🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
The 12 most dangerous malware threats in 2026 are LockBit, BlackCat (ALPHV), Cl0p, QakBot, Emotet, RedLine, Agent Tesla, Mirai, Raspberry Robin, PlugX, Formbook, AsyncRAT, Dridex, Lumma, and Bumblebee. These malware families are responsible for most ransomware incidents, large data theft cases, and long-term intrusions reported across organizations this year.
Attackers continue to rely on simple access paths rather than complex techniques. Email compromise, stolen credentials, exposed services, and built-in system tools are enough to turn a single mistake into a full-scale incident.
This review focuses on threats that consistently appear in active campaigns and play a direct role in modern attack chains seen throughout 2026. Platforms like CloudSEK help organizations track these threats early by identifying exposed assets, attacker behavior, and emerging risks before they escalate into full incidents.
In 2026, the most dangerous malware is the kind that quickly takes control and is hard to push out. Attacks that lock systems, leak sensitive data, or stay hidden for weeks tend to cause problems that don’t end with a simple cleanup.
Part of the risk comes from how normal these attacks look at the start. Routine emails, reused passwords, and familiar system tools are often enough to let malware slip in without raising suspicion.
The situation gets worse once that first access isn’t caught in time. From there, attackers can move through networks, deploy ransomware, or extract data at scale, turning a small lapse into a long and expensive recovery.
Malware threats are evolving in ways that make attacks easier to launch and harder to notice until the impact is already serious.
Modern malware no longer needs obvious vulnerabilities to get inside a system. Phishing emails, reused passwords, and overlooked services often provide a quiet entry point that looks harmless at first.
Instead of bringing in clearly malicious tools, attackers increasingly rely on software and features that are already trusted. By blending in with normal administrative activity, malware can operate for long periods without drawing attention.
Many malware strains are no longer delivered as a single, fixed payload. Attackers add or change components as the attack progresses, allowing them to adapt without starting from scratch.
Once access is established, things tend to move quickly. A single compromised account or device can lead to lateral movement, data theft, or ransomware deployment before anyone realizes what’s happening.
We reviewed these malware threats by examining how frequently they appear in real-world incidents and how consistently they are linked to serious outcomes. The focus stayed on threats that security teams are actually dealing with, not those that only appear in isolated reports.
Each threat was assessed based on how it enters systems, what it is typically used for, and how far the damage usually spreads. We also looked at whether the malware often acts as a starting point for larger attacks, such as ransomware deployment or widespread data theft.
The final selection reflects current activity and relevance rather than past reputation alone. Every threat on this list continues to surface in active campaigns and remains a practical concern for organizations in 2026.
LockBit operates as a high-velocity ransomware service optimized for repeatable intrusions, rapid encryption, and aggressive leak-site extortion. Initial access commonly begins with stolen VPN or RDP credentials or exploitation of edge devices, followed by lateral movement to achieve domain-level control and data exfiltration.
Recent campaigns emphasize automation, selective encryption, and accelerated exfiltration to reduce containment windows. Victims often experience simultaneous operational outages, regulatory exposure, and secondary fraud driven by harvested credentials.
Switzerland's National Cyber Security Centre recorded 57 ransomware reports in H1 2025, indicating sustained pressure on organizations across Zürich and Bern. This incident volume aligns closely with extortion tactics characteristic of LockBit-style operations observed across Europe.
BlackCat is a multi-platform ransomware operation engineered to function across Windows, Linux, and virtualized enterprise environments. Initial access typically relies on credential theft, abuse of remote access services, or exploitation of exposed infrastructure, followed by persistent access that enables coordinated encryption and data theft.
Affiliate discipline is a defining risk factor, with structured stages covering privilege escalation, reconnaissance, exfiltration, and disruption. Recovery complexity increases significantly when VMware stacks and Linux-backed services are affected.
The Australian Cyber Security Centre reported 138 ransomware incidents in FY2024–25, underscoring continued ransomware pressure on organizations in Sydney and Melbourne. This environment sustains the strategic danger posed by ALPHV-style campaigns against high-availability systems.
Cl0p focuses on large-scale data extortion, often prioritizing bulk theft over full encryption to maximize leverage while allowing partial business continuity. Campaigns frequently exploit third-party exposure and file-transfer ecosystems, transforming a single vulnerability into widespread downstream compromise.
Risk concentrates in legal, contractual, and reputational fallout, as stolen data triggers multi-jurisdictional reporting and prolonged litigation. Remediation is often fragmented across vendors, subsidiaries, and partners rather than confined to a single network.
The UK Cyber Security Breaches Survey 2025 estimates that 612,000 businesses experienced a cyber breach or attack in the prior year, with ransomware reported by 3 percent of organizations. This reflects sustained operational risk across hubs such as London and Manchester, where large-scale extortion groups thrive amid expanded supplier access.
QakBot functions as an access-enabling trojan designed to establish footholds, harvest credentials, and enable remote control that supports later payload deployment. Phishing remains a primary delivery vector, with follow-on activity focused on internal discovery and handoff to secondary tooling.
Its modular design increases long-term risk, allowing operators to swap in lateral movement frameworks, ransomware loaders, or data theft modules without altering initial infection patterns. Enterprise impact is often driven by rapid escalation following the compromise of a single mailbox or endpoint.
JPCERT/CC reported 10,102 incident reports in Q1 2025, reflecting sustained security pressure across Tokyo and Osaka. High incident volume creates consistent opportunity for loader-style malware like QakBot to blend into routine email compromise activity.
Emotet operates as a delivery platform that relies on email thread hijacking and staged payload deployment to maintain flexible access. Operators prioritize persistence and propagation, expanding reach across inboxes, shared drives, and trusted endpoint relationships.
Risk escalates through payload chaining, where an Emotet foothold enables infostealers, command and control frameworks, or ransomware operators. Cleanup costs rise due to reinfection cycles tied to compromised email accounts and address books.
CERT.LV recorded 631 cyber incidents in Q1 2025 and blocked 476,855 visits via DNS Firewall, highlighting sustained threat pressure around Riga. This volume supports Emotet-style distribution models dependent on repeated user exposure.
RedLine specializes in credential theft, browser session extraction, and cryptocurrency wallet targeting, feeding downstream account takeover and fraud operations. Distribution commonly uses cracked software, fake installers, and malicious download lures that convert user intent into compromise.
Damage often emerges later through reused credentials, stolen cookies, and hijacked MFA recovery paths across SaaS and banking platforms. Effective response requires endpoint remediation combined with broad credential rotation across personal and enterprise identity systems.
Canada’s Maple Disruption 2025 reporting identified 1,622 fraud reports linked to the operation, including 1,433 phishing and smishing cases, illustrating the fraud ecosystem affecting Toronto and Ottawa. Credential-stealing malware directly benefits from this sustained phishing volume.
Agent Tesla is a long-running credential-stealing RAT focused on keylogging, clipboard capture, screen scraping, and data exfiltration over common protocols. Campaigns frequently target small and mid-sized organizations using email lures themed around invoices and purchase orders aimed at finance and operations staff.
Low-friction deployment and familiar delivery techniques maintain steady infection rates, particularly where email security and endpoint controls lag. Business impact centers on mailbox compromise, financial fraud enablement, and credential reuse across SaaS administration portals.
The Singapore Police Force reported 19,665 scam cases in H1 2025 with losses totaling approximately 456.4 million US dollars. This high-pressure social engineering environment across Singapore supports credential-stealing tools like Agent Tesla.
Mirai compromises exposed IoT devices by exploiting weak passwords, default credentials, and internet-facing management interfaces. Operators monetize scale through DDoS-for-hire services, outage coercion, and infrastructure disruption that extends beyond individual targets.
Risk is amplified by persistence, as infected devices frequently rejoin botnets after reboot and remain unmanaged for extended periods. Defense becomes an ecosystem challenge involving ISPs, manufacturers, and enterprise networks.
Dutch reporting on DigiD documented four DDoS attacks between January and March 2025, highlighting continued disruption pressure across national infrastructure managed from The Hague. This reinforces the strategic threat posed by Mirai-style botnets.
Raspberry Robin functions as a propagation-focused entry mechanism, often leveraging removable media and staged delivery to enable follow-on access. Its value lies in foothold brokerage, where initial compromise is transferred into ransomware or data theft operations.
Containment is challenging in large environments with mixed device fleets, shared media workflows, and inconsistent endpoint enforcement. Risk increases in settings involving contractors, shared workstations, and distributed branch offices.
KE-CIRT/CC reported more than 2.5 billion detected cyber threat events and issued 13.2 million advisories in Q1 2025, reflecting intense exposure across Nairobi and national networks.
PlugX is a stealth-oriented backdoor associated with long-dwell espionage operations, emphasizing persistence and staged command execution. Campaigns often use DLL sideloading, signed binary abuse, and low-profile command and control traffic to evade detection.
Strategic impact accrues over time as operators map networks, collect sensitive data, and retain access through refresh cycles. Defense teams face complex decisions around hunting scope, rebuilding trust, and system integrity.
The Italian National Cybersecurity Agency reported 1,549 cyber events in H1 2025, including 346 confirmed incidents affecting areas such as Rome and Milan. High incident throughput increases the likelihood of stealth backdoors persisting undetected.
Formbook targets credentials, browser data, and form submissions, packaging stolen information for large-scale criminal resale. Delivery relies heavily on email attachments, fake invoices, and commodity droppers aimed at end users.
Its effectiveness derives from volume, as each compromised login can enable mailbox takeover, payroll fraud, and third-party account abuse. Remediation requires broad identity containment across browsers, email platforms, and enterprise SSO environments.
The New Zealand National Cyber Security Centre reported 1,369 incidents in Q1 2025, including 440 phishing and credential harvesting cases, a 15 percent increase from the previous quarter. Activity concentrated in Auckland and Wellington reflects sustained credential theft aligned with large-scale secondary exploitation.
AsyncRAT provides full remote access capabilities, enabling file theft, surveillance, credential harvesting, and payload delivery from a single foothold. Distribution typically uses email lures and fake installers, followed by expansion through password recovery and privilege escalation.
Risk is elevated in environments with mixed personal and business device usage, where weak segmentation allows a single endpoint to pivot into shared drives and administrative consoles. Persistence supports long-running campaigns that erode endpoint trust.
UAE state media reporting on the National Cybersecurity Report 2025 cited 58 percent growth in ransomware group activity, indicating intensifying threat conditions across Dubai and Abu Dhabi. This environment increases the operational value of remote access tools like AsyncRAT.
Reducing malware risk in 2026 comes down to limiting the small weaknesses attackers repeatedly exploit. Most successful attacks still begin with simple access points that quietly go unnoticed.
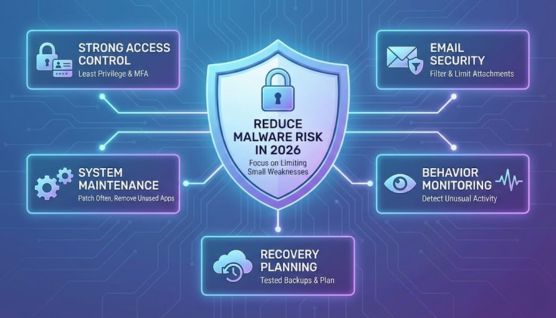
Strong access control slows malware down immediately. When users only have the permissions they actually need and logins are protected with multi-factor authentication, a single compromised account is far less likely to spread damage.
Email continues to be the most common entry point for malware. Filtering malicious messages and limiting what links and attachments can execute removes many threats before they ever reach a system.
Outdated software and unused services create easy opportunities for attackers. Keeping systems patched and removing unnecessary components reduces the overall attack surface.
Modern malware often avoids detection by blending in with normal activity. Watching for unusual behavior instead of relying only on known signatures helps identify threats earlier.
No defense is perfect, and some attacks will still succeed. Tested backups and a clear response plan help organizations recover quickly and avoid long-term disruption.
CloudSEK helps organizations stay ahead of malware threats by identifying risks before they turn into active incidents. Its approach focuses on tracking attacker behavior, exposed assets, and early signs of compromise rather than reacting after damage is done.
By combining threat intelligence with continuous monitoring, CloudSEK gives security teams clearer visibility into where malware campaigns are forming and how they might enter an environment. This makes it easier to prioritize real risks, close gaps early, and respond faster when threats start to move.
