🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
الوجبات السريعة الرئيسية:
تقييم مخاطر البيانات هو عملية منظمة لتحديد المعلومات الحساسة وتقييم التهديدات وحساب المخاطر بناءً على الاحتمالية وتأثير الأعمال. وهو يشرح أين توجد البيانات، وكيف تتحرك، ومن يمكنه الوصول إليها، وما هي حالات التعرض الموجودة عبر البيئات متعددة السحابات وSaaS ونقطة النهاية والبيئات المحلية.
تقوم التقييمات بتقييم فعالية الضوابط الحالية بما في ذلك التشفير وسياسات الوصول إلى الهوية والتجزئة وممارسات الاحتفاظ وأنظمة المراقبة. كما أنها تسلط الضوء على نقاط الضعف مثل المستودعات غير المحمية أو قوائم جرد البيانات غير المكتملة أو الحوكمة غير المتسقة.
تستخدم المؤسسات تقييمات مخاطر البيانات لتقليل التعرض وتلبية التوقعات التنظيمية وتعزيز استراتيجيات حماية البيانات على المدى الطويل. تدعم هذه المؤسسة عمليات أكثر مرونة واتخاذ قرارات أفضل حول معالجة البيانات.
يعمل تقييم مخاطر البيانات من خلال تحديد البيانات الحساسة وتقييم نقاط الضعف وتصنيف المخاطر بناءً على التأثير والاحتمالية حتى تتمكن الفرق من تحديد أولويات العلاج بكفاءة.
تقوم أدوات Discovery بفحص المواقع المهيكلة وغير المهيكلة لتحديد المعلومات الحساسة. يقوم التصنيف بتعيين ملصقات مثل PII أو PHI أو PCI أو البيانات الخاصة أو المنظمة لتحديد الحماية المطلوبة.
يعمل تحديد المخاطر على تقييم التكوينات الخاطئة وفجوات الأذونات وتدفقات البيانات غير الآمنة ومتجهات التهديد. كما يأخذ في الاعتبار المهاجمين المحتملين والتقنيات التي يمكنهم استخدامها لاستغلال نقاط الضعف.
يؤدي تسجيل المخاطر إلى مضاعفة الاحتمالية والتأثير لإنتاج تقييمات متسقة. تساعد الحدود الواضحة الفرق على تصنيف التعرضات على أنها منخفضة أو متوسطة أو عالية الخطورة.
تقارن خرائط التحكم الحماية ضد الأطر مثل NIST CSF و ISO 27001 ومتطلبات GDPR. تكشف هذه العملية عن عناصر التحكم المفقودة مثل التشفير أو الترميز أو المصادقة متعددة العوامل.
يقوم تخطيط المعالجة بتعيين الإجراءات والمالكين والجداول الزمنية لتقليل المخاطر ذات الأولوية العالية. تركز الخطط عادةً على تشديد الأذونات أو تحسين التشفير أو تأمين تدفقات البيانات.
تنجم مخاطر البيانات عن اعتماد السحابة المتعددة، وتوسيع SaaS، والمحتوى الذي تم إنشاؤه بواسطة الذكاء الاصطناعي، وعمليات تكامل الطرف الثالث، والتزامات الامتثال العالمية. تعمل هذه المخاطر على توسيع أسطح الهجوم وتقليل الرؤية عبر البيئات اللامركزية.
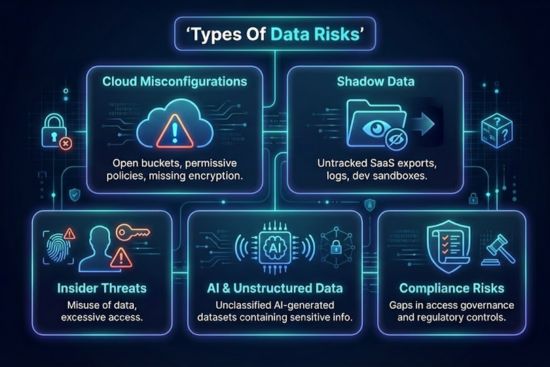
تؤدي المجموعات التي تم تكوينها بشكل خاطئ وقواعد البيانات المفتوحة والسياسات التي تسمح بالوصول العام إلى التعرض المباشر. يؤدي التشفير المفقود أو إعدادات الشبكات المتساهلة إلى زيادة احتمالية الاختراق.
نماذج بيانات الظل في عمليات تصدير SaaS التي لم يتم تعقبها والسجلات غير المُدارة والمستودعات المؤقتة وصناديق حماية المطورين. غالبًا ما تفلت هذه الأصول من الحوكمة وتحتوي على معلومات حساسة.
قد يقوم الموظفون أو المقاولون بإساءة استخدام البيانات عن قصد أو عن طريق الخطأ. يؤدي الوصول الواسع للغاية أو مراقبة النشاط غير الكافية إلى زيادة المخاطر الداخلية.
تقوم أنظمة الذكاء الاصطناعي بإنشاء مجموعات بيانات جديدة غير منظمة قد تتضمن معلومات تحديد الهوية الشخصية أو المحتوى المنظم. وبدون التصنيف، يصبح من الصعب تتبع مجموعات البيانات هذه وتأمينها.
تتطلب الأطر التنظيمية ضوابط صارمة على المعلومات الشخصية والمالية. يمكن أن تؤدي الثغرات في جداول الاحتفاظ أو الاستعداد للإخراق أو حوكمة الوصول إلى انتهاكات GDPR و HIPAA و PCI DSS و SOC 2.
يركز تقييم مخاطر البيانات السحابية على تكوين التخزين وإدارة الهوية وحركة البيانات والأدوات التي تم إنشاؤها بواسطة SaaS عبر البيئات متعددة السحابات.
تحدد أدوات المسح المعلومات الحساسة في الحاويات والنقاط وقواعد البيانات المُدارة والتخزين بدون خادم. بمجرد اكتشافه، يحدد التصنيف مستوى الحماية المطلوب.
تتضمن عمليات التهيئة الخاطئة الشائعة التخزين المفتوح وفرض TLS المفقود وقواعد جدار الحماية الضعيفة والوصول غير المقيد عبر الحسابات. تظل هذه الفجوات من أهم أسباب الاختراقات السحابية.
تحدد مراجعات Access الامتيازات المفرطة والحسابات الخاملة والأدوار عالية المخاطر. يؤدي فرض أقل الامتيازات و MFA إلى تقليل فرص الهجوم الداخلي والخارجي.
يكشف تخطيط تدفق البيانات عن كيفية انتقال المعلومات بين التطبيقات والخدمات ومناطق السحابة. يساعد التخطيط على إبراز مسارات النقل غير الآمنة أو التعرض أثناء الترحيل.
تقوم منصات SaaS بإنشاء التقارير والصادرات والسجلات التي قد تحتوي على بيانات حساسة. تضمن المراقبة تأمين هذه الملفات أو تخزينها بشكل صحيح أو حذفها وفقًا لسياسات الاحتفاظ.
تعمل DSPM (إدارة وضع أمان البيانات) على تحسين تقييم مخاطر البيانات من خلال الاكتشاف المستمر للبيانات الحساسة وتحليل الوصول وتحديد التكوينات الخاطئة عبر بيئات السحابة وبيئات SaaS. إنه يعالج فجوات الرؤية التي غالبًا ما تفوتها الأدوات التقليدية.
تحدد DSPM تلقائيًا البيانات المخزنة عبر الأنظمة الأساسية السحابية وتطبيقات SaaS والتخزين غير المُدار. يوفر مخزونًا محدثًا لمجموعات البيانات الحساسة والمنظمة.
تقوم أدوات DSPM بتصنيف البيانات الجديدة فور ظهورها في المستودعات. يضمن المسح المستمر الكشف السريع عن المعلومات الحساسة أو أحداث التعرض.
يكشف DSPM عن التخزين غير المُدار والنسخ الاحتياطية المهجورة والصادرات غير الآمنة. غالبًا ما تحتوي هذه الأصول التي تم تجاهلها على معلومات حساسة تفتقر إلى الحوكمة المناسبة.
يقوم DSPM بتقييم المخاطر باستخدام الحساسية ومستوى الوصول وحالة التكوين وسياق التعرض. ينتج عن ذلك مستويات مخاطر دقيقة وذات أولوية للمعالجة.
يتكامل DSPM مع أنظمة IAM و SIEM و SOAR و DLP لتبسيط اكتشاف الحوادث والاستجابة لها. تعمل عمليات الدمج هذه على تحسين الرؤية عبر الفرق وعمليات سير العمل.
يتضمن تقييم مخاطر البيانات إنشاء المخزون، ورسم خرائط التدفق، وتحليل التهديدات، وتسجيل المخاطر، والمراقبة المستمرة لتقييم التعرض بطريقة منظمة وقابلة للتكرار.
يقوم المخزون بتوثيق جميع أصول البيانات الحساسة ومواقع التخزين والتصنيفات الخاصة بها. يضع الأساس لتقييم التعرض والالتزامات التنظيمية.
يعرض تخطيط التدفق كيفية انتقال البيانات عبر المستخدمين والتطبيقات والخدمات السحابية. وهي تحدد النقاط الضعيفة حيث قد تتعرض البيانات أثناء النقل أو المعالجة.
يفحص تحليل التهديدات تقنيات المهاجم ونقاط الضعف البيئية. يساعد فهم مسارات التهديدات المحتملة على تحديد الإجراءات الوقائية ذات الصلة.
يتتبع السجل المركزي المخاطر وتقييمات الخطورة وأصحاب المعالجة والمواعيد النهائية. وهو يدعم الحوكمة والاستعداد للتدقيق وإعداد التقارير المستمرة.
تكتشف المراقبة التغييرات في الوصول أو التكوين أو التعرض عبر البيئات. تضمن التقارير للفرق والمدققين رؤية لمستويات المخاطر والتحسينات.
تساعد الأطر المؤسسات على تنظيم عمليات التقييم الخاصة بها وتحديد الضوابط المطلوبة.
يحدد NIST CSF وظائف تحديد التهديدات وحمايتها واكتشافها والاستجابة لها والتعافي منها. يوفر هيكلًا مرنًا لإدارة المخاطر الإلكترونية.
تحدد ISO 27001 متطلبات أنظمة إدارة أمن المعلومات. يتضمن الملحق A عناصر تحكم لإدارة الوصول والتشفير وأمن الشبكة ومعالجة البيانات.
تتطلب اللائحة العامة لحماية البيانات تقييمات تأثير حماية البيانات للمعالجة عالية المخاطر. تقوم DPIAs بتقييم مخاطر الخصوصية وممارسات تقليل البيانات ومتطلبات المعالجة القانونية.
تحدد SOC 2 معايير الأمان والتوافر والسرية وسلامة المعالجة والخصوصية. يتم استخدامه على نطاق واسع من قبل شركات SaaS ومقدمي الخدمات.
يحدد PCI DSS متطلبات حماية بيانات بطاقة الدفع. تتضمن عناصر التحكم التشفير والترميز والتجزئة وإدارة الوصول الصارمة.
يضمن التسلسل المنظم المكون من خمس خطوات تقييمًا متسقًا عبر السحابة وSaaS والأنظمة الداخلية.
تحدد الفرق مجموعات البيانات التي تحتوي على معلومات شخصية أو مالية أو منظمة أو خاصة. يحدد التصنيف الضوابط ذات الصلة ومتطلبات السياسة.
يكشف تعيين مواقع التخزين عن الأصول غير المعروفة أو مستودعات الظل أو النسخ المكررة. يضمن القضاء على النقاط العمياء التقييم الدقيق.
تحدد نمذجة التهديدات كيف يمكن للمهاجمين استغلال نقاط الضعف في التكوين أو الهوية أو تدفقات البيانات. يكشف تحليل التعرض عن الأصول الأكثر عرضة للخطر.
يتم تعيين درجات المخاطر باستخدام التأثير والاحتمالية لإنشاء تقييمات خطورة متسقة. تحظى العناصر عالية الخطورة بالأولوية للمعالجة.
يتم تعيين الملكية والجداول الزمنية لإجراءات المعالجة مثل تشديد الأذونات أو إضافة التشفير أو تحسين سياسات الاستبقاء. تتوافق الأولويات مع تأثير الأعمال والمتطلبات التنظيمية.
تعتمد المؤسسات على البيانات الحساسة عبر الأنظمة الأساسية السحابية وتطبيقات SaaS والأنظمة الموزعة. بدون التقييم، تزيد فجوات الرؤية والتشكيلات الخاطئة من احتمالية الاختراق والمخاطر التشغيلية.
تستمر الأطر التنظيمية في التطور، مما يتطلب حوكمة أقوى وممارسات الاحتفاظ والاستعداد للإبلاغ عن الخرق. تضمن التقييمات المنتظمة بقاء الضوابط متوافقة مع المتطلبات القانونية.
تعمل التقييمات أيضًا على تعزيز المرونة التشغيلية من خلال تحديد نقاط الضعف قبل أن يستغلها المهاجمون. يعمل هذا النهج الاستباقي على تحسين الحوكمة وتقليل المخاطر طويلة الأجل.
تعمل الأدوات على التشغيل الآلي للاكتشاف والتصنيف والمراقبة وتسجيل المخاطر لتحسين الدقة وتقليل عبء العمل اليدوي.
تقوم محركات Discovery بتحديد موقع البيانات الحساسة عبر البيئات المهيكلة وغير المهيكلة والسحابية. تحدد قواعد التصنيف متطلبات الحساسية والاحتفاظ.
يوفر DSPM رؤية مستمرة لبيئات السحابة وSaaS. يكتشف التكوينات الخاطئة والأذونات المفرطة وبيانات الظل.
تراقب DLP استخدام البيانات وتمنع المشاركة أو الإرسال غير المصرح به. تساعد السياسات في التحكم في كيفية انتقال المعلومات الحساسة عبر الأنظمة.
تقوم SIEM بتجميع السجلات لاكتشاف النشاط المشبوه. تعمل SOAR على أتمتة الاستجابات للأحداث عالية الخطورة وتسريع سير عمل التحقيق.
تقوم محركات تسجيل المخاطر بحساب الخطورة بناءً على السياق والتعرض. تساعد هذه التقييمات الفرق في تحديد أولويات المعالجة وتتبع التحسينات.
يجب على المؤسسات إجراء تقييمات مستمرة في بيئات السحابة الديناميكية حيث تتغير البيانات والتكوينات بشكل متكرر. تضمن المراقبة المستمرة معالجة التعرضات الجديدة على الفور.
قد تتطلب الصناعات الخاضعة للتنظيم تقييمات ربع سنوية أو نصف سنوية أو سنوية. يوصى بإجراء تقييمات إضافية بعد عمليات الترحيل أو ترقيات النظام أو الحوادث الأمنية للتحقق من فعالية التحكم.
تعمل الأداة المناسبة على تحسين الرؤية وتقوية الحوكمة وتسريع المعالجة.
تقوم المنصات الآلية بالبحث باستمرار عن البيانات الحساسة وتغييرات التكوين. تحافظ هذه الرؤية في الوقت الفعلي على دقة التقييمات في البيئات سريعة التطور.
تعمل لوحات المعلومات الموحدة على دمج الاكتشاف وتحليل الوصول وتخطيط التدفق وتسجيل المخاطر في عرض واحد. يساعد ذلك الفرق في تحديد أولويات العناصر عالية الخطورة وتقليل التعرض بشكل أكثر كفاءة.
والغرض من ذلك هو تحديد البيانات الحساسة وتقييم التهديدات وتقليل التعرض. هذا يدعم الامتثال ويحسن حماية البيانات.
تختلف الجداول الزمنية بناءً على تعقيد البيئة. تعمل الأدوات الآلية على تسريع التقييمات من خلال الاكتشاف المستمر.
نعم، تعد أنظمة السحابة وأنظمة SaaS ضرورية لتقييمات مخاطر البيانات الحديثة. غالبًا ما تخزن هذه المنصات أكبر حجم من البيانات الحساسة.
تركز مخاطر البيانات على التعرض للمعلومات الحساسة. تغطي مخاطر الأمن السيبراني التهديدات الأوسع عبر البنية التحتية والتطبيقات.
عادةً ما تقود فرق الأمان والحوكمة والامتثال التقييمات. قد تعتمد المؤسسات الصغيرة على فرق تكنولوجيا المعلومات التي تدعمها المنصات الآلية.
تساعد تقييمات مخاطر البيانات المؤسسات على فهم مكان وجود البيانات الحساسة، وكيفية الوصول إليها، وحالات التعرض التي تهددها. إنها تدعم الحوكمة وتقلل من نقاط الضعف وتعزز الامتثال التنظيمي عبر البيئات الموزعة.
باستخدام أدوات DSPM والاكتشاف الآلي وتسجيل المخاطر السياقية، تكتسب المؤسسات رؤية مستمرة للمخاطر المتطورة. تعمل التقييمات الفعالة على تحسين المرونة على المدى الطويل وتمكين عمليات البيانات الأكثر أمانًا وكفاءة.
