Get visibility and protection from the risks and vulnerabilities caused by your third party vendors.

Source: IBM Cost of a Breach Report, 2023







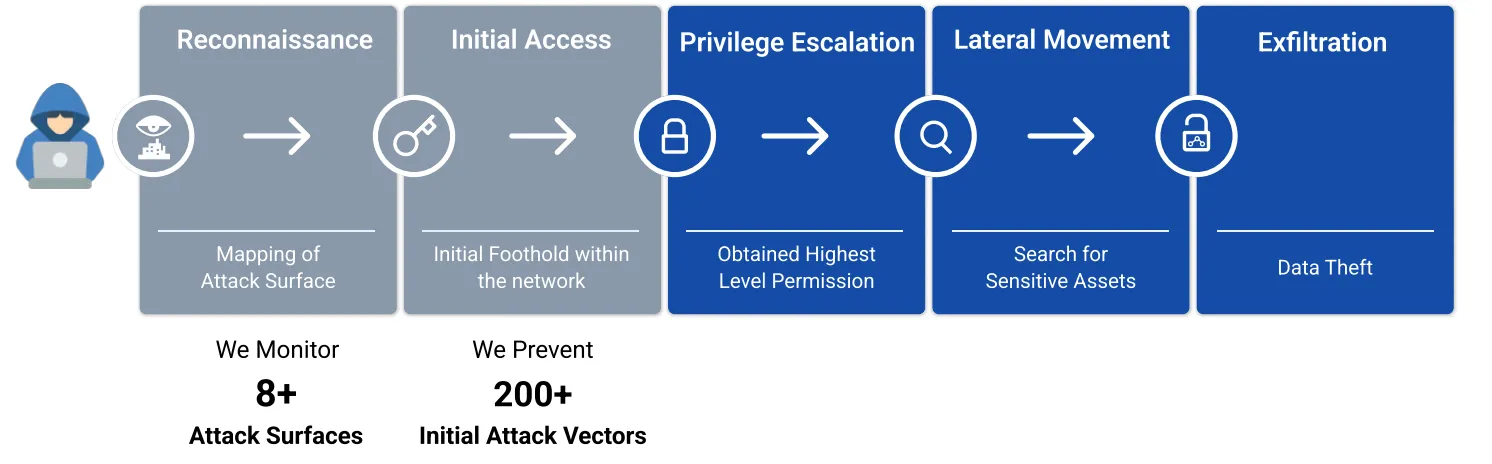
CloudSEK stops the Kill Chain by predicting and preventing Initial Access Vectors
In a digital world where threats evolve daily, your business needs a shield against unseen dangers. Learn how our Digital Risk Protection (DRP) solutions offer comprehensive monitoring and defence against digital threats. Transform your online presence into a fortress with our innovative strategies.
Hence, it s absolutely necessary that the attackers are stopped before they can gain initial access within the network.
CloudSEK stops the kill chain attackers follow even before they can gain an initial foothold within the network. We do this by mapping customers attack surfaces and all IAVs commonly used by threat actors. Killing the IAV would prevent a cyber threat from happening.
At CloudSEK, we combine the power of Cyber Intelligence, Brand Monitoring, Attack Surface Monitoring,
Infrastructure Monitoring and Supply Chain Intelligence to give visibility and context to our customer's IAVs.
Our advanced platform diligently scrutinizes the potential security vulnerabilities and risks from external suppliers and vendors.
Actively monitors and evaluates risks from established vendors, safeguarding against vulnerabilities in the organization's supply chain.
Thoroughly assesses and manages risks associated with external software usage, ensuring robust protection against potential security threats."


Cyber threats like data breaches and ransomware can disrupt business, compromise data, and damage reputations. Understanding the importance of vendor risk monitoring is crucial in countering these cyber threats.
Collaborating with multiple vendors expands an organization's attack surface, making each vendor a potential entry point for cyber attacks. Regular monitoring of vendors helps identify and mitigate vulnerabilities before they're exploited
A cyber breach in a vendor's system can expose sensitive info, lead to intellectual property theft, or disrupt services. Continuous monitoring is key to ensuring vendor security standards.
Cyber attacks increasingly target the supply chain, with compromised vendors spreading threats. Swift detection of these risks hinges on effective supply chain monitoring
Industries facing regulations like GDPR or HIPAA can be liable for vendor breaches. Proactive monitoring ensures vendor compliance, reducing legal and financial risks.
Regular vendor monitoring keeps organizations abreast of evolving cyber threats, vulnerabilities, and attack methods, enabling proactive risk mitigation.
Regular monitoring of vendors enhances early threat detection, crucial for effective response and minimizing impact in vendor-related security incidents.
SVigil platform evaluates the security vulnerabilities and risks posed by external suppliers and vendors, ensuring that your organization's products and services remain secure and reliable.
