🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
HackerOne هي أفضل منصة مكافآت الأخطاء الشاملة في عام 2026 لأنها تقدم أقوى مزيج من عمق البرنامج والموثوقية والمكافآت للقراصنة الأخلاقيين. إن حجمها واتساقها يجعلانها البيئة الأكثر موثوقية لكل من الباحثين الجدد وذوي الخبرة.
تساعد منصات مكافآت الأخطاء الباحثين الأمنيين في العثور على نقاط الضعف والإبلاغ عنها في نظام بيئي منظم وآمن من الناحية القانونية. إنها تمنح المؤسسات تغطية أمنية مستمرة بينما تسمح للقراصنة الأخلاقيين بالكسب بناءً على تأثير النتائج التي توصلوا إليها.
أصبح المشهد في عام 2026 أوسع من أي وقت مضى، مع منصات متخصصة في Web3، والاختبارات المُدارة، والبرامج التي تركز على الخصوصية، والاكتشاف بمساعدة الأتمتة. يستعرض هذا الدليل أفضل عشرة منصات ويسلط الضوء على ما تقدمه كل واحدة حتى يتمكن الباحثون من التوافق مع البيئات التي تناسب أهدافهم.
تم تقييم كل منصة بناءً على كيفية أدائها للقراصنة الأخلاقيين في الاستخدام الحقيقي، بما في ذلك اتساق المدفوعات وجودة البرنامج وتجربة الباحث. كان الهدف هو فهم ما تقدمه هذه المنصات فعليًا بمجرد أن يبدأ الباحث في اختبار نقاط الضعف وإرسالها.
تم فحص العوامل الرئيسية مثل استجابة الفرز ووضوح النطاق وشفافية القاعدة والتواصل عن كثب. تكشف هذه العناصر ما إذا كانت المنصة تدعم التعاون السلس أو تخلق اختناقات أثناء عملية إعداد التقارير.
تم إيلاء اهتمام خاص لمجالات مثل عمق مكافأة Web3 ونماذج pentest المُدارة ولوائح الاتحاد الأوروبي والاكتشاف القائم على الأتمتة. وقد ساعد ذلك في تحديد نقاط القوة الفريدة لكل منصة وتصنيفها وفقًا لما من المرجح أن يكتسبه الباحثون.
تحافظ HackerOne على ريادتها من خلال تقديم مزيج لا مثيل له من البرامج النشطة والمكافآت القوية وثقة المؤسسة. إنه يوفر تجربة باحث مصقولة تبدو متسقة سواء كنت تبدأ أو تطارد نقاط ضعف عالية التأثير.
سير عمل إعداد التقارير الخاص بها سريع ومستقر ومدعوم من قبل فرق الفرز المدربة جيدًا. وهذا يجعلها واحدة من المنصات القليلة حيث يمكن للباحثين الاعتماد على حلقات التغذية الراجعة التي يمكن التنبؤ بها والنمو طويل الأجل.
النقاط البارزة الرئيسية:
تقدم Bugcrowd مجموعة واسعة من البرامج عبر الصناعات، مما يجعل من السهل العثور على النطاقات التي تتناسب مع اهتماماتك. تبدو واجهته وسير العمل بديهيًا، خاصة للباحثين الذين يحبون التنقل بين أنواع المشاركة المختلفة.
تتألق المنصة من خلال نظام الدعوة الخاص بها، والذي يكافئ الأداء تدريجيًا بفرص عالية الجودة. بالنسبة للباحثين الذين يرغبون في الوصول الثابت إلى البرنامج دون تدقيق شديد، يعد Bugcrowd خيارًا متوازنًا ويمكن الاعتماد عليه.
النقاط البارزة الرئيسية:
تبرز Intigriti من خلال تقديم واحدة من أكثر تجارب الإعداد سلاسة في مساحة مكافآت الأخطاء. تصميم المنصة يجعل تحديد النطاق والاختبار نظيفين ويمكن التحكم فيهما، خاصة للباحثين الجدد.
أوقات الاستجابة سريعة باستمرار، مما يمنح المبتدئين وضوحًا سريعًا بشأن جودة التقرير واتجاهه. تجذب قاعدة البرامج التي تركز على الاتحاد الأوروبي أيضًا أولئك الذين يبحثون عن بيئات شفافة ومنظمة جيدًا.
النقاط البارزة الرئيسية:
تتخذ Synack نهجًا منظمًا من خلال قبول الباحثين الذين تم فحصهم فقط في نظامها البيئي الخاص. هذا يخلق بيئة متميزة حيث تبدو كل مشاركة منظمة ومهنية.
تقدم البرامج عادةً دفعات أعلى لأنها تتضمن أصولًا حساسة وتوقعات على مستوى المؤسسة. بمجرد القبول، يستفيد الباحثون من العمل الذي يمكن التنبؤ به، والفرز السريع، والفرص التقنية الأعمق.
النقاط البارزة الرئيسية:
تناشد YesWeHack الباحثين الذين يقدرون معايير الخصوصية الصارمة والنطاقات المحددة جيدًا. تحظى برامجها بشعبية خاصة في الصناعات التي يكون فيها التنظيم والامتثال أمرًا مهمًا.
تتميز المنصة بسهولة التنقل وتوفر اتصالًا شفافًا في كل مرحلة. يقدّر الصيادون المقيمون في الاتحاد الأوروبي بشكل خاص تركيزهم الإقليمي وهياكل المكافآت المتوازنة.
النقاط البارزة الرئيسية:
يمزج كوبالت بين صيد الحشرات واختبار الاختراق المنظم من خلال تقديم مشاركات مخططة بدلاً من سباقات المكافآت المفتوحة. وهذا يمنح الباحثين دورات عمل متسقة وتوقعات أوضح.
يضمن نموذجها المُدار التواصل السريع والمدفوعات المستقرة المرتبطة بالتسليمات المحددة جيدًا. بالنسبة لأولئك الذين يفضلون سير العمل الذي يمكن التنبؤ به على الطلبات التنافسية، يبرز Cobalt كخيار محسّن.
النقاط البارزة الرئيسية:
تهيمن Immunefi على مساحة Web3 مع أكبر مجموعة من برامج مكافآت blockchain و DeFi. تعتبر مكافآتها من أكثر المكافآت سخاءً في عالم الأمن بسبب المخاطر المالية المرتبطة باستغلال العقود الذكية.
سيجد الباحثون ذوو الخبرة في مجال بلوكتشين نقاط الضعف عالية التأثير أكثر فائدة هنا من أي منصة Web2. تصل أخطاء DeFi الحرجة بانتظام إلى مدفوعات من ستة أو سبعة أرقام.
النقاط البارزة الرئيسية:
تقدم HackenProof مزيجًا مرنًا من برامج Web2 و Web3، مما يجعلها مثالية للباحثين الذين يستمتعون بالتبديل بين الأهداف التقليدية والأهداف على السلسلة. المنصة بسيطة وتدعم الصيادين الجدد جيدًا.
تأتي البرامج التي تركز على بلوكتشين بمكافآت تنافسية، بينما توفر نطاقات Web2 الاتساق لأولئك الذين يبنون الثقة. طبيعتها الهجينة تجعلها خيارًا متعدد الاستخدامات.
النقاط البارزة الرئيسية:
يقدم Detectify Crowdsource نموذجًا فريدًا حيث يساهم الباحثون المهرة في الماسحات الضوئية الآلية. إنه يكافئ أولئك الذين يجدون الأنماط باستمرار ويطورون حمولات عالية التأثير.
تناسب هذه المنصة الباحثين الذين يفضلون العمق على الاتساع، مع التركيز على أبحاث الاستغلال عالية الجودة بدلاً من الطلبات السريعة. يضمن مجتمعها الصغير الذي تم فحصه اعترافًا قويًا بالعمل المؤثر.
النقاط البارزة الرئيسية:
تم تصميم Open Bug Bounty للتعلم والخدمة العامة بدلاً من المكافآت المالية. يساعد الباحثون في تأمين مواقع الويب من خلال الكشف المنسق وبناء المصداقية على طول الطريق.
هذا يجعلها واحدة من أفضل نقاط البداية للمبتدئين في تعلم كتابة التقارير وتحديد نقاط الضعف. تشجع طبيعتها التي يحركها المجتمع التعاون والشفافية.
النقاط البارزة الرئيسية:
منصة مكافأة الأخطاء هي بيئة منسقة حيث تنشر المؤسسات برامج الأمان وتكافئ الباحثين لاكتشاف نقاط الضعف. تعمل هذه المنصات على ربط المتسللين الأخلاقيين بالشركات التي تسعى إلى إجراء اختبارات منظمة وآمنة من الناحية القانونية.
وهي تعمل بمثابة العمود الفقري لبرامج الكشف عن نقاط الضعف الحديثة (VDPs) من خلال تركيز الاتصالات والفرز والمدفوعات. يستخدمها المتسللون الأخلاقيون لتقديم النتائج بثقة بينما تستفيد الشركات من تدفقات عمل التقارير المنظمة.
البرامج العامة والخاصة والمدارة هي التنسيقات الأكثر شيوعًا. يوفر كل منها مستويات مختلفة من الوصول وإمكانية المكافأة والتعقيد اعتمادًا على احتياجات المؤسسة.
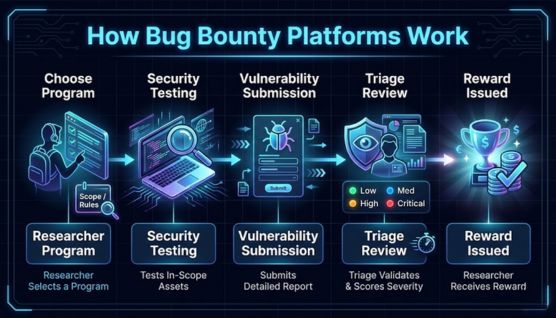
تتبع معظم المنصات سير العمل القياسي: يختار الباحثون برنامجًا ويختبرون الأصول المحددة ويرسلون نقاط الضعف وينتظرون التحقق من الفرز. بعد التحقق من الصحة، يتم إصدار المكافآت استنادًا إلى درجة الخطورة وقيمة الأصول وسياسات المورد.
تقوم المنصات بتعيين فرق فرز مخصصة أو آلية لمراجعة الطلبات بسرعة. وهذا يضمن التواصل المتسق، وتسجيل درجات الخطورة بدقة، وتقليل الإيجابيات الكاذبة.
تنتقل العملية عمومًا من التقديم إلى التحقق في غضون أيام أو أسابيع اعتمادًا على نضج البرنامج. عادةً ما تشير أوقات الفرز الأسرع إلى جودة منصة أقوى ورضا أعلى للباحث.
تلعب منصات Bug bounty دورًا مهمًا في تعزيز الأمن لكل من المنظمات والمتسللين الأخلاقيين.
اتساق المدفوعات مهم لأنه يؤثر بشكل مباشر على التحفيز طويل الأجل واستثمار الوقت. عادةً ما تقدم المنصات ذات التعرض العالي للمؤسسات أو Web3 مكافآت أقوى للأخطاء المؤثرة.
تساعد البرامج العامة المبتدئين على بناء الثقة، بينما توفر البرامج الخاصة والمدارة فرصًا ثابتة للباحثين ذوي الخبرة. إن فهم كيفية قيام كل منصة ببناء الوصول يجعل من السهل العثور على البرامج التي تتوافق مع مستوى التوفر والمهارة.
تختلف المنصات في مدى صعوبة برامجها، لذا فإن اختيار منصة تتوافق مع تجربتك الحالية يمنع الإحباط. مع تطور المهارات، يصبح الانتقال إلى البرامج الخاصة أو المتخصصة أكثر واقعية ومكافأة.
تدعم المنصات المختلفة أنواعًا مختلفة من الأصول، من تطبيقات الويب التقليدية إلى واجهات برمجة التطبيقات وتطبيقات الأجهزة المحمولة والسحابة والعقود الذكية. تضمن مطابقة نقاط القوة التقنية الخاصة بك مع النطاق الصحيح تقدمًا أسرع ونتائج عالية الجودة.
غالبًا ما يعني المجتمع الأكبر منافسة أقوى، ولكنه يشير أيضًا إلى نظام بيئي أكثر نشاطًا وجدارة بالثقة. من ناحية أخرى، يمكن للمجتمعات الصغيرة المنسقة أن تقدم اعترافًا أعمق ومشاركة أكثر استقرارًا.
يساعد الفرز السريع الباحثين على فهم ما إذا كانت تقاريرهم صحيحة وكيفية تقييمها. يقلل التواصل المتسق أيضًا من عدم اليقين ويسرع المدفوعات.
تركز بعض المنصات بشكل كبير على قطاعات مثل Web3 أو SaaS للمؤسسات أو الأنظمة الحكومية. يتيح لك استهداف منصة تتوافق مع اهتماماتك طويلة المدى بناء خبرة قيمة في مجالات أمان محددة.
تعتمد المدفوعات عمومًا على قيمة الأصول وتأثير الاستغلال وحساسية الصناعة. تقدم المنصات ذات البرامج الممولة بشكل كبير بطبيعة الحال نطاقات جوائز أكبر.
تتصدر Synack و Immunefi باستمرار بسبب مؤسستهما وتعرضهما لـ Web3. غالبًا ما تتلقى نقاط الضعف الحرجة في العقود الذكية دفعات عالية بشكل استثنائي.
يمكن للباحثين تحقيق أقصى قدر من الأرباح من خلال التخصص في أمان API أو العقود الذكية أو التكوينات الخاطئة للسحابة. يؤدي إنشاء سجل تقارير قوي أيضًا إلى زيادة الدعوات الخاصة والوصول إلى البرامج ذات الأجور الأعلى.
تقوم مكافآت Web3 بتقييم المخاطر على السلسلة ومنطق العقد الذكي وآليات التشفير، مما يجعلها مختلفة جوهريًا عن أمان الويب التقليدي. يمكن أن تؤثر نقاط الضعف هذه بشكل مباشر على الأصول الرقمية.
تخلق المخاطر المالية في DeFi مجموعات مكافآت أكبر بكثير، وتجذب باحثين متخصصين للغاية. تهيمن Immunefi و HackenProof على هذا القطاع بمعايير إعداد تقارير شاملة تركز على بلوكتشين.
يجب على الباحثين فهم تحسين الغاز وسيناريوهات القروض السريعة وتفاعلات العقد لتحقيق النجاح. أنماط الويب التقليدية وحدها ليست كافية في بيئات Web3.
يجب أن يبدأ المبتدئين ببرامج عامة واضحة النطاق تكافئ التعلم الجيد بدلاً من السباق من أجل السرعة. توفر منصات مثل Intigriti و Open Bug Bounty بيئات داعمة.
يستفيد الباحثون الجدد من التدرب على المختبرات المعرضة للخطر عن قصد قبل الانضمام إلى البرامج الرئيسية. تؤدي كتابة إثبات واضح وقابل للتكرار للمفاهيم إلى تسريع نمو المهارات والموافقة على التقارير.
تعمل المكاسب الصغيرة على بناء الثقة وفتح الوصول إلى الدعوات الخاصة. الاتساق مهم أكثر من السعي وراء دفعات عالية مبكرًا.
يحدد برنامج الكشف عن الثغرات الأمنية (VDP) ما يمكن للباحثين اختباره وما هو محظور. يضمن الكشف المنسق عن الثغرات الأمنية (CVD) توصيل النتائج بمسؤولية إلى البائعين.
تتطلب بعض المنصات KYC لمعالجة المدفوعات أو الانضمام إلى البرامج الخاصة. يجب على الباحثين دائمًا قراءة قواعد البرنامج لتجنب الاختبار غير المصرح به.
توفر سياسات الملاذ الآمن الحماية القانونية عند العمل ضمن النطاق. تخلق هذه القواعد المساءلة والثقة المتبادلة بين الباحثين والمنظمات.
تختلف أوقات الفرز حسب النظام الأساسي، ولكن معظم البرامج الراسخة تقوم بمراجعة الطلبات في غضون أيام قليلة. غالبًا ما تقدم المنصات المُدارة استجابات أسرع لأن الفرق المخصصة تتعامل مع التحقق من الصحة.
من المتوقع وجود إثبات واضح للمفهوم لمعظم عمليات الإرسال لمساعدة المراجعين على تأكيد المشكلة بسرعة. تعمل POCs القوية أيضًا على زيادة معدلات القبول وتقليل الاتصال ذهابًا وإيابًا.
يمكن للمبتدئين أن يكسبوا، لكن التقدم الأولي بطيء أثناء تعلم المنهجية واكتساب جودة التقرير. تتحسن الأرباح مع نمو الخبرة وزيادة الدعوات إلى البرامج الخاصة.
يمكن لبعض الثغرات الأمنية التي تؤثر على البنية التحتية أو البرامج المستخدمة على نطاق واسع تلقي مهام CVE. عادةً ما تكون مشكلات الويب فقط غير مؤهلة لأنها تقتصر على التطبيقات الفردية.
يمكن رفض التقارير لأسباب مثل انخفاض الخطورة أو التكرار أو الاختبار خارج النطاق. تساعد مراجعة قواعد البرنامج وتحسين استراتيجية الاختبار على تقليل حالات الرفض بمرور الوقت.
تعتمد التصنيفات على المعايير التي تهم المتسللين الأخلاقيين، مثل جودة البرنامج وموثوقية الدفع وتجربة الباحث الشاملة. تمت مراجعة كل منصة لمعرفة كيفية أدائها في بيئات الاختبار الحقيقية بدلاً من كيفية تسويق نفسها.
تم إيلاء الاهتمام لاستجابة الفرز ووضوح القواعد ومعايير الاتصال عبر برامج متعددة. تساعد هذه العناصر في الكشف عن المنصات التي تدعم الباحثين حقًا وتلك التي تخلق احتكاكًا غير ضروري.
تم قياس كل منصة باستخدام سمات متسقة، مما سمح للمقارنات بأن تظل متوازنة وشفافة. يضمن هذا النهج أن التقييمات النهائية تعكس القيمة العملية وليس الافتراضات أو التحيز.
