🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Qilin Ransomware, also known as Agenda, is a ransomware-as-a-service (RaaS) operation that first emerged in July 2022. It functions as an organized threat group rather than a single malware variant, enabling repeatable and scalable attacks.
Qilin is widely assessed as a sophisticated ransomware operation based on its consistent tooling, structured campaigns, and sustained activity over time. Its use of a service-based model allows multiple operators to conduct attacks under a shared framework.
By late 2024 and continuing into 2025, Qilin became one of the most active ransomware operations globally, accounting for a notable share of reported incidents. This growth reflects operational maturity and expansion rather than short-term or opportunistic activity.
The attack agenda behind Qilin Ransomware is focused on making money by causing disruption and threatening to expose stolen data. A U.S. Department of Health and Human Services (HHS) threat profile describes Qilin as a ransomware-as-a-service operation that works with affiliates and takes 15–20% of each ransom payment, showing a clearly profit-driven model.
After first appearing as Agenda in 2022 and later rebranding to Qilin, the group steadily increased both the number of attacks and the size of ransom demands. According to HHS reporting, ransom demands in 2023 often ranged from the tens to hundreds of thousands of dollars, and by mid-2024, more than 100 victims had been listed on its leak site, mainly in manufacturing and professional services.
Qilin strengthens its leverage through double extortion, threatening to publish stolen data even if systems are restored. This approach helps the group maximize pressure on victims, attract affiliates, and continue expanding its role within the ransomware-as-a-service ecosystem.
Qilin Ransomware executes attacks through a structured approach that turns initial access into widespread disruption and extortion pressure. The process is designed to steadily increase control over the environment before any visible damage occurs.
Once access is established, attackers focus on expanding their reach and preparing systems for coordinated impact. This preparation ensures that disruption can occur quickly and across multiple systems at the same time.
The attack becomes visible when systems are encrypted and operations are interrupted, creating urgency for the victim. At the same time, extortion pressure is applied to ensure demands remain effective even if technical recovery is possible.
Qilin Ransomware relies on a consistent set of technical methods that allow its affiliates to break into networks, maintain control, steal data, and enforce extortion. These techniques support its ransomware-as-a-service model, making attacks repeatable across different environments rather than one-off events.
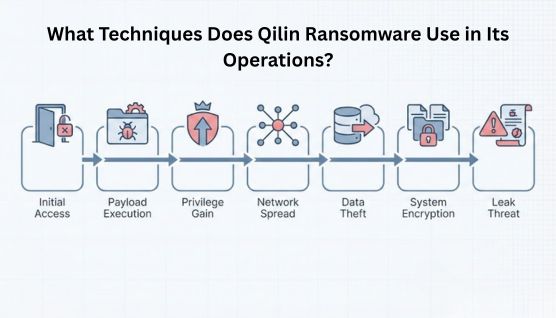
To gain entry, Qilin affiliates typically take advantage of weak or exposed access points that already exist in an organization’s environment. Qilin affiliates exploit existing weaknesses such as exposed credentials or misconfigured access to gain silent entry into networks.
Because this stage focuses on blending in, it often goes unnoticed until later phases of the attack. Early access gives attackers time to understand the network and plan their next steps.
Once inside, Qilin uses specific delivery methods to introduce and execute the ransomware payload. These infection vectors give attackers control over when and where the malware runs.
Most activity targets Windows systems, which remain common across enterprise environments. In some cases, Linux-based variants aimed at VMware ESXi servers have also been observed, expanding the potential scope of impact.
After establishing a foothold, attackers work to increase their level of access within the environment. By gaining higher privileges, they can interact with systems and controls that are normally restricted.
This elevated access makes it easier to weaken defenses and prepare the environment for broader disruption. Without it, attackers would be limited to a small portion of the network.
Qilin operations often involve moving from one system to another once access is secured. This lateral movement allows attackers to reach critical servers and shared resources.
As attackers spread across the network, the number of affected systems grows. This expansion makes recovery more difficult and increases the overall impact of the attack.
Encryption is the most visible part of a Qilin ransomware attack. Files and systems are locked to interrupt daily operations and prevent access to important data.
The goal is not selective damage but widespread disruption. By encrypting systems at scale, attackers create urgency and force organizations to respond quickly.
Before or alongside encryption, Qilin affiliates often steal sensitive data from the environment. This may include internal documents, customer records, or regulated information.
Exfiltrated data gives attackers additional leverage during negotiations. Even if systems can be restored, the risk of public exposure remains.
Qilin reinforces ransom demands by threatening to release stolen data through a Dedicated Leak Site (DLS). This approach shifts pressure from technical recovery to reputational and regulatory consequences.
Double extortion ensures that victims remain under pressure even when backups are available. It turns data exposure into a central part of the attack strategy.
In 2025, Qilin Ransomware showed a clear increase in activity, particularly targeting public sector and critical infrastructure organizations. This shift reflects a growing focus on environments where disruption can have widespread impact.
According to the Center for Internet Security (CIS) Cyber Threat Intelligence team, Qilin accounted for about 24% of ransomware incidents affecting U.S. State, Local, Tribal, and Territorial (SLTT) organizations in the second quarter of 2025. This marked a sharp rise from roughly 9% earlier in the year, highlighting the group’s rapidly expanding presence.
Organizations most affected by Qilin Ransomware activity are those where downtime or data exposure can immediately disrupt essential operations. These environments often depend on continuous service availability or handle sensitive information that cannot be easily taken offline.
Public sector entities, particularly state, local, tribal, and territorial organizations, are frequently impacted due to limited tolerance for prolonged outages. Critical infrastructure, healthcare providers, and educational institutions are also common targets, as service disruption can quickly escalate into public safety or regulatory concerns.
Manufacturing and professional services organizations are often affected as well, especially those operating complex or time-sensitive systems. In these sectors, production delays, intellectual property exposure, and contractual obligations significantly increase pressure to resolve incidents quickly.
Attacks linked to Qilin Ransomware create immediate disruption while also causing long-term business, legal, and security consequences for affected organizations.
Reducing the risk of Qilin ransomware requires early visibility into suspicious activity, controlled access across systems, and preparedness measures that limit damage before disruption occurs.
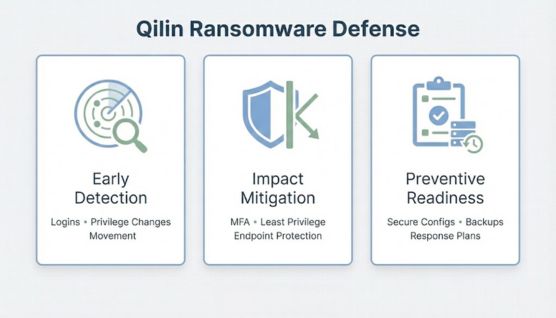
Early detection focuses on spotting abnormal behavior such as unusual logins, unexpected privilege changes, or unexplained internal movement. Training users on identifying phishing emails and monitoring authentication activity can help surface threats before attackers gain deeper access.
Mitigation efforts aim to restrict attacker movement once access is established. Enforcing Multi-Factor Authentication (MFA), limiting administrative privileges, and deploying an anti-ransomware security tool help reduce the likelihood that an attack can spread or escalate.
Prevention depends on strengthening systems and planning for recovery before an incident occurs. Maintaining secure configurations, testing backups stored on off-site infrastructure, and rehearsing incident response plans improve resilience against ransomware-related disruption.
Effective ransomware protection lowers the risk of successful attacks by limiting exposure, reducing attacker leverage, and strengthening recovery capabilities across the environment.
Ransomware protection starts by minimizing exposed services and unnecessary access points that attackers rely on for entry. Fewer exposed pathways reduce the chances of attackers establishing an initial foothold.
Modern ransomware protection focuses on detecting suspicious behavior rather than relying only on known signatures. This helps identify malicious activity early, even when attackers use new or modified techniques.
Strong protection includes reliable backup and recovery capabilities that allow organizations to restore systems without engaging attackers. This reduces the effectiveness of encryption-based pressure and shortens downtime after an incident.
By protecting sensitive data and restricting access to critical systems, ransomware protection reduces the impact of extortion threats. When attackers lose leverage, ransom demands become less effective.
Instead of relying on a single anti-ransomware tool, CloudSEK focuses on preventing ransomware attacks before they fully develop. Its approach centers on identifying early warning signs, known as initial attack vectors, from external sources.
The platform continuously monitors the open, deep, and dark web to track emerging ransomware activity, threat actor behavior, and leaked data. It also helps organizations understand weaknesses in their external infrastructure and third-party dependencies that attackers commonly exploit to gain access.
By combining threat intelligence, attack surface monitoring, and actionable alerts, CloudSEK helps security teams respond before attacks escalate into encryption or extortion. This proactive model allows organizations to prioritize real risks and strengthen defenses instead of reacting after damage has already occurred.
