🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد



.jpg)
الفئة: استخبارات الخصم
الصناعة: متعددة
المنطقة: عالمي
التحفيز: الشؤون المالية
أعلى: كهرمان
تستغل الجهات الفاعلة في مجال التهديد بنشاط رؤوس HTTP المفقودة «X-Frame-Options» لتشغيل حملات التصيد الاحتيالي التي تستهدف شركات متعددة على مستوى العالم. وقاموا بتضمين نطاقات الشركات في إطارات iframe وتغطيتها بلوحات تسجيل الدخول المخادعة لجمع بيانات الاعتماد.
تضمن مخطط التصيد الاحتيالي تحميل نطاق الضحية داخل إطار iframe وعرض لوحة تسجيل دخول مزيفة في الأعلى. أدخل الضحايا بيانات اعتمادهم دون علمهم في هذا التراكب، والتي تم إرسالها بعد ذلك إلى المهاجمين عبر روبوت Telegram باستخدام رمز API المشفر ومعرف الدردشة على صفحة التصيد الاحتيالي.
تتضمن عمليات التخفيف تعيين 'خيارات الإطار X«عنوان HTTP إلى»أنكر'أو'نفس الأصل'، تنفيذ سياسة أمان المحتوى باستخدام'أسلاف الإطار«التوجيه، باستخدام البرامج النصية لخرق الإطارات، وتطبيق»نفس الموقع'السمة إلى ملفات تعريف الارتباط، وفرض أمان النقل الصارم لـ HTTP (HSTS)، وتنفيذ المصادقة متعددة العوامل (MFA).
اكتشفنا صفحة تصيد تستهدف شركات متعددة. أدت زيارة صفحة الويب إلى تزويد الضحايا بلوحة تسجيل دخول على الصفحة. عنوان URL لصفحة التصيد الاحتيالي هو: hxxp [://] web-auth-ver-micha [.] hb [.] ru-msk [.] vkcs [.] السحابة/ترينيتي - ب [.] html #victim_email @victim_domain [.] com
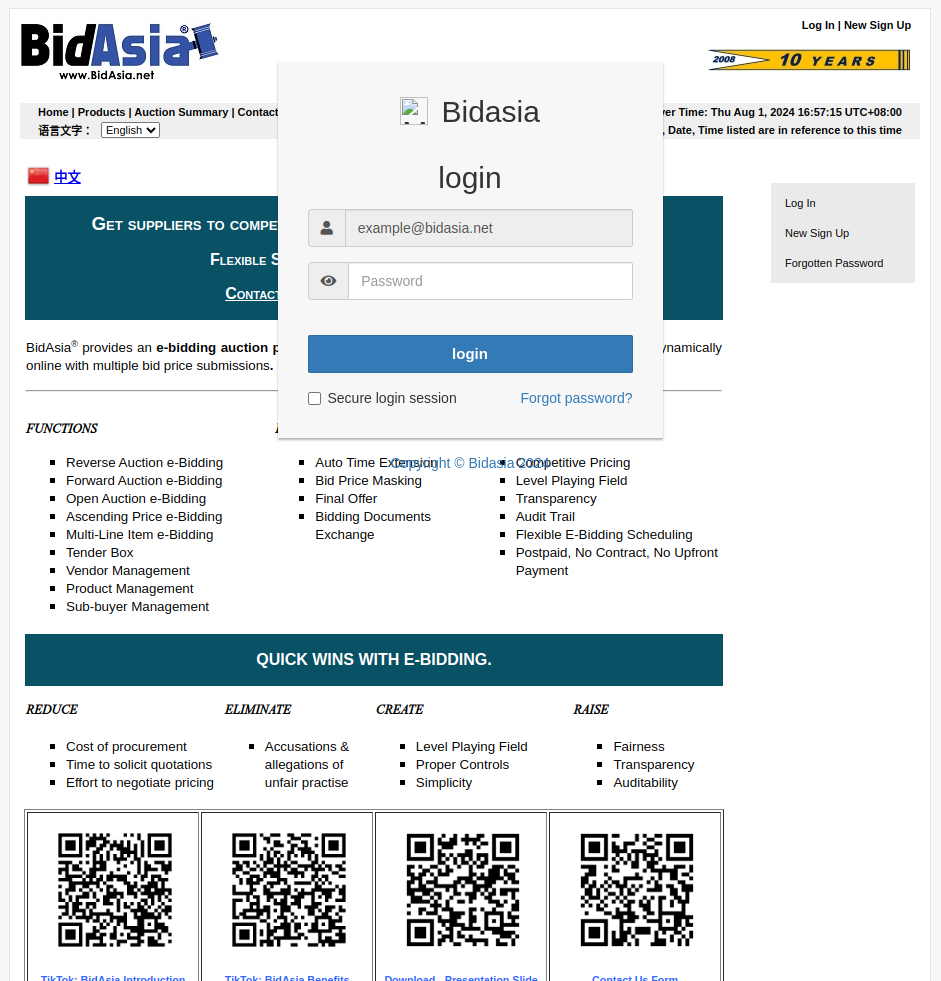
من خلال إلقاء نظرة على الكود المصدري لصفحة الويب المخادعة، كان من الواضح أن الصفحة تقوم بتحميل النطاق الموجود في البريد الإلكتروني للضحية باستخدام إطار iframe. علاوة على ذلك، قامت بتحميل صفحة تسجيل الدخول الخاصة بها والتي سمحت للضحايا بإدخال بيانات اعتماد تسجيل الدخول. وبالتالي، من الواضح أن صفحة التصيد الاحتيالي كانت تسيء استخدام مواقع الويب التي لم تقم بتعيين خيارات X-Frame-Options.
<iframe><embed><object>يمكن استخدام رأس استجابة HTTP لـ X-Frame-Options للإشارة إلى ما إذا كان ينبغي السماح للمتصفح بعرض صفحة في أو <frame>أو. يمكن للمواقع استخدام هذا لتجنب هجمات النقر، من خلال ضمان عدم تضمين محتواها في مواقع أخرى.
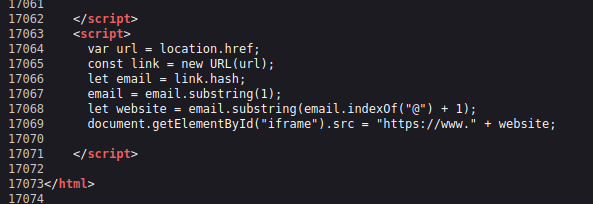
بمجرد إدخال الضحية بيانات الاعتماد على لوحة تسجيل الدخول الخاصة بالمهاجم أعلى إطار iframe، تم إرسال بيانات الاعتماد إلى روبوت التلغرام عبر واجهة برمجة تطبيقات التلغرام. لهذا الغرض، كان لدى الجهات الفاعلة في مجال التهديد رمز واجهة برمجة تطبيقات التلغرام المشفر ومعرف الدردشة الذي سمح بإرسال البيانات إلى روبوت برقية يتحكم فيه المهاجم.
نظرًا لأن مواقع الويب التي استهدفها المهاجمون كانت تفتقد رأس HTTP لـ X-Frame-Options، فقد أتاح ذلك تحميل مواقع الويب هذه في إطار iframe مما يجعلها عرضة للنقر!
بمجرد حصولنا على رمز البرقية ومعرف الدردشة، تمكنا من التخلص من جميع أوراق الاعتماد التي جمعها ممثل التهديد حتى الآن على جميع الضحايا.
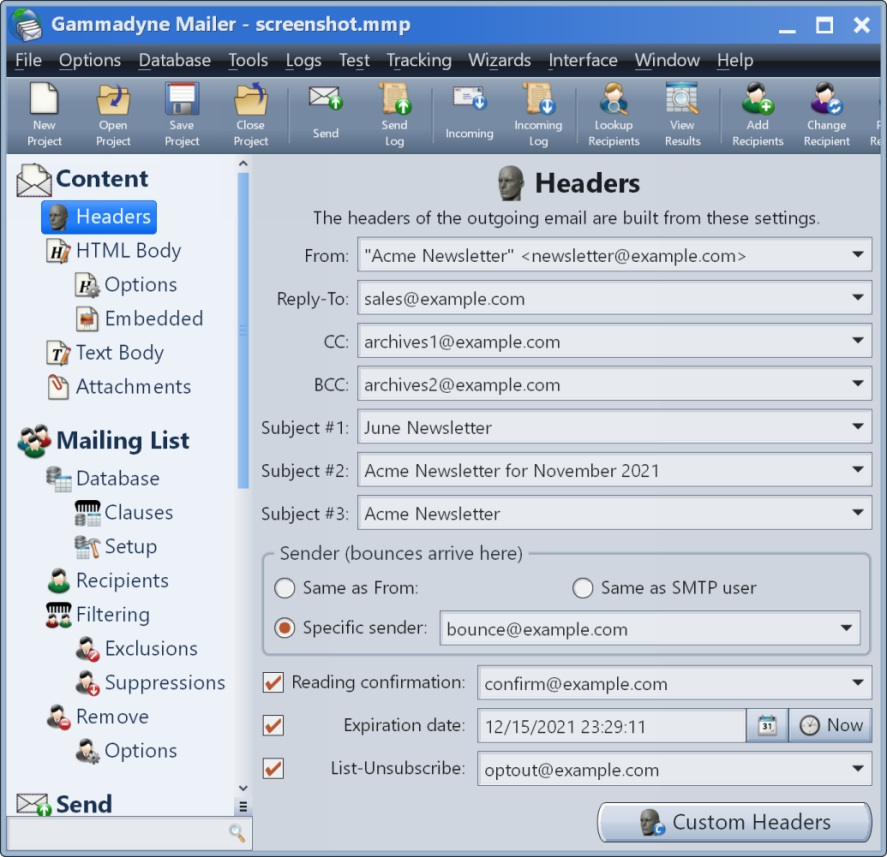
من البيانات التي تمكنا من تفريغها من روبوت التلغرام حتى 31 يوليو 2024، وجدنا 1,262 ضحية حتى الآن. هؤلاء هم المستخدمون الذين نقروا على صفحة التصيد الاحتيالي وقدموا بيانات اعتمادهم. علاوة على ذلك، فإن النطاق الأكثر استهدافًا هو موقع دوتش مانوز الكبير وهي شركة دواجن مقرها في الولايات المتحدة الأمريكية.
متبوعة بـ globalnapi.com وهي شركة أدوية في مصر. indexcargologistics.com هو المجال الثالث الأكثر استهدافًا وهو شركة الخدمات اللوجستية والنقل في نيروبي، كينيا.
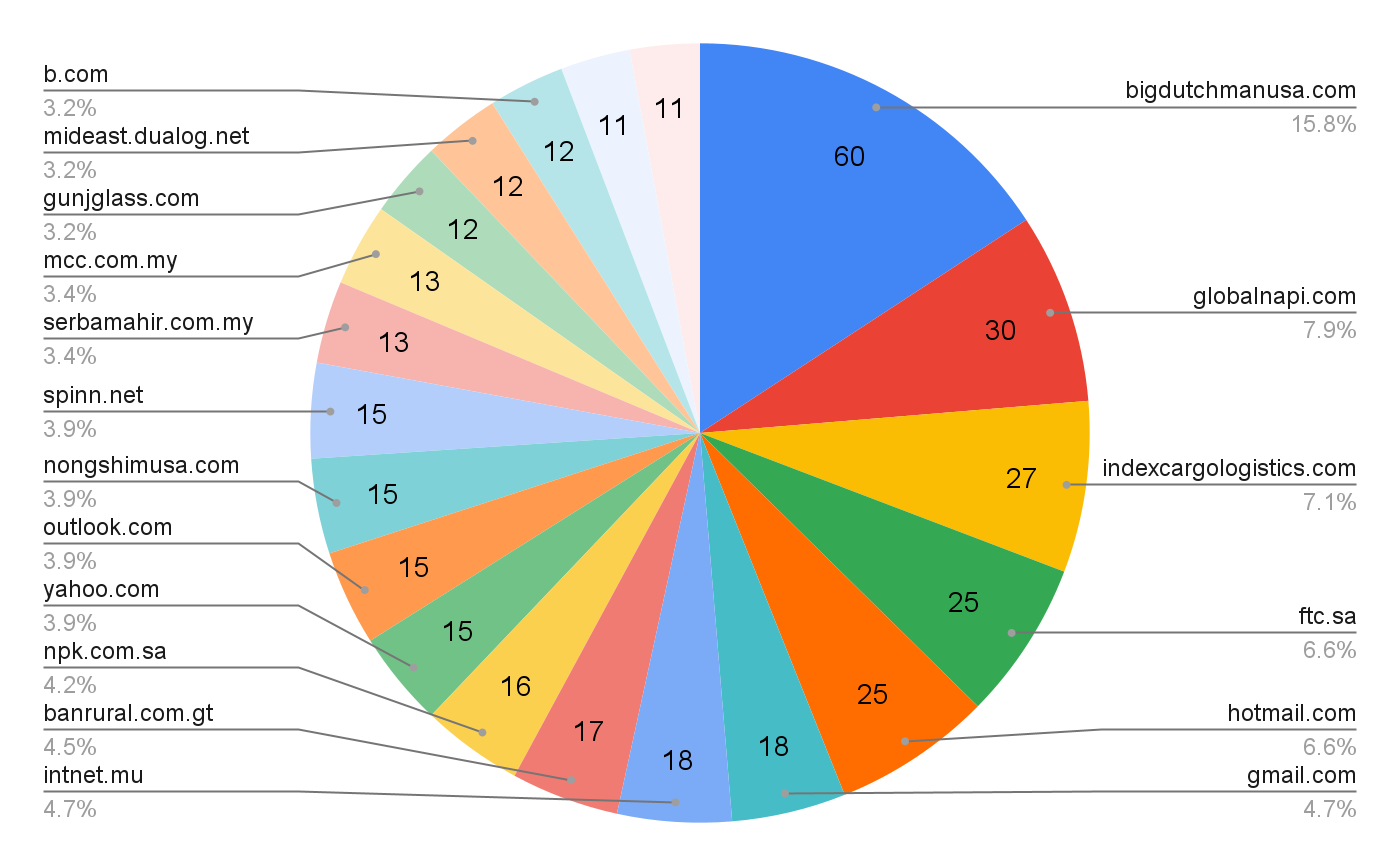
من HUMINT، علمنا أن ممثل التهديد يستضيف بعض صفحات التصيد الاحتيالي المستضافة على VK Cloud و firebase. تقوم هذه الصفحات بتحميل إطار iframe من البريد الإلكتروني المذكور في عنوان url، أي إذا كان عنوان URL المخادع هو https://phishing.url/phishing.html#victim_email@victim_domain.com ثم سيتم تحميل vitic_domain في إطار iframe. علاوة على ذلك، ستكون هناك لوحة تسجيل دخول أنشأها المهاجم.
بمجرد أن يقوم الضحية بإدخال بيانات اعتماده في لوحة تسجيل دخول المهاجم، يتم إرسالها إلى برقية عبر واجهة برمجة تطبيقات التلغرام المضمنة في صفحة الويب. لهذا الغرض، كان روبوت البرقية الذي قاموا بإنشائه يسمى «MichaMicha». يمكن للمهاجمين بعد ذلك التحقق من صحة بيانات الاعتماد من هناك.
علاوة على ذلك، اكتشفنا عبر HUMINT أيضًا أنه من أجل نشر هذه النطاقات المزيفة، يستخدم ممثل التهديد أدوات مثل Sendgrid أو «PowerMTA SMTP Server» أو «Gammadyne Mailer». تسمح هذه الأدوات لممثل التهديد بإرسال رسائل بريد إلكتروني احتيالية متعددة إلى معرفات بريد إلكتروني مختلفة دفعة واحدة.
باستخدام رمز الروبوت والمعرف المضمنين في صفحة الويب الخاصة بالتصيد الاحتيالي، تمكنا من إعادة توجيه جميع الرسائل من الروبوت إلى دردشة التلغرام الخاصة بنا مع الروبوت. كانت الرسالة الأولى من مقبض التلغرام الخاص بالمهاجم: @غرفة التحكم 1717.
اسم مستخدم Telegram للبوت الذي تستخدمه الجهات الفاعلة في التهديد هو: @ميشاميتشابوت.
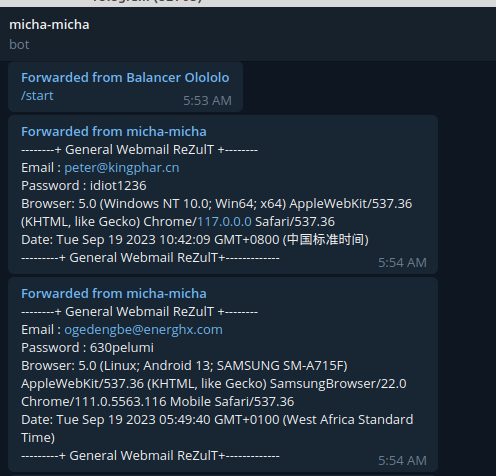
باستخدام HUMIT، تعرفنا أيضًا على أن المهاجم موجود في نيجيريا حيث تم إنشاء حساب Telegram باستخدام رقم هاتف محمول نيجيري.
تمكنا أيضًا من الحصول على مثيل آخر من firebase للتصيد الاحتيالي يستخدمه ممثل التهديد لاستضافة مواقع التصيد الاحتيالي التي تستهدف Naver Works وهي شركة كورية.
عنوان URL الخاص بالخداع الاحتيالي في Firebase: hxxps [://] تخزين قاعدة البيانات [.] googleapis [.] com/v0/b/vccv-f1c96 [.] appspot [.] com/o/%eb%b 0% 94% 20% EB%8B 9% EC% EC%9D 98% 98% 20% EC%A 1% B 0% EC%B 9% 98% 20% EA%B 2% B 0% EA%B 3% BEC%A 5% قبل الميلاد [.] html؟ alt=وسائل الإعلام والرمز = da7594e4-02c5-499b-a040-8 f17695f6286
للتخفيف من خطر النقر، حيث يقوم ممثل التهديد بتحميل نطاق الشركة في إطار iframe وتثبيته بلوحة تسجيل دخول احتيالية، يمكن تنفيذ العديد من الاستراتيجيات:
إذا (أعلى موقع!) = الموقع الذاتي) {
الموقع العلوي = self.location.href؛
}