🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
The benefits of a firewall include controlled network access, reduced exposure to cyber threats, protection against unauthorized connections, and improved visibility into network traffic. By filtering and regulating how data moves across network boundaries, a firewall lowers attack risk while keeping critical systems protected.
Beyond basic access control, firewalls provide operational advantages that directly strengthen security posture. They help block malware before it spreads, limit attacker movement through segmentation, and reduce the overall attack surface by restricting unnecessary services and ports.
Firewalls also deliver long-term value by enforcing security policies consistently and supporting data protection and compliance requirements. This combination of prevention, visibility, and containment makes firewalls essential for maintaining stable and secure modern networks.
Firewalls control which connection requests can interact with internal systems, stopping unauthorized access before it reaches the network perimeter. This prevents untrusted sources from entering protected environments, which commonly leads to system compromise.
With entry points clearly regulated, internal systems remain shielded from unapproved users. The result is a significant reduction in unauthorized access attempts.
Malware is most effective when it enters a network disguised as legitimate traffic, making early interception critical. Inspection at the network boundary helps stop malicious payloads before they interact with internal devices.
When harmful patterns are detected, malware is blocked by firewall controls before it can spread. This containment limits operational impact even during active attacks.
Repeated intrusion attempts target exposed network boundaries where access decisions are weak or inconsistent. Blocking these connection requests prevents attackers from establishing an initial foothold.
By denying untrusted connection requests, a firewall prevents intrusions at the perimeter. Repeated attack paths lose effectiveness over time.
Lack of traffic visibility allows threats to move unnoticed across network paths until damage is already done. Continuous inspection provides insight into traffic sources, destinations, and access behavior.
Logs and alerts generated through firewall monitoring make abnormal activity easier to spot. Earlier detection allows faster response before incidents escalate.
Unrestricted network access is a leading cause of accidental data exposure and unauthorized data movement. Restricting communication paths ensures that critical systems are not exposed unnecessarily.
Unauthorized data movement is blocked when firewall rules limit access to approved users and applications. This helps preserve confidentiality and information integrity.
Exposed services and open ports significantly increase attack surface and exploitation risk. Reducing these entry points limits how attackers can interact with the network.
By restricting access paths, a firewall makes exploitation more difficult. Fewer available targets directly translate into lower risk.
Inconsistent policy enforcement creates security gaps that attackers actively exploit. Automated enforcement ensures rules are applied uniformly across all traffic paths.
Once defined, policies are applied consistently through firewall mechanisms. This eliminates gaps caused by configuration errors or oversight.
Lateral movement becomes possible when internal network segments communicate freely. Separating environments limits how far an attacker can move after initial access.
Communication between segments is controlled using firewall-based segmentation. If one area is compromised, the damage remains contained.
Uncontrolled traffic flows often lead to performance degradation and service disruption. Managing which connections are allowed helps maintain predictable network behavior.
System stability improves when disruptive connections are filtered by firewall controls. Networks operate more reliably under managed traffic conditions.
Regulatory failures frequently stem from insufficient access controls and missing activity records. Enforcing traceable network controls reduces regulatory exposure.
Audit readiness improves when firewall logging and access restrictions are in place. Compliance risks are reduced through sustained control and visibility.
Firewalls prevent cyber attacks and malware by controlling traffic at the network boundary, where most threats attempt to gain entry.
Protecting sensitive information depends on controlling how data flows across network boundaries and internal paths.
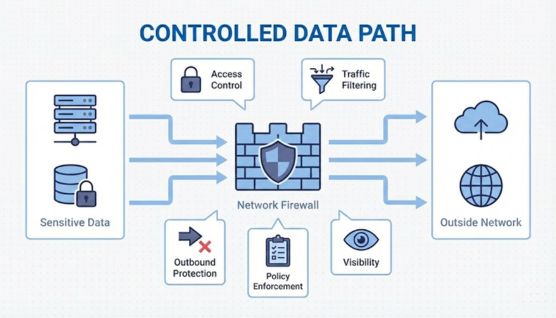
Excessive network reachability is a primary cause of unintended data exposure. Limiting access paths ensures sensitive systems are reachable only where operationally necessary.
Unregulated data movement increases the risk of data appearing in unsecured environments. Defined routing and filtering rules keep sensitive information within approved network paths.
Most data breaches involve unauthorized outbound transfers rather than inbound theft. Restricting outbound connections prevents sensitive data from leaving the network unnoticed.
Data policies fail when enforcement is inconsistent across network segments. Applying rules at the network layer ensures data handling standards remain uniform.
Undetected data movement creates blind spots that delay breach discovery. Network-level inspection reveals abnormal flows that may indicate exposure or misuse.
No security control can stop every cyber attack on its own. Firewalls significantly reduce risk by controlling network access, traffic paths, and exposure points, but they work best as part of a layered security approach.
Yes, network-level controls remain essential even in cloud and zero-trust environments. Firewalls continue to regulate traffic paths, enforce segmentation, and reduce attack surface across hybrid infrastructures.
Firewalls are not designed to stop all insider activity, but they limit unnecessary access and monitor abnormal traffic patterns. This reduces the risk of accidental exposure and restricts how far misuse can spread.
Without a firewall, network traffic flows without structured control or inspection. This increases exposure to unauthorized access, malware entry, and data leakage risks.
When properly configured, firewalls improve stability by filtering unnecessary and malicious traffic. Performance issues usually result from misconfiguration rather than the firewall itself.
