنتظم والمصادقة متعددة العوامل على تعزيز المرونة الشاملة.
يواجه المصنعون هجمات متزايدة لأن توقف الإنتاج يخلق نفوذًا كبيرًا. يكشف تقارب OT/IT الخاص بهم عن العديد من نقاط الوصول الضعيفة.
التهديدات:
نهج التخفيف:
يستفيد المصنعون من عزل التكنولوجيا التشغيلية وتأمين وصول البائعين. كما أن المراقبة المستمرة للأنظمة الصناعية تقلل من نقاط الضعف الخفية.
تتعامل المؤسسات المالية مع الأموال وبيانات الهوية، مما يجعلها أهدافًا مربحة. يسعى المهاجمون إلى تحقيق مكاسب مالية مباشرة من خلال الاحتيال وعمليات الاستحواذ على الحسابات.
التهديدات:
نهج التخفيف:
تعمل الشركات المالية على تعزيز الحماية من خلال فرض المصادقة القوية والكشف عن الاحتيال في الوقت الفعلي. تساعد التحليلات السلوكية أيضًا في تحديد النشاط المشبوه بسرعة.
يواجه تجار التجزئة كميات كبيرة من الهجمات بسبب المعاملات المستمرة عبر الإنترنت. يستغل مجرمو الإنترنت أنظمة الدفع وحسابات العملاء.
التهديدات:
نهج التخفيف:
يمكن لبائعي التجزئة تعزيز الأمان من خلال إدارة الروبوتات والمصادقة القوية وبوابات الدفع الآمنة. تؤدي عمليات التدقيق المنتظمة لعمليات تكامل الجهات الخارجية أيضًا إلى تقليل التعرض.
تقوم شركات التكنولوجيا بتخزين الملكية الفكرية ودعم النظم البيئية الضخمة للمستخدمين. يهدف المهاجمون إلى التسلل إلى منصاتهم للاستغلال على نطاق أوسع.
التهديدات:
نهج التخفيف:
تعمل شركات التكنولوجيا على تحسين السلامة من خلال تشديد ضوابط API وتأمين بيئات البناء. كما تحد حوكمة الوصول وتدوير المفاتيح من الدخول غير المصرح به.
تدير الوكالات الحكومية خدمات المواطنين الأساسية وقواعد البيانات الحساسة. يستهدفهم المهاجمون لإحداث اضطراب واستخراج معلومات استراتيجية.
التهديدات:
نهج التخفيف:
تعمل ترقية البنية التحتية القديمة وفرض ضوابط صارمة على الهوية على تعزيز الحماية. تستفيد الوكالات من المراقبة المستمرة للكشف عن محاولات التسلل المبكرة.
تعمل أنظمة الطاقة على تشغيل البنية التحتية الوطنية، مما يجعلها أهدافًا عالية التأثير. يركز المهاجمون على التسبب في عدم الاستقرار التشغيلي ووقت التوقف الطويل.
التهديدات:
نهج التخفيف:
يعمل مشغلو الطاقة على تعزيز الدفاعات من خلال عزل الأنظمة الحرجة ومراقبة النشاط غير المعتاد. كما تعمل الشراكة مع خدمات استخبارات التهديدات على تحسين الاكتشاف المبكر.
تواجه المدارس والجامعات هجمات متزايدة بسبب الميزانيات المحدودة وشبكات المستخدمين الكبيرة. بالإضافة إلى ذلك، يتم استهداف المؤسسات البحثية للملكية الفكرية.
التهديدات:
نهج التخفيف:
يمكن للمؤسسات التعليمية تحسين السلامة من خلال اعتماد MFA والتدريب التوعوي. إن تعزيز ضوابط الوصول لمنصات التعلم عن بعد يقلل أيضًا من المخاطر.
يعتمد مزودو خدمات النقل على التنسيق الرقمي في الوقت الفعلي، مما يجعل الاضطرابات مكلفة. يستغل المهاجمون الاتصال البيني للنظام لتحقيق أقصى قدر من التأثير.
التهديدات:
نهج التخفيف:
تحمي المؤسسات العمليات من خلال تقسيم طبقات الشبكة ومراقبة تبعيات سلسلة التوريد. تساعد التنبيهات الآلية على اكتشاف الحالات الشاذة في أنظمة التوجيه.
تفتقر الشركات الصغيرة والمتوسطة وشركات الخدمات إلى موارد الأمن السيبراني المتقدمة، مما يجعلها أهدافًا متكررة. يستغل المهاجمون المصادقة الضعيفة والأدوات القديمة.
التهديدات:
نهج التخفيف:
تستفيد الشركات الصغيرة من اعتماد طبقات أمان منخفضة التكلفة مثل MFA وحماية نقطة النهاية. تعمل عمليات النسخ الاحتياطي المنتظمة وتدريب الموظفين على تقليل تأثير الاختراق.
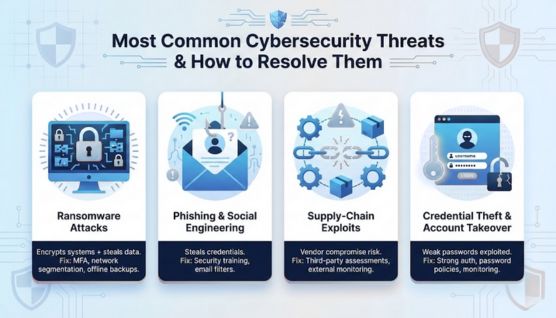
تقوم برامج الفدية بتشفير الأنظمة وسرقة البيانات للضغط على الضحايا للدفع. يمكن للمؤسسات تقليل المخاطر من خلال فرض MFA وتقسيم الشبكات والحفاظ على النسخ الاحتياطية دون اتصال بالإنترنت.
يظل التصيد الاحتيالي أسهل طريقة للمهاجمين لسرقة بيانات الاعتماد. تعمل برامج التدريب وفلاتر أمان البريد الإلكتروني على خفض معدلات النجاح بشكل ملحوظ.
يعرض المهاجمون البائعين للخطر للوصول إلى أهداف أكبر. تقلل التقييمات المنتظمة من طرف ثالث والمراقبة المستمرة لسطح الهجوم الخارجي من هذا التعرض.
كلمات المرور الضعيفة أو المعاد استخدامها تجعل الاختراقات أسهل. تساعد المصادقة القوية وسياسات كلمة المرور وأدوات المراقبة على منع الوصول غير المصرح به.
يجب على المنظمات الحديثة تعزيز وضع الأمن السيبراني من خلال استراتيجيات الدفاع الاستباقية متعددة الطبقات.
شهدت الرعاية الصحية أكبر عدد من الاختراقات بسبب بياناتها القيمة وبنيتها التحتية القديمة. استغل المهاجمون نقاط الضعف هذه للحصول على برامج الفدية والابتزاز.
لا يمكن لعمليات التصنيع تحمل وقت التوقف عن العمل، مما يمنح المهاجمين نفوذًا. من الصعب أيضًا تأمين أنظمة OT، مما يؤدي إلى إنشاء نقاط دخول سهلة.
يقومون بتخزين الأموال وبيانات الهوية ومعلومات الدفع. وهذا يجعلها بيئات ذات مكافآت عالية لسرقة بيانات الاعتماد والاحتيال.
نعم، يتم استهداف الشركات الصغيرة والمتوسطة بشكل متكرر لأنها تفتقر إلى فرق أمنية مخصصة. تزيد أوقات الاستجابة البطيئة من نجاح المهاجم.
لا يزال الخطأ البشري سببًا رئيسيًا للانتهاكات. برامج التدريب والتوعية تقلل بشكل كبير من هذه المخاطر.
يوفر CloudSek معلومات مستمرة عن التهديدات تعتمد على الذكاء الاصطناعي من خلال مراقبة البصمة الرقمية الخارجية للمؤسسة عبر مصادر الويب السطحية والعميقة والمظلمة. يساعد هذا الاكتشاف في الوقت الفعلي في تحديد تسربات البيانات وبيانات الاعتماد المكشوفة وانتحال هوية العلامة التجارية والتهديدات المستهدفة في وقت سابق.
تقوم منصة مراقبة سطح الهجوم الخارجي (EASM) الخاصة بها تلقائيًا بتعيين الأصول التي تواجه الإنترنت مثل المجالات وواجهات برمجة التطبيقات ومثيلات السحابة وتكنولوجيا المعلومات المظللة. يقوم CloudSek بعد ذلك بوضع علامة على التكوينات الخاطئة أو الثغرات الأمنية قبل أن يتمكن المهاجمون من استغلالها للوصول الأولي.
عند اكتشاف المخاطر، تقدم CloudSek تنبيهات سياقية مع إجراءات معالجة واضحة استنادًا إلى الخطورة وقابلية الاستغلال. هذا يقلل من وقت التحقيق ويعزز الاستجابة للحوادث من خلال تمكين اتخاذ قرارات أسرع وأكثر دقة.
